Transparently wire isolation into workflows to protect data from untrusted — potentially compromised — devices and networks.
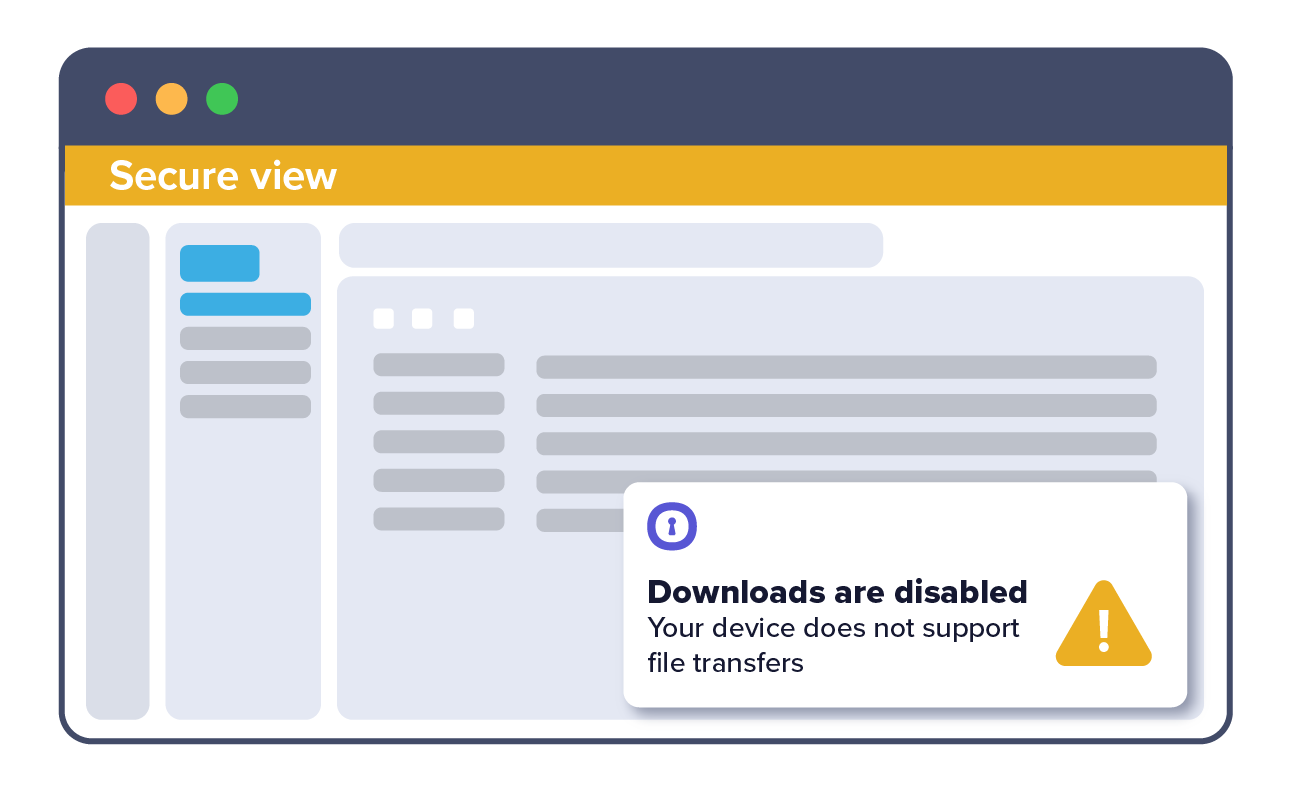
Constrain app access and data transfer based on the context of the access scenario: user, device, location or risk posture.
Rapidly deploy to third parties and BYOD employees without a software download or disrupting user workflows.

Enable third-parties rapidly while maintaining access and data control, and isolating risk.
Give distributed workers the app access they need without cyber or data leakage risks.
Isolated, centralized environment and data transfer control for sensitive apps.
Unmanaged devices present “last-mile” vulnerabilities and uncontrolled access to business data. Traditional security controls don’t apply or are dependent on users downloading software. You need a flexible, cloud-native solution to deploy where you need it when you need it — instantly.

Restrict application access for third-parties like contractors and suppliers, and remote or BYOD workers to control data transfer with precision. Empower IT to enforce access rules — to whomever has access to their data and:
Zero-trust shouldn’t mean shipping laptops across the globe, cumbersome setups and towering IT stacks. Silo delivers zero-trust access with speed, simplicity and cloud-native scalability.
