The Silo Web Isolation Platform is a secure, cloud-native execution environment for all web-based activity. Silo is built on the principles that all web code and critical data should be isolated from the endpoint, and that browsing capabilities should be like any other enterprise workflow — configurable and auditable.


isolation from all web code, regardless of device or network
secure and anonymous page views since launch
data loss events or identity leaks in 10 years of operation
A cloud-based solution that deploys in seconds — whether it’s for a single user or thousands. Silo doesn’t require infrastructure investment; its ability to easily scale lets IT focus on solving business problems, not managing procurement. And Silo can be delivered as a distinct browser or seamlessly integrated into the existing browser using APIs allowing IT to deliver the most appropriate user experience.
Unlike more traditional security solutions that require synchronizing software across endpoints, integrating with network infrastructure and piping disaggregated logs into a unified system, Silo lets you deploy across your user population with a click of a button. Silo can scale up and down as your needs change, allowing you to deliver the right solutions for your users at the right time.
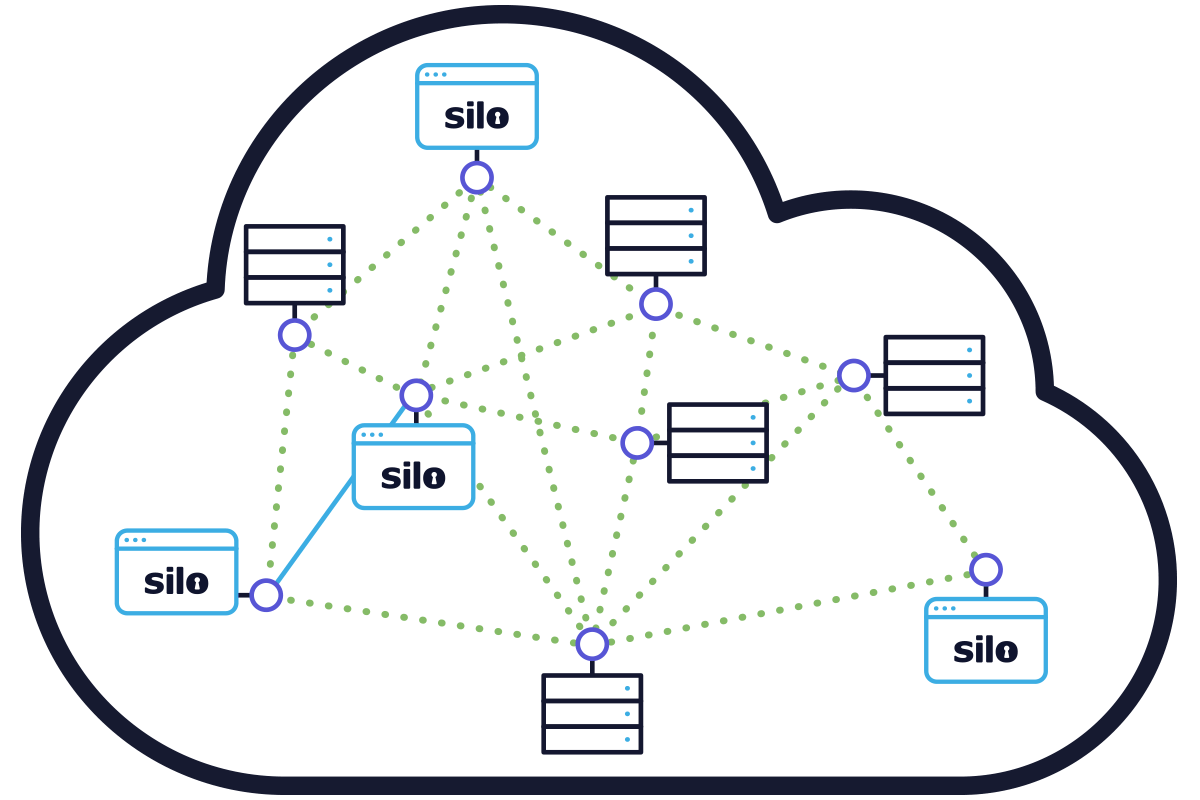
A robust user/group and policy framework ends the tyranny of one-size-fits-all. Silo lets you define access, authentication and use policies across users and organizations. Whether you want a throwaway browser for personal use or a locked-down environment for a sensitive workflow, Silo gives IT unprecedented control over how the web is used.
Silo can be tuned to meet the fluid needs of your organization. Define policies centrally and rest assured that they follow the user across devices and locations.
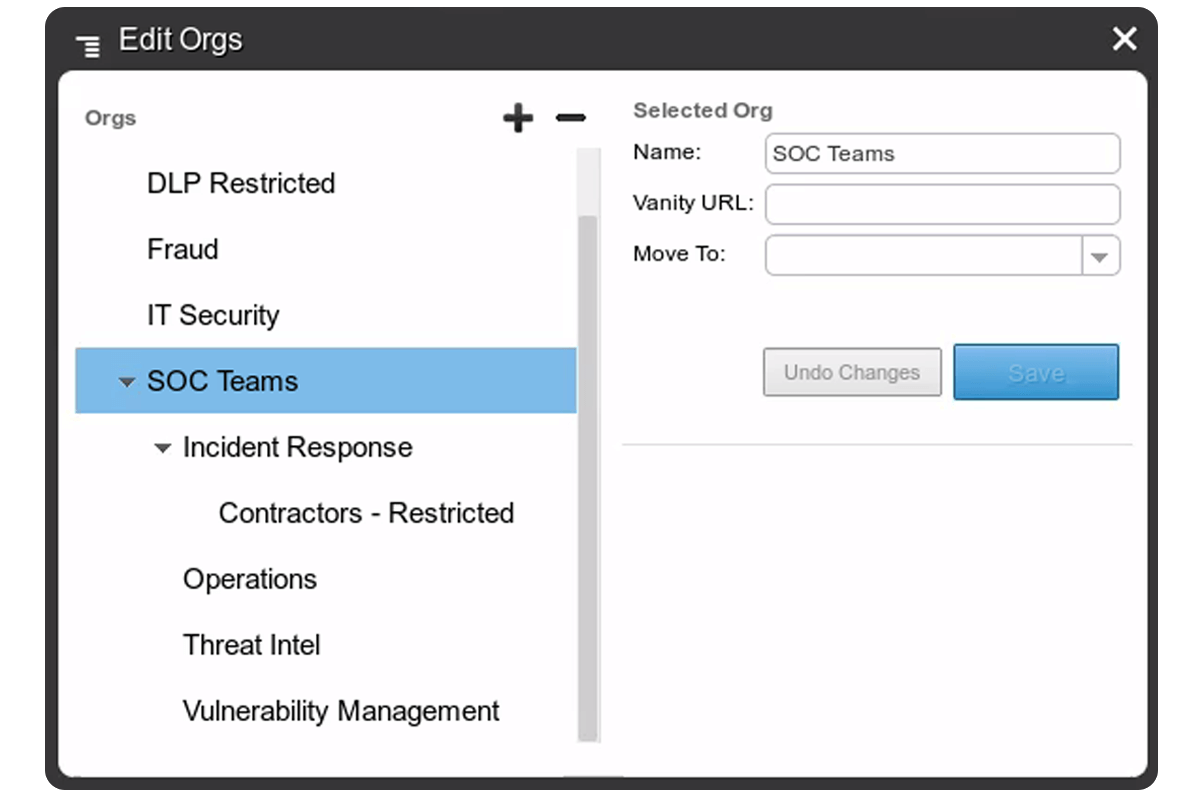
From directory services to identity management platforms, secure web gateways and SIEM solutions, Silo plays nicely with your current IT technology stack. Silo can also act as a completely standalone environment and execute outside your organization's infrastructure (e.g., when working with third-party contractors/suppliers/partners or BYOD employees).
Silo matches your organizational structure as defined in your on-premises directory service. If you're using an identity management platform, third-party SAML or other cross-authentication solutions, they can be used to authenticate users when they access Silo, and for single-click access to provisioned web applications.
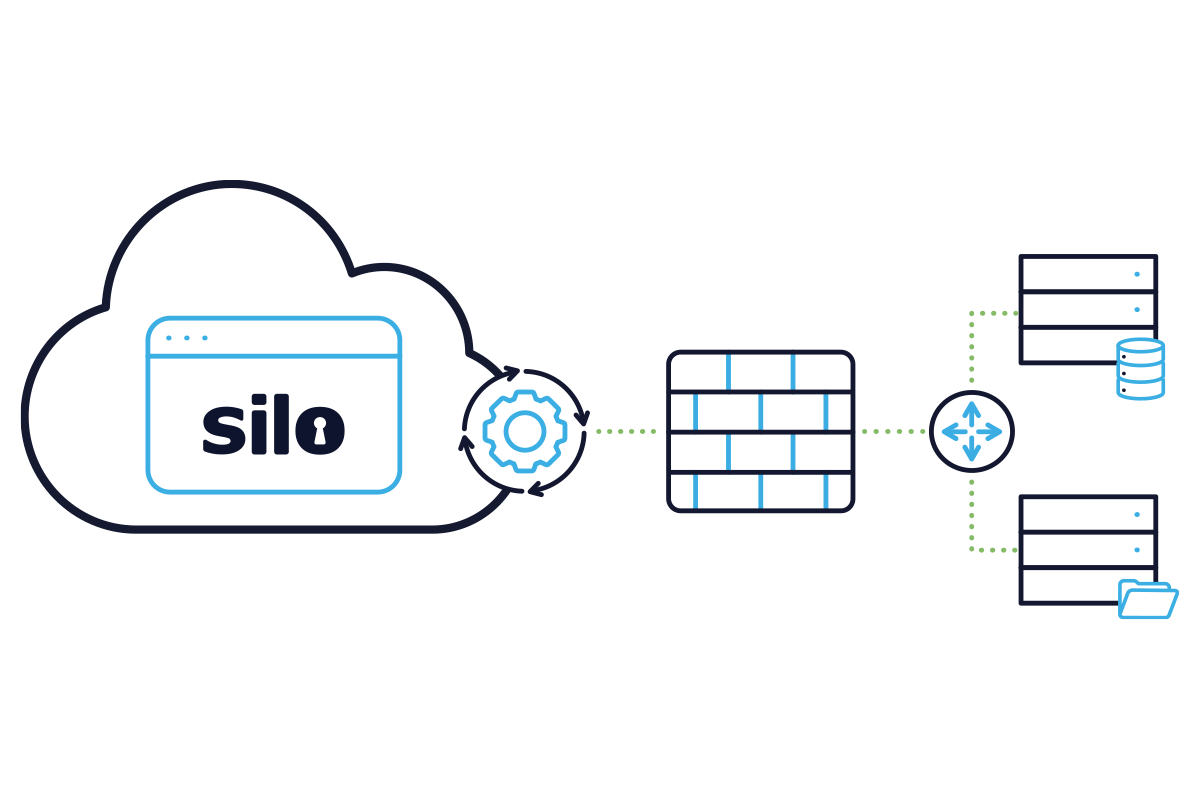
Silo meets the needs of the most regulated organizations in the world, from federal agencies to Swiss banks to healthcare providers. All data is encrypted and protected to the highest standards. And Authentic8 undergoes regular third-party audits and assessments to remain compliant with FedRAMP, PCI, HIPAA, SOC2 and more global standards.
Platform security is an intrinsic value at Authentic8. Whether pursuing our own compliance with global security standards like NIST and ISO, meeting specific industry requirements or delivering a solution to help our customers meet their compliance requirements, Silo is built from the ground up with information security in mind. With SIlo, you control how much customer-identifying information is stored in the system. Silo encrypts log data with keys managed by the customer, and it provides APIs to extract and pipe data into third-party analysis tools. We also provide APIs to extract your data should you decide to stop using the service. See our Certifications page for more detail.

Cybersecurity intelligence
LEARN MOREIntelligence and Evidence Gathering
LEARN MOREFinancial Crime and Compliance
Learn MoreTrust and Safety
learn moreFraud and Brand Misuse
LEARN MORECorporate Research and Protection
LEARN MOREThird-party application access
LEARN MOREBYOD application access
LEARN MORESecure application workspace
LEARN MOREUntrusted website access
LEARN MOREPersonal browsing
LEARN MOREEnterprise browser
LEARN MORE