Learn domain OSINT techniques to uncover the ownership of a website. Explore WHOIS lookups, reverse IP searches, and safe methods for digital investigations.
Investigating who is behind a website is critical in most OSINT investigations. At first sight, we might think that we will only need to inspect a website when it is strongly related to the investigating case. However, there is more information to be gleaned in an investigation. For instance, OSINT gatherers need to examine domain names in various scenarios, such as:
- Attribution: This is the main reason for knowing who is behind a website. By revealing the person/s operating a particular website, we can connect various online entities belonging to one person together, know who hosts and registers associated domain names and finally understand their motivations. For example, suppose we discovered that a Russian operator is behind an English website used to spread fake news. In that case, this gives a clear clue about foreign influence against national security.
- Validate sources: If the website we are taking information from is unknown, we must validate its authenticity to ensure accuracy and reliability. Keep in mind that some websites could be used to spread disinformation to mislead investigations.
- Reveal operator capabilities: Inspecting a chain of websites will reveal their operators' capabilities, which gives clear insights about who is behind them. For example, some websites could be well-designed and have official accounts on main social media platforms in addition to using dedicated hosting in foreign countries, which offers a clear clue that their operators are well-funded and could be connected to a nation-state.
- Cyber threat intelligence: Investigating domain names associated with ransomware and phishing attacks could reveal their actual operators.
- Tracking financial transactions: Revealing website ownership will facilitate tracking online money transactions, money laundering activities and revealing any financial activities associated with the website.
Now that we have understood why investigating website ownership is critical for OSINT investigations, let us begin discussing the different tools and strategies to reveal website ownership and how to collect information safely
Tools and techniques to investigate website ownership
There are vast arrays of tools and techniques OSINT gatherers can use to analyze website ownership. In this section, I will focus on the most critical methods. However, before I start, it is recommended to begin reading the subject website content before applying tools to it. You may find the actual owners by reading the “about us” page or by downloading and reading public documents hosted on the website.
Investigating website history
Previous versions of a website can reveal necessary information about its owners. A website could change over time. For instance, new content is added, and others are removed. Inspecting previous versions may reveal information such as mailing addresses, phone and emails, and other information such as business partners and branches.
The Wayback Machine is one of the most popular online services for fetching previous versions of websites, which seamlessly plugs into Silo for Research.
How to perform WHOIS lookup
Every domain name has associated information that identifies its owner, whether they are a person or a company. Information in WHOIS record include:
- The name and contact information of the domain name owner
- The name and contact information of the registrar (the organization or company that registered the domain name)
- The domain registration and expiration dates
- The name servers
- The administrative and technical contact information — typically, this information belongs to the registrar company
There are many services to retrieve the WHOIS records:
We should also check the domain name history to review the past ownership and registration changes of the subject domain name. A free service for retrieving domain history is WHOXY (see Figure 1).
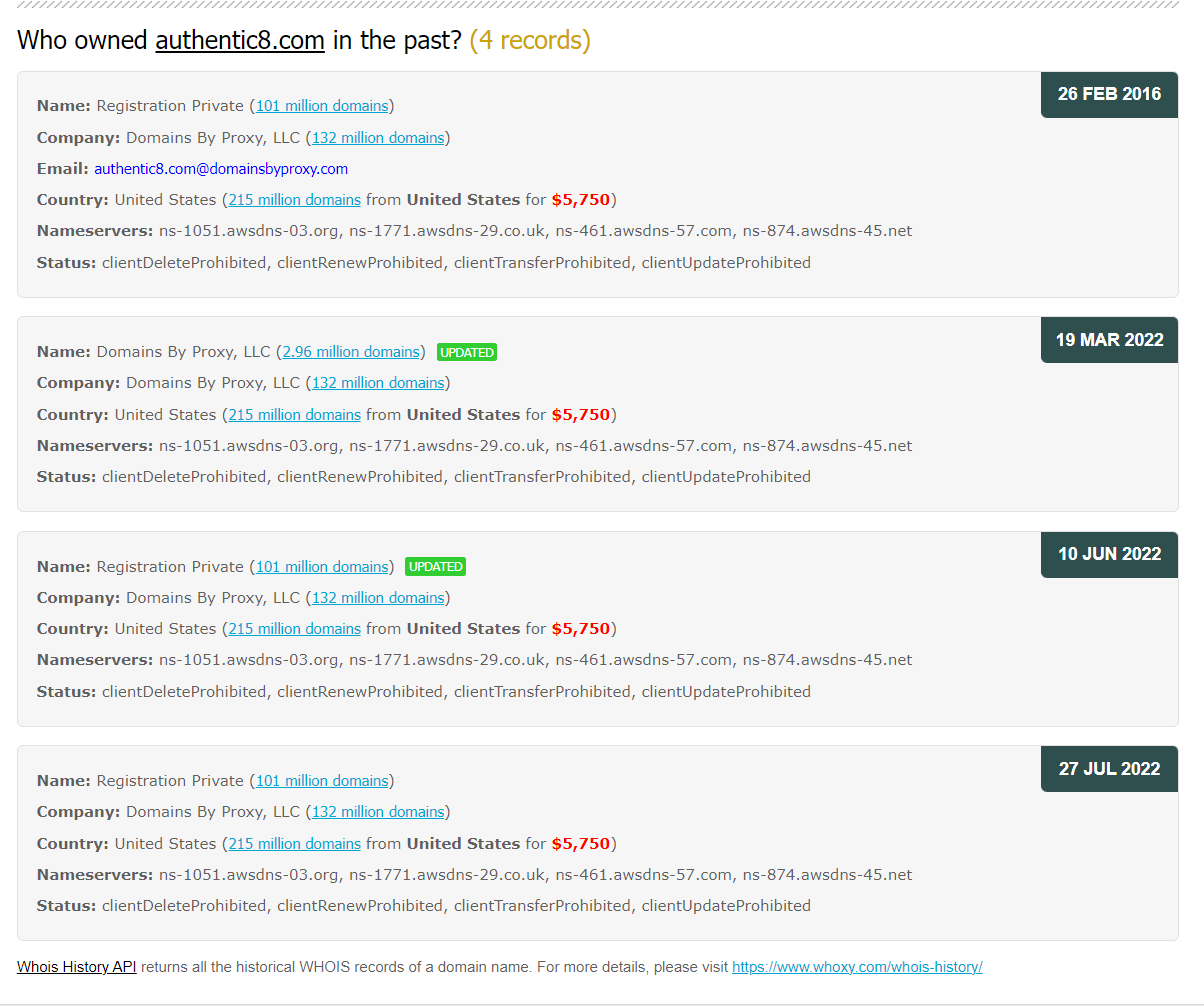
Figure 1 - Using whoxy.com to reveal domain name history
Hosting company
The company used to register the domain name could differ from the one used to host the website files. Here are some services to detect the hosting company of any site on the web:
The above services will also give you the IP address used by the website, so make sure to remember this info to use it in the next section.
Reverse IP search
Many websites use shared web hosting services. Threat actors may host different websites belonging to them on these shared hosting platforms, which results in these websites using the same IP address.
We can conduct reverse IP searches using many free online services to find all websites hosted on the same IP address.
- ViewDNSinfo – The reverse IP lookup tool allows finding all domain names hosted on the same web server (see Figure 2)
- DomainTools Reverse IP lookup
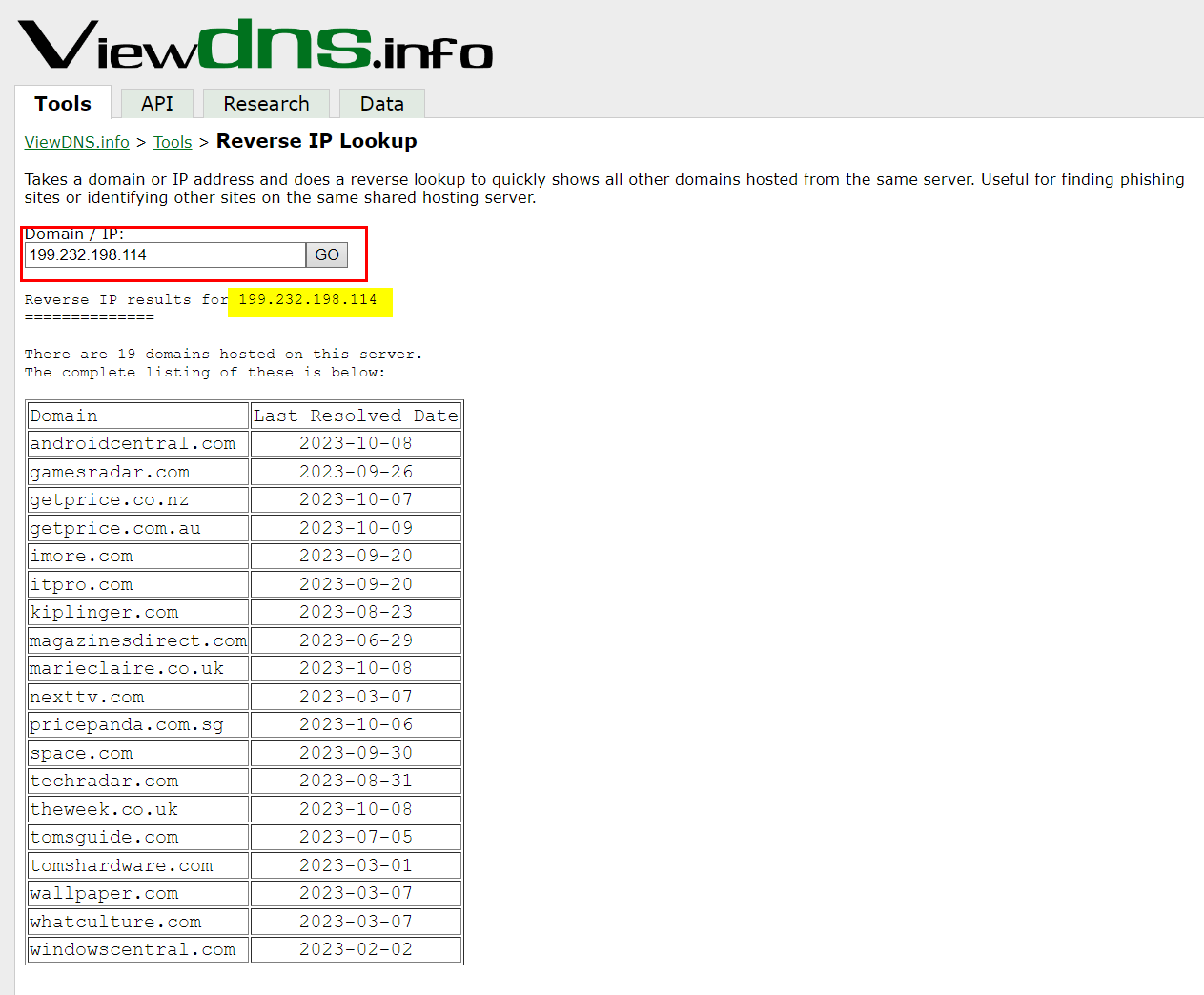
Figure 2 – Finding all domain names hosted on the same web server
Reverse Google analytics ID
Google Analytics ID is a unique identifier issued by Google that distinguishes a specific website or web application. Google uses this tracking ID (has this form ua-xxxx) to collect statistics about traffic and visitor behaviors to websites or applications.
Web admins frequently use the same Google ID to collect analytical data for multiple websites. Google provides a dashboard to monitor many websites using the same account.
We can exploit this feature by reverse searching Google Analytics ID to identify all websites using the same ID, which means they belong to the same entity.
We can conduct this search manually. However, there are free online services for doing this, such as:
Website source code
A website source code may reveal important information about its owners. For example, I identified who was behind a website in many investigations by reading comments in the HTML source code. Web pages source code could reveal the following info:
- Web developer name
- JavaScript libraries used
- Code snippets borrowed from code repositories
- The HTML template used to create the website
- Abandoned code snipped containing website-specific information
All web browsers have the feature to read visited website HTML source code. In Google Chrome, we can open the DevTools by pressing “Ctrl + Shift + C” under Windows and Linux, while Mac requires pressing “Cmd + Option + C.” To view page source code, right-click over the web page and select “View page source”.
If we suspect a specific code snippet is unique to the subject website, we can use a dedicated search engine to search for matching occurrences of any code snippets across the web. There are several search engines for doing such a search, the following are the most popular ones:
Inspect associated email addresses
We may find email addresses during our search within target website contents or archived versions. These should be further inspected to identify connected entities across the web. Here are some steps to inspect email addresses:
Check if the email address is still valid or active. Here are two services for doing this:
Check if the email address was included in a previous data breach. Ensure to read the previous data breaches where this email was found because it may reveal important information — for example, if the email was included in a HOTEL data breach; this will point that the owner is linked or at least visited this HOTEL at some time.
Examine social media and online profiles
Finding official social media accounts associated with a website can help link and identify potential website operators. Analyzing consistent identifiers in profiles like usernames, profile images, bios, and linked accounts/sites can indicate who may be behind a website.
It is also helpful to search for press releases, articles and interviews linked to the target website, as it may reveal information about the individuals or organizations behind it.
All images posted on the website should be examined carefully, for example, by checking their metadata information and conducting a reverse image search to find where they appear online.
Safely investigating website ownership
Revealing anonymous websites' ownership and operator information is crucial for OSINT investigations. But just as critical is making sure the watchers don’t become the watched. Your digital fingerprint could tip off webmasters to your investigation, allowing them to destroy evidence, falsify facts or even target the investigator. The only way to safely investigate web ownership is with complete isolation and managed attribution.
While websites may utilize privacy services, obscure registration information (hide their WHOIS records) and conceal hosting providers, skilled OSINT analysts can safely use various tools to piece together attribution clues. Without tipping off the subject of the investigation, practitioners can gather critical information about their target.
To learn more about how Silo can empower safe investigations, request a demo.
Domain OSINT FAQs
What is an OSINT domain lookup?
An OSINT domain lookup involves using open-source tools to find information about a website’s domain registration, hosting, and IP details. It helps investigators identify who owns or manages a website without alerting the target.
How can I find the ownership of a website?
You can uncover the ownership of a website by performing an OSINT domain lookup through WHOIS databases, hosting checkers, and reverse IP tools. Analyzing metadata and analytics IDs can reveal linked domains and operators.
Can OSINT reveal hidden website owners?
Yes, even if a site uses WHOIS privacy or proxy services, OSINT techniques like reverse IP lookups, historical WHOIS data, and cross-domain analytics tracking can uncover hidden website owners or related assets.
What is an OSINT WHOIS lookup?
An OSINT WHOIS lookup retrieves public domain registration data—such as the registrar, owner contact details, and DNS records—used by analysts to verify website ownership and identify connections across multiple domains.
How does reverse IP help in OSINT domain analysis?
Reverse IP lookups reveal other domains hosted on the same server. In OSINT, this helps uncover related sites owned by the same operator, exposing patterns of behavior or coordinated campaigns.
Why is ownership of a website important in investigations?
Determining the ownership of a website helps investigators attribute online behavior, detect influence operations, and connect multiple domains to the same entity. It’s crucial for threat attribution and validating sources.
Tags Anonymous research Compliance Cybersecurity Digital fingerprint Financial crime Fraud and brand misuse Law enforcement OSINT research Phishing/malware Trust and safety


