
Traditional online investigations risk exposure and loss of control when accessing sensitive or adversarial content. Silo Workspace is a cloud-based, multi-application platform that puts you in-region with the tools you need to track leads across networks, websites, and apps.
Each on-demand workspace is regionally configured and equipped with the tools and persistence you need to conduct long-standing investigations, giving access to network resources, user forums, and other content sources. And Silo provides comprehensive policy control with full audit and oversight to ensure proper use and regulatory compliance.
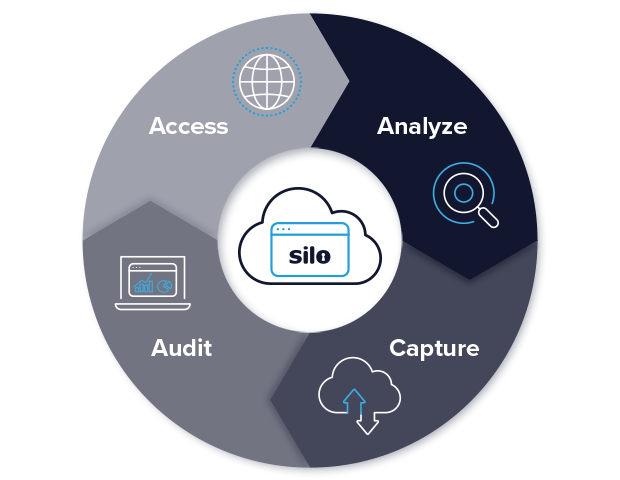


Silo Workspace adapts to your investigations, from a single in-region research browser to a full suite of applications for cross-platform access and data analysis. Tailor each workspace to your needs, whether your investigation calls for passive collection or active, persona-based engagement. Spanning the open, deep, and dark webs, Silo Workspace enables secure content collection and analysis without exposing you or your mission.
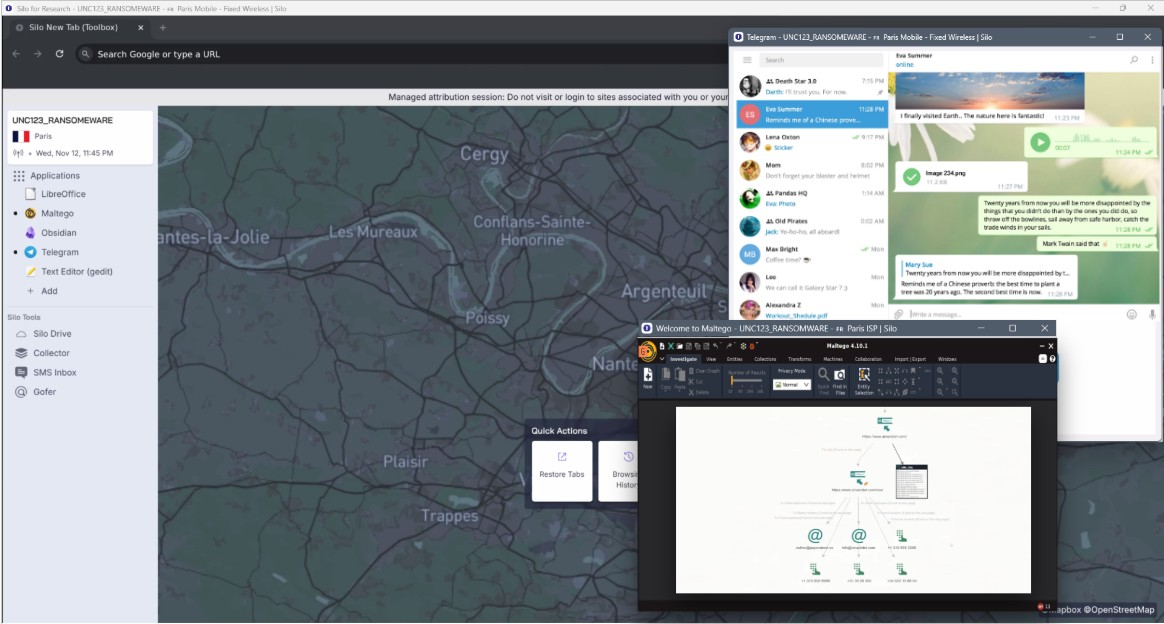
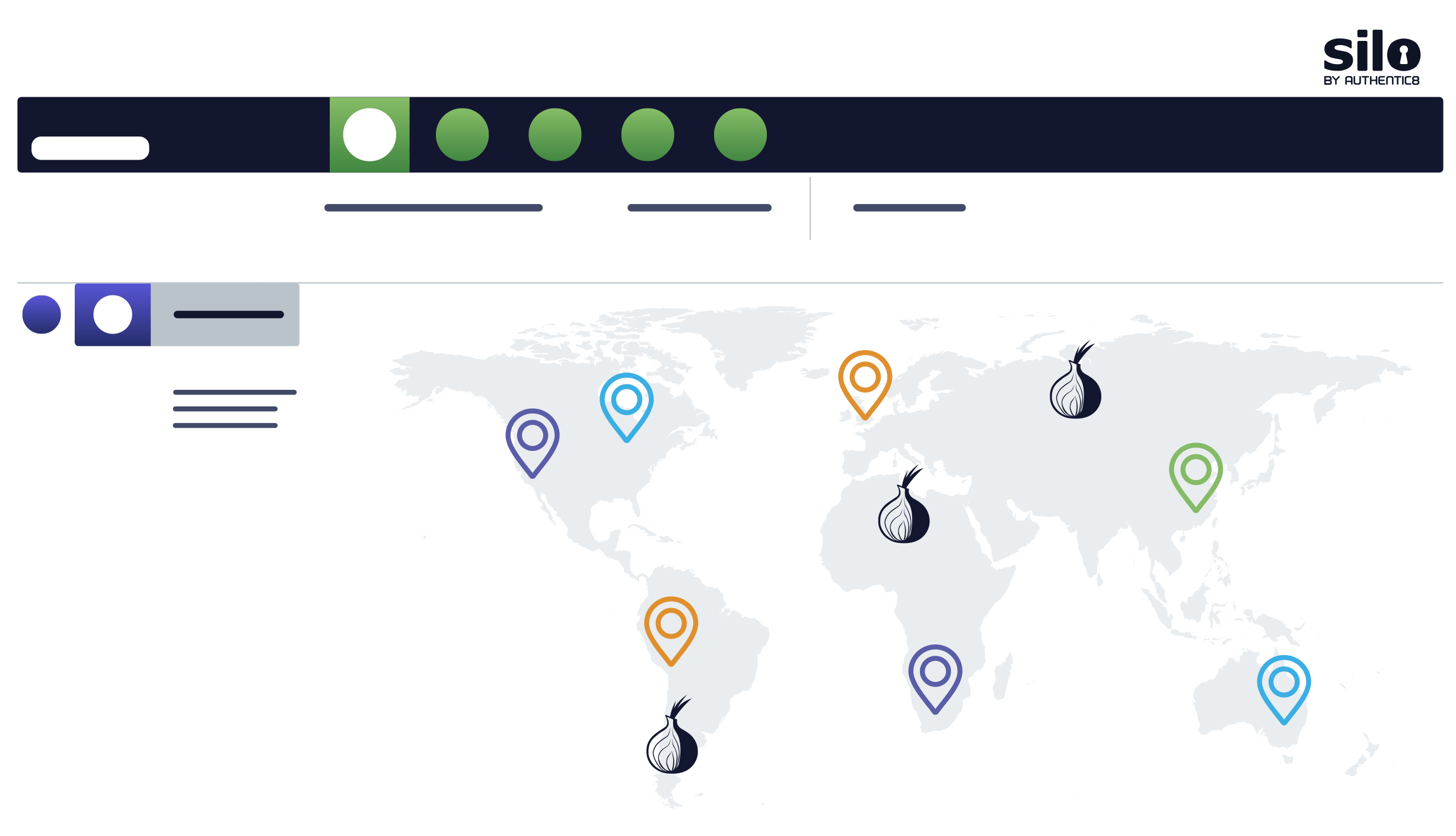
Silo Workspace creates secure, cloud-based environments that enable you to span regions, languages, networks, and protocols to reach content, applications, and forums for your investigation. Match your digital footprint to the location and blend in with the crowd. You can configure your persona for dark web access and safely extract the critical content your investigations require.
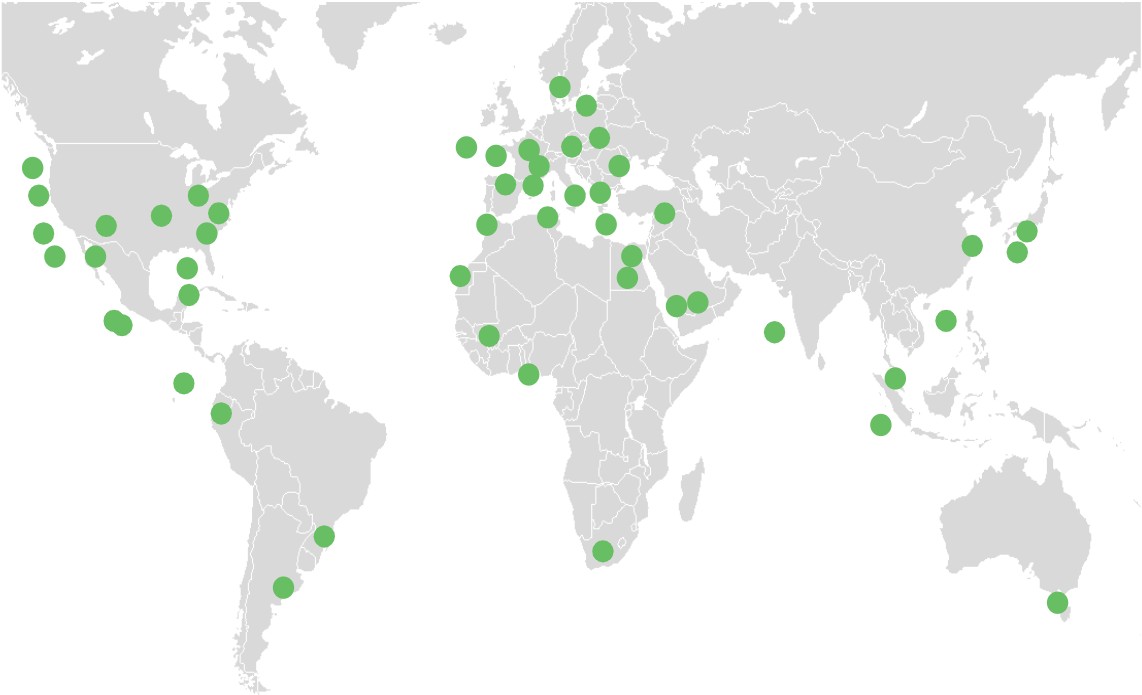
Built on the Silo Managed Attribution (MA) Network, Silo Workspace leverages more than 700 owned and operated endpoints across 32 countries to provide authentic, regionally diverse access. This network offers last-mile routing through local ISPs and mobile providers and Tor interconnects for dark web investigations. The Silo MA Network overcomes modern challenges like AI scrapers and anti-bot defenses, ensuring researchers maintain reliable access to online content.
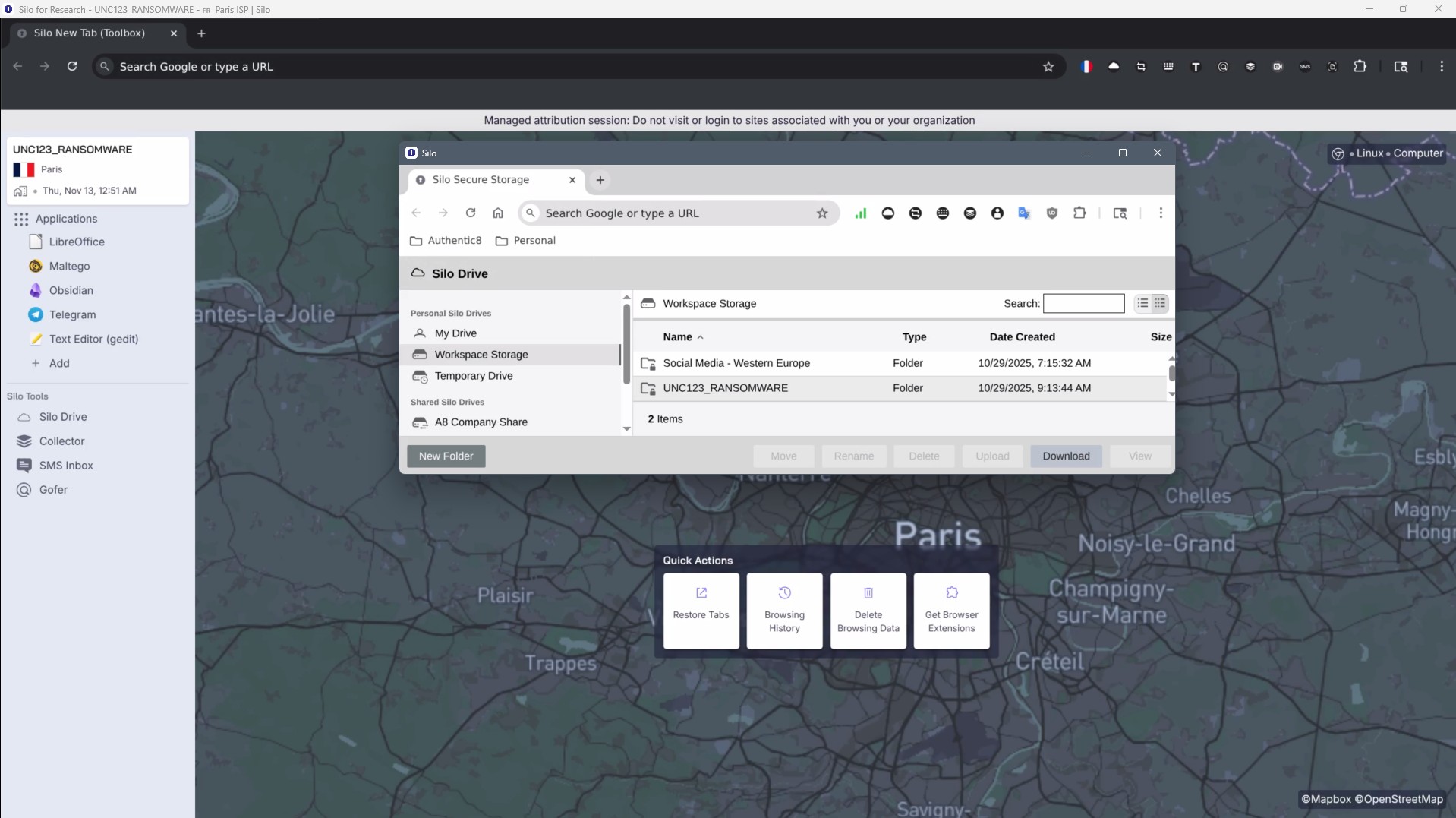
Collecting and preserving digital evidence requires secure handling, collaboration, and compliance. Silo Drive provides encrypted, cloud-based storage integrated across Silo Workspaces, enabling you to share, stage, and preserve data —all while maintaining chain of control and evidentiary requirements. Silo Drive keeps your investigation data protected, compliant, and ready for extraction or integration.
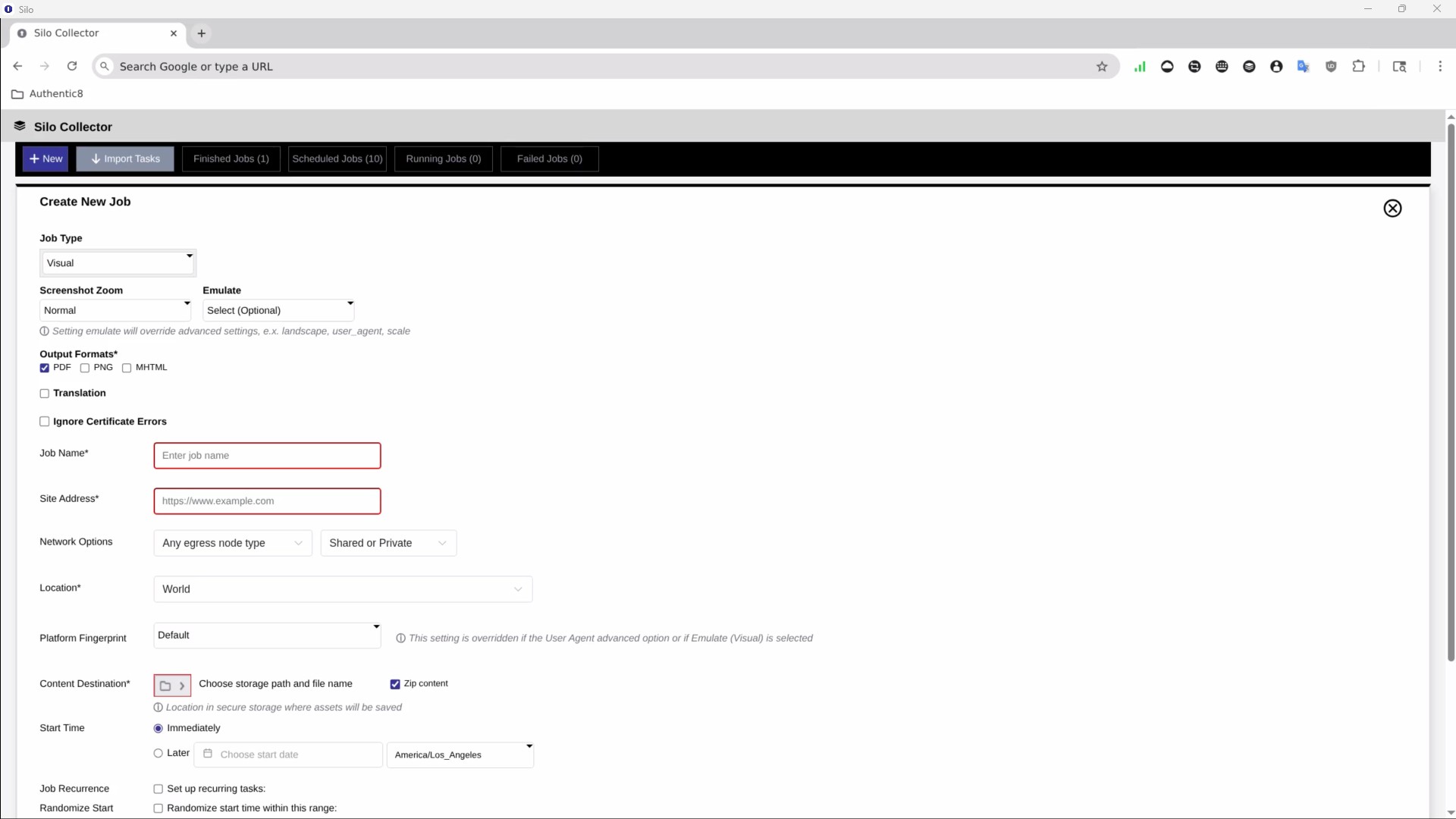
Silo Workspace enables direct, secure engagement with counterparty sites or individuals across the web and applications. When investigations require ongoing monitoring, Silo Collector automates routine content access, assessment, and extraction, from screenshots to media assets. Jobs run autonomously across the Silo MA Network with all captured data stored in time-stamped Silo Drive folders to preserve a historical record of target sites.
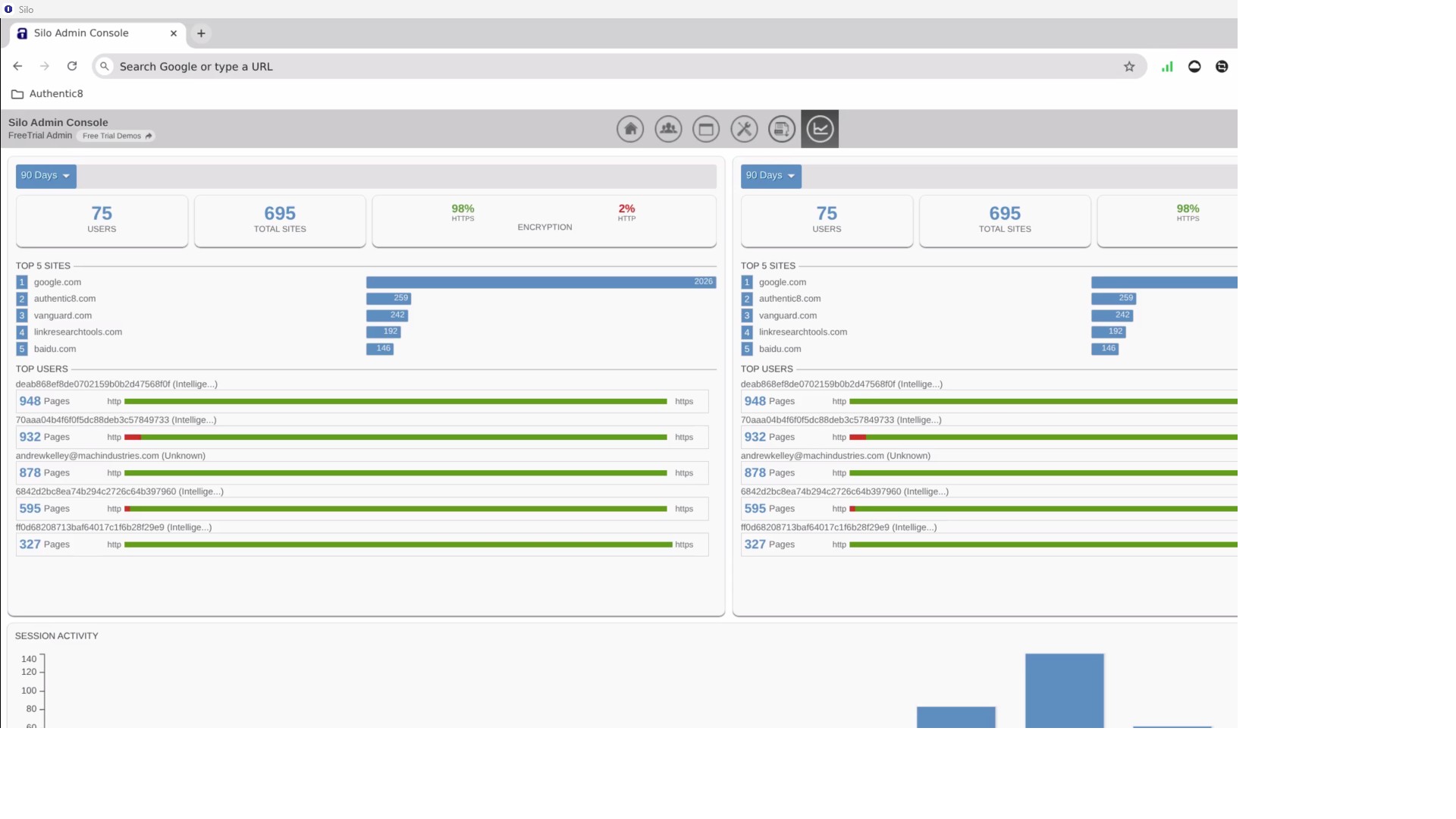
Silo Workspace is built for flexibility, supporting diverse investigative needs while giving admins full control. Admins can centrally grant or revoke access; define tools, regions, and persistence settings; and enforce governance through customizable policies. All user activity is logged and encrypted with customer-managed keys while APIs enable seamless integration with enterprise systems for user management, orchestration, and analysis.
Today’s threat actors advance their skills at warp speed — and so should defenders. Silo Training provides tradecraft education for all types of users, from executives who need to minimize their digital profile to experienced research analysts who conduct deep investigations across the dark web.




With Silo Workspace's managed attribution functionality, you can completely customize how you appear to sites and the people you interact with online. Manipulate a variety of your device details including language, time zone and keyboard settings, as well as the browser, OS and other elements. Appear to be browsing from any of Authentic8's dozens of global egress nodes, and show a local IP address that never refers back to you or your organization.
Yes, dark web access is seamlessly integrated within Silo Workspace and its suite of analyst tools. You do not need a separate, standalone dark web browser. This integration provides investigators with full isolation from dark web cyberthreats (e.g., malware-laden sites, forums, marketplaces) and anonymity from counter-surveillance efforts utilized by malicious actors.
Yes, Silo integrates with Authentic8 Secure Storage, an encrypted, audited and cloud-based storage repository for users and groups. Investigators may be required to capture and collect content as part of their process. And to maintain efficacy of potential evidence, a proper chain of control and evidentiary requirements must be met.
Collected data needs to be logged, attributed to an analyst and checked for validity. Chain of custody protections are critical to proper collection. When using Silo collection tools — whether manual or automated — all aspects of the process are logged and available for post-facto review.
Yes, Silo is a FedRAMP-authorized service. It has been assessed and approved as a cloud service offering (CSO) that meets the stringent security requirements to process, store and transmit federal government data.