As social media use rises so does the amount of online personal information. Find out how threat actors use social media user information and data to launch phishing attacks.
The widespread of social media platforms has introduced radical changes to how people and organizations utilize the internet. For instance, people use social media platforms to socialize, communicate with their peers, find jobs and stay up to date with the latest news. Businesses use it to monitor competitors, promote their products and services and communicate with customers and employees cost-effectively.
The number of social media users is growing at an explosive rate. For instance, according to Statista, as of January 2024, of the 5.35 billion internet users worldwide, 5.04 billion of them were social media users. Threat actors look at social media platforms as a gold mine of information that they can exploit to conduct various malicious activities.
In this article, I will discuss how threat actors can leverage social media platforms to conduct attacks against unsuspecting internet users, primarily phishing attacks. However, before I start, let me briefly discuss the privacy dilemma when using social media platforms.
Privacy dilemma in social media platforms
Social media platforms hold personal information about billions of people. Let’s use Facebook as an example. Despite enforcing privacy settings that prevent a Facebook user from letting non-friend users see their posts or photos, other non-friend users may still be able to access such protected content. For instance, a user may tag their friend in a post or picture. If the tagged person has lax privacy settings, then the entire user's Facebook friend list can view the tagged photo or post.
Aside from leaking users' private information, many social media users post vacation information, such as their current geolocation, or post photos about the place they are visiting. Criminals can exploit this information and try to rob these empty houses.
Cybercriminals have become more educated, and they can leverage open source intelligence (OSINT) tools and techniques to collect information about particular users from their social media posts to craft a customized attack against them.
What is social media phishing?
In a previous article (Phishing 101), I discussed phishing attacks focusing on email phishing. We can group phishing attacks according to the medium used to execute them, such as "email phishing" for attacks executed via emails. As the name implies, social media phishing is conducted via social media platforms like Facebook, Instagram, Twitter (X) or Discord. Such attacks aim to obtain target users’ account credentials or to steal their personal information.
Social media platforms' open nature allows anyone to create an account. Some social media websites, such as Reddit, do not require extensive identity checks to create an account. You only need a valid email address to receive the account activation link. The ease of creating social media profiles allows threat actors to create countless fake accounts and use them for different malicious purposes.
Social media phishing tactics
Threat actors leverage different tactics to carry out phishing on social media platforms. Here are the main ones:
Email notification
Most social media platforms require users to have an email address to activate their accounts. It is common for social media websites to send email notifications to users to tell them what is happening on the platform and encourage them to access their accounts. In Figure 1, we see a LinkedIn email notification asking a user to access their account to read the remaining message sent via its platform by another LinkedIn user.
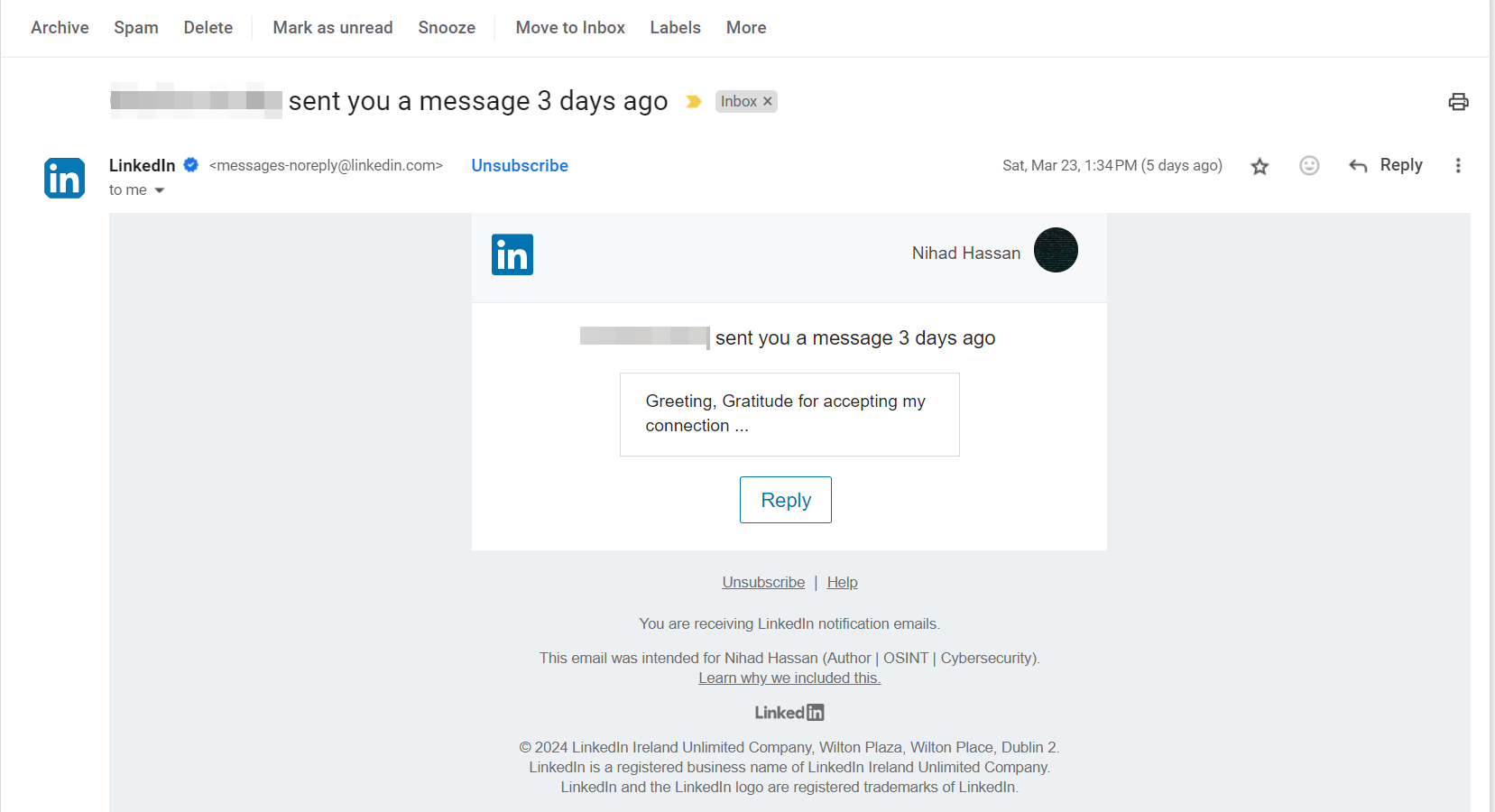
Figure 1 - LinkedIn sends a notification when someone sends you a message via its platform. You need to access your LinkedIn account to read the full message.
Threat actors try to impersonate these emails by creating emails that resemble those sent by popular social media websites and inserting their malicious links — or attachments — into the email. Once clicked or downloaded by the recipient, the malicious actions are executed, which can be:
- Installing malware on a user computing device if the email contains an attachment
- Driving the user to a malicious website impersonating the social media platform and asking them to provide their account credentials to steal them
Hackers use techniques, such as typosquatting and image links, to conceal their links' destinations. Figure 2 shows an email sent by a hacker impersonating a legitimate email provider; the hacker hides the phishing URL behind an image button.
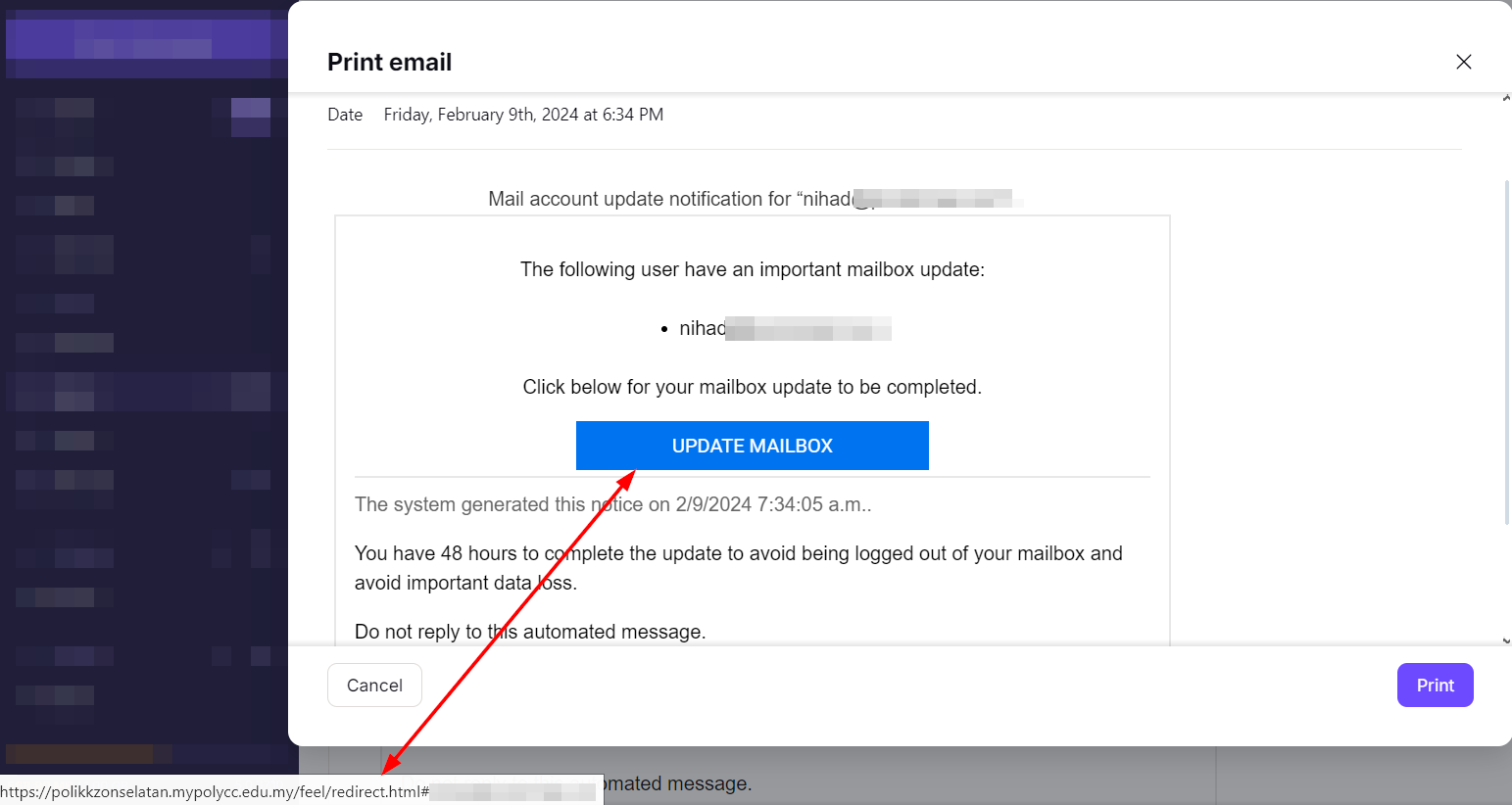
Figure 2 - Hackers conceal their actual URL destination by hiding it behind images
Fake social media profiles
As we know, creating an account on most social media platforms is free. Anyone can create an account that impersonates another person, organization or brand without needing legal proof. Of course, accounts that belong to celebrities, official companies and even verified individuals are commonly vetted by some social platforms in some way. However, most internet users do not consider this verification mechanism when interacting with social media accounts, making them easy targets for phishers.
For example, a hacker can create a social media account impersonating the Authentic8 company on Twitter. To make their Twitter account look legitimate, they can reserve a domain name that is very close to the original one. For instance, using a name such as "authentic88" (adding 8 to the last name) or "authenticc8" (adding 'c' letter to the name). Now, they can interact with Authentic8's customers (it is easy to get a list of potential customers by checking who is following the company's profile on social media platforms) and send phishing links (via Twitter private messages or by posting Tweets with malicious links), asking users to visit a particular portal to renew their subscription or request sensitive information from Authentic8 users.
Phishers use different tactics to create identical websites to those they are impersonating, such as:
- Website copiers such as HTTrack and Wget (they copy the legitimate website and upload it to their hosting space as if it is their website)
- Use specialized phishing tools such as HiddenEye, BLACKEYE v2.0, Gophish and SocialFish (the last one can clone different social media websites to execute a password-harvesting attack link with just a few clicks)
- Use dedicated tools for generating phishing pages such as Zphisher
Fake social media profiles can also be used in combination with other social engineering (SE) techniques, such as creating a sense of urgency and fear or exploiting trust and social connections. For instance, a fake profile may claim to be an employee of the Authentic8 company and reach out to customers with a "limited-time offer" or a "security update" that requires immediate action, such as:
- Clicking a malicious link
- Providing their account credentials to renew their subscription
- Sending a lockout notification to users, prompting them to reset their password to avoid losing access to their account
Such tactics can significantly increase the chances of users falling victim to phishing attempts by clicking on malicious links or revealing sensitive information.
Using hijacked social media accounts
Another tactic threat actors employ is exploiting trust and social connections by hijacking legitimate accounts of individuals or impersonating the target friends or family members. This approach can make the phishing attempt more successful, as users are more likely to trust messages or requests coming from their social peers.
To execute such attacks, hackers need first to steal social media accounts using different methods, such as:
- Using automated tools to guess target passwords: this attack is feasible when the target account uses weak and short passwords.
- Employing SE attacks via phishing emails, typosquatting websites, fake login pages, SMS phishing and even in-person to acquire target social media account credentials
- Using malware to infect devices with keyloggers to steal account credentials.
- Using credential stuffing attacks to gain unauthorized access to social media accounts by attempting stolen login credentials from other data breaches belonging to the same target users.
After compromising the social media account, threat actors begin exploiting it for targeted attacks in several ways:
- Direct messages: A phisher who has gained unauthorized access to a user's account can send direct messages to the account's entire friend list. These messages contain links that lead them to carefully crafted phishing websites. Hackers exploit the trust relationship between the account holder and their connections to convince them to click on these malicious links without hesitation.
- Fake posts and comments: A phisher may create posts and comments containing links to malicious websites, exploiting the trust between social media users. For example, your friend on LinkedIn may post about an investment opportunity in some cryptocurrency companies. You would likely trust clicking links posted by your friend, expecting to be directed to a legitimate crypto investment website. However, the malicious link would redirect you to the attacker's phishing site to steal your credentials or exploit software weaknesses in your web browser or app to execute different malicious actions.
As social media becomes increasingly integrated into our daily lives, threat actors become more willing to exploit these platforms for phishing attacks. From impersonating trusted entities to leveraging fake profiles and malicious posts, their techniques depend on manipulating the human mind to do things that are contrary to ordinary behavior. In this article, I showed a few techniques attackers use to exploit social media platforms for phishing attacks. I will expand this area in future articles to discuss more attack methods and the best methods to prevent them.


