Did you know that ISPs can use VPN to spy on you? Third parties taking advantage of your VPN’s many flaws for nefarious purposes. We explain how they do it.
Large-scale privacy violations on the web have become commonplace. Social media platforms and app or service providers have been shelling out, some intentionally, others unintentionally, user data to third parties hand over fist.
While such incidents may have a numbing effect on some users, others take them as a reminder to seek better protection against surveillance and tracking threats on the internet. After all, service providers selling our data to third parties is not a new development. This post provides more in-depth background on how ISPs use VPN to spy on you.
Third parties taking advantage of VPN’s many flaws for nefarious purposes is so real that earlier this month, two U.S. senators (Ron Wyden and Marco Rubio) raised alarm in a bipartisan letter [PDF] to the director of the Department of Homeland Security’s new Cybersecurity and Infrastructure Security Agency (CISA), Christopher Krebs.
In the light of all this, what doesn’t cease to amaze me is how many privacy-concerned users still think that VPNs (Virtual Private Networks) provide sufficient protection. A VPN creates a secure encrypted connection (“tunnel”) between the endpoint and a VPN server that is supposed to prevent third parties from tracking users, spying on their web activities, or blocking them from reaching specific sites. In many countries, a VPN may allow users to bypass government censorship.
There are, however, many misconceptions about VPN’s actual capabilities. Yes, a VPN can mask your connection and your traffic. However, how effectively and for whom? Does your ISP or your VPN provider still get to sneak a peek? And who else could have access to your data?
Perhaps you’re even using your VPN in a way that defeats its purpose? Let’s take a closer look.
Many users try to shield their web activities from prying eyes by installing a VPN extension on their browser. Big mistake. One way to not use a VPN properly is through a browser extension.
A study conducted by security researcher John Mason shows that 70 percent of VPN Chrome extensions leaked the user’s DNS. This means that the sites you visit can potentially find out about the real connection details behind your “super secure” VPN extension.
Extensions that were found vulnerable to attacks leveraging this vulnerability include Opera VPN, Hola VPN, Betternet, VPN Unlimited, ZenMate VPN, DotVPN, and Ivacy VPN. This is by far not a complete list. The easiest way to find out if your Chrome VPN extension is affected is by testing it here.
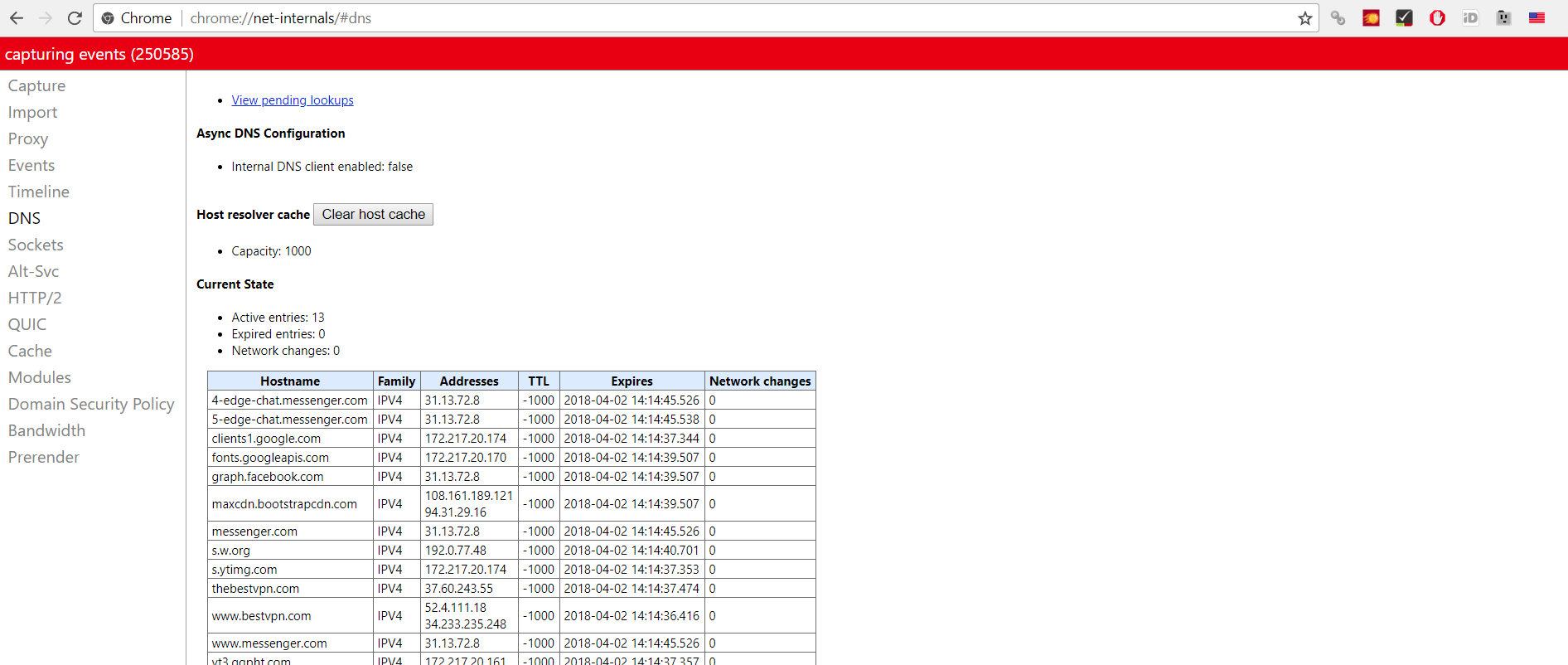
Source: https://thebestvpn.com/vpn-leak-test/
This flaw is rooted in a Chrome feature called “DNS Prefetching”. It reduces latency by resolving DNS queries to sites (domain to IP address) before a user even decides to visit the particular site. This feature makes Chrome fast, but also causes a DNS leak which is detrimental to the interests of millions of users who have installed these extensions for improved privacy protection.
Now that we’ve already addressed why VPN extensions, in particular, are unreliable, what about other problems? Despite all the claims from your VPN provider, how safe are you from IP leakage? Is your provider holding onto the logs of your web activities? Are they selling that data?
These are legitimate concerns, especially if you’re paying for VPN service. If not, be aware that “free” means you are the product and shouldn’t be surprised if your provider is monetizing user data.
Let’s go through a checklist of potential VPN risk sources:
If you can’t answer one or more of these questions, keep on reading. It may make you safer.
Your first thought should go to the method in which you connect to your VPN. Some providers like to supply you with their own client. Hotspot Shield does this, IP vanish also does this, and so does CyberGhost.
A recent study conducted by Mohammad Taha Khan (PhD candidate at the University of Illinois at Chicago) and Narseo Vallina-Rodriguez (research scientist at the Networking and Security team at the International Computer Science Institute in Berkeley) found that out of 61 VPN systems, 13 had programming and misconfigurations that resulted in the user’s traffic to be leaked, defeating VPN’s whole purpose.
VPNs that don’t employ their own application are not necessarily less secure.In fact, many popular VPN providers like Vpnbook take advantage of an OpenVPN client. OpenVPN (which is open source) is also built into popular router firmware, such as DD-WRT, Vyatta, pfSense, et al.
That’s a lot of fancy equipment, but does it always guarantee that OpenVPN is properly implemented against basic types of VPN leakage? Not so fast...
...because judging by the number of OpenVPN vulnerabilities disclosed in the past, you still better be careful. One that stands out is “VORACLE”. An attack allows the collection of plain text traffic before it is routed to the VPN provider. This attack only works under certain circumstances.
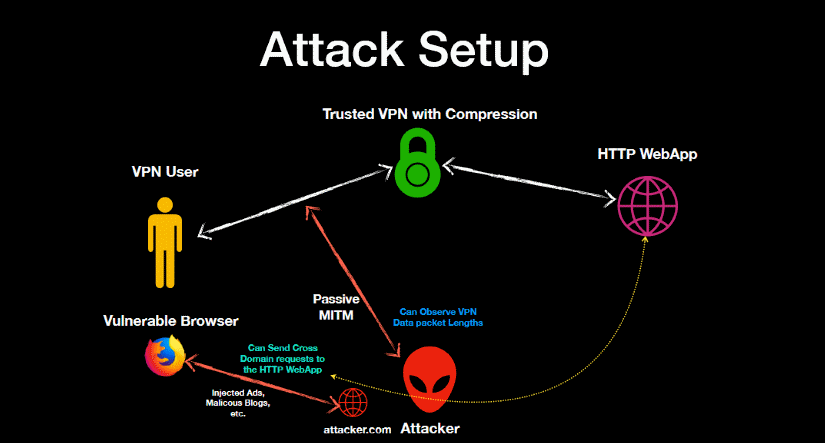
Source: https://www.bleepingcomputer.com/news/security/voracle-attack-can-recover-http-data-from-vpn-connections/
As long as the attacker is on the same network as the victim who is taking advantage of a VPN provider that uses the OpenVPN protocol, a man-in-the-middle attack can be conducted - through a rogue WiFi hotspot, for example - to decrypt VPN traffic that’s being sent over plain text HTTP.
Don’t assume just because you’re on a site with SSL/TLS enabled that you’re 100% safe. There are ways to kick victims off HTTPS. Many sites still have the HTTP version enabled, and frequently the HTTPS version isn’t completely enforced - which allows traffic manipulation (see sslstrip).
The MITM attack exploiting OpenVPN was discovered by Ahamed Nafeez, a security researcher who presented the concept at last year’s DEF CON and Blackhat USA conferences. BleepingComputer’s Catalin Cimpanu quoted Nafeez: "VORACLE allows an attacker to decrypt secrets from HTTP traffic sent through a VPN.”
One of the most basic types of data leakage with many VPN providers is IPv4 and IPv6 DNS leakage. Your computer currently utilizes two versions of internet protocols - versions 4 and 6. Before version 6, there was version 4. IPs that reside in version 4 look like this: 127.0.0.1. Version 4 IPs go from ranges in 0-255. Version 6, however, does not follow this format, its IPs look something like the following: fe80::6ae3:b5ff:fe92:330e:
The reason this “upgrade” in the internet protocol even occurred has to do with capacity. The IPv4 capacity cannot handle the number of internet users that will be online in the years to come. IPv6 adds that higher capacity. Since your computer utilizes both, if a VPN provider does not route both types of traffic to their servers, you may encounter IP leaks like so:
If for example your computer tries to connect to an IPv6-only site, and your VPN covers only IPv4, then you can encounter a VPN leak. Not all providers cover both IPv4 and IPv6, so you should take note and get clarity before committing to one.
Another way VPNs are leaking IP addresses and overall traffic has to do with the “killswitch” scenario. Say you’re connected to a VPN, and all of a sudden your VPN connection drops. Does your VPN stop all traffic or allow traffic to continue to and from your actual endpoint?
The problem here is that many VPNs don’t come with a killswitch that stops all traffic in that scenario. Instead, they simply allow your traffic to go through your original network. If you’re using, for instance, Skype with a VPN that has no killswitch, and you disconnect from the VPN, your real connection is then used for Skype, and thus your traffic remains unprotected.
Speaking of Skype, one common standard, “WebRTC”, is particularly prone to DNS leaks through VPN. WebRTC utilizes P2P, voice calling, video chat, etc. all through the browser. In browsers like Firefox, Chrome, and Opera, WebRTC is enabled by default. The only way to stop the VPN leaks is to disable WebRTC completely.
The quickest way to check if your machine is susceptible to this type of leak is to enable your VPN, visit https://ip.voidsec.com/, and see if your real IP is identified on the webpage.
You can also use Sploit.io, a free service I’ve created that can show you whether or not you have potential WebRTC leaks even with a VPN enabled. Go see just how good your online OPSEC is. Both services will show your local IP, remote IPv4 and remote IPv6 (if there is one).
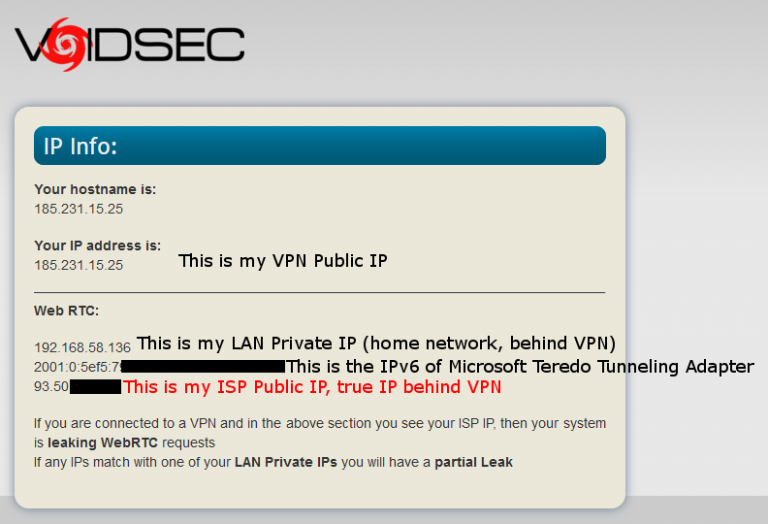
Source: https://voidsec.com/vpn-leak/
Now let’s examine how VPN providers handle their logs. Most VPN providers hold onto logs for months. Usually, the logs contain IP address information (from what IP you connected with the VPN service). This includes not only the IP but timestamps. Timestamps allow a VPN provider to match what service was requested on their platform by whom. This then leads onto logging all traffic going in and out of the VPN.
Because all the logging happens behind the scenes, it doesn’t ring any alarm bells for individual users. It should, because it’s actually a big deal, given the tremendous amount of data collected this way. These logs could be held onto for years, depending on the provider’s policies and how your jurisdiction handles privacy laws. If you’re engaging in illicit activities, for instance, VPN providers will hand over all the logs they have on you to law enforcement. No VPN provider is going to take a bullet for a user’s activities.
How do free VPN providers handle all the data? Many users probably wonder what the catch is with free VPN providers. Free VPN providers can sell your private traffic data to advertisers. Usually, this is listed in their terms of use and privacy notices (but not all the time, since not all VPN providers are legitimate businesses/companies).
Hopefully, I’ve shed some light on how unsafe VPNs can be. It’s crucial to fact check the claims of your VPN provider. How you connect to your VPN, how traffic is being routed, which browser you’re using, and what it enabled that could allow leakage - these are all critical factors to consider to protect your privacy and anonymity.
VPN is not the best solution when it comes to online privacy. There are many better (free) alternatives like Tor, OpenWRT (using a router instead of a client to route all traffic through an endpoint), or SSH tunneling. Companies who need complete anonymity for their employees online (like law firms or banks) and security researchers, often use Silo, the secure cloud browser provided as-a-service by Authentic8.
At the risk of repeating myself - do not use a VPN extension. Such plugins don’t protect your machine; they only try to route traffic from within your browser. Once you leave the browser to use any other application, such as Skype or VoIP, you are left unprotected. You’re much better off using clients like OpenVPN that route all your traffic through the VPN and not just your browser, which reduces the attack surface and risk of data leakage.