A practical guide to OSINT on X (Twitter): profile analysis, advanced search operators, Google Dorks, and vetted tools, built for SOCMINT and investigations.
Twitter OSINT is the collection and analysis of public data from X (formerly Twitter), including profiles, posts, media, lists, and interactions, to support investigations. Analysts can combine platform operators (e.g., from:, filter:) with Google Dorks and attribution controls to map identities, verify events, and preserve evidence.
In this guide, I will provide different techniques for effectively searching the X platform, including using various tools to facilitate and improve our X search.
Here's what we'll cover at a glance:
Use cases: identity resolution, event verification, network mapping, content preservation.
Quick wins: start with profile triage, run advanced search operators, then preserve evidence.
Checklist — Profile triage
Capture handle, display name, bio, join date, location, URL(s).
Screenshot header/avatar; run reverse image search.
Note Topics/Lists, followers/following deltas.
Extract external domains for WHOIS/tech stack.
Checklist — Search
Start with
from:,to:,@mentions.Layer
lang:,filter:images|videos,since:,until:.Add geo:
near:orgeocode:when location matters.
Checklist — Preservation
Save search, export links, capture hashes.
Archive target URLs (court-defensible methods).
Store operator strings with timestamps.
Twitter (X) background
The X platform (formerly called Twitter) is a microblogging social networking platform. Initially launched in 2006, Twitter witnessed a significant boost in 2007 after receiving a series of funding led by Union Square Ventures and becoming very popular in the global tech community. Twitter continued to witness growth until the COVID-19 pandemic when the amount of disinformation spread across its platform became very large and affected its profits. In 2022, Elon Musk acquired Twitter and in 2024, as a part of his efforts to rebrand Twitter, he decided to change its name to the X platform (www.x.com).
After Musk acquired Twitter, the platform witnessed a decrease in active users. For instance, in 2024, the user base has dropped to 335.7 million active users compared with 421 million in 2023.
Despite the sudden decrease in user numbers, X remains a trendy and important social networking platform for posting short messages. Although predicting future growth is somewhat challenging in the ever-changing social media landscape, X still has good potential to grow, considering its owner's financial capability and the group of companies he owns or has shares in.
Inspecting X accounts
An X account begins with the character @ followed by the username or handle. For example, my X account is @darknessgate. To access any X account, type https://twitter.com or https://x.com followed by the target X username: https://twitter.com/darknessgate
Please note that usernames are case-insensitive in URLs, so @DarknessGate and @darknessgate will lead to the same profile page.
Each X account has two names associated with it. The first one is the account name, which could be your company, personal name or nickname, such as "John Doe." Under the name, you will find the username of the account profile. X usernames can be changed after creation, but only if the desired new username is available.
The main X profile page also displays the following information:
- Profile image: This could be a personal photo or a logo if the profile is for a company; some accounts do not have a profile image
- Profile banner image (header image): The header image appears horizontally on the X profile page
- Profile bio: Some X accounts have a bio associated with them that could include different information, such as links to other social media accounts, websites or blogs managed by the X account holder; the bio can only span 160 characters
- Join date: Month and year when the X account was created
- Followers and following: Number and names of other X accounts who follow this profile and other Twitter accounts this profile follows
- Posts: This section contains all posts on X shared by this user
- Replies: All reposts made by the user
- Media: All media files, such as images and videos, uploaded by this X user; for example, the media file will appear in this section when posting a tweet associated with an image or video file
In Figure 1, I highlighted all these elements in red.
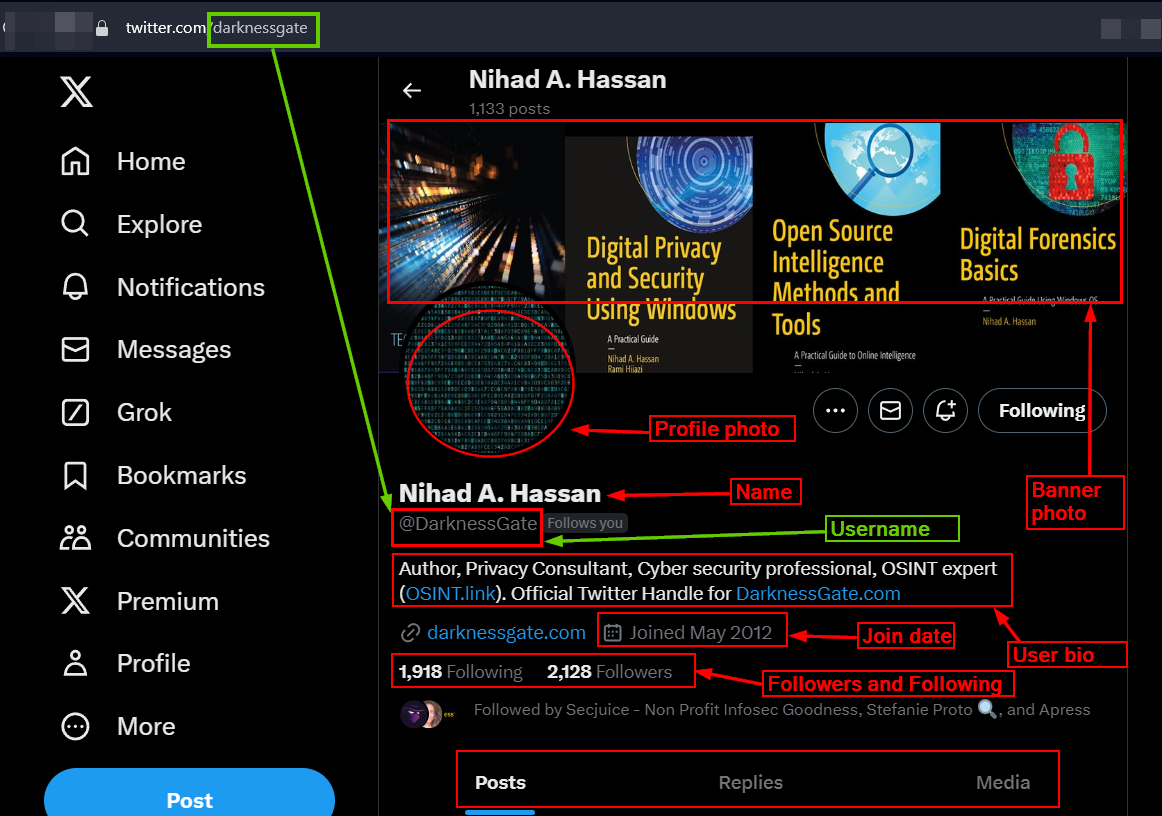
Figure 1 - The main X profile page includes important information to start our OSINT investigation
Other optional information that can be included in the main profile page of the X account includes the following:
- Location information
- Date of birth (for example, a specific date/time)
When available, these details can provide valuable context for OSINT investigations, as they will help us identify a user's geographic location and age.
There are three dots on the right side of the X profile page. Clicking them will display a dropdown menu showing different options related to this account. The most important two are:
- View topics
- View lists
Exploring these options can offer insights into a user's preferences and network. The "View topics" feature shows the subjects the account frequently engages with, while "View lists" can reveal X groups that the user finds relevant or important.
Now, let us experience how to further inspect each element in the X profile page.
> Looking for social media intelligence (SOCMINT) resources? Check out our Practical guide to SOCMINT research.
X username
The first thing we need to do is check whether the target X account uses the same username on other social media accounts. For instance, many users prefer to use the same username across different social media platforms. Here are three websites to conduct a reverse username search:
- Instant Username Search
- Reverse Username Search from socialcatfish
- Usersearch
- Username Checker from Privacy Watch
- Maigret: This is a Python-based automated solution that searches over 2300 websites to locate similar accounts, compiling the findings into reports in both .pdf and .html formats
- Sherlock: Find similar social media accounts across 400 platforms
X name
The X name can be anything: a user's actual name, a nickname or anything else. Like an X username, we can search for the target name to see where it may appear online. We can search for anyone's name using different online services or by using Google Dorks. Here are some online services for name search:
- Search Public Records: Search U.S. driving, arrest, citation and financial court records
- Familysearch: Access a massive archive of historical documents that contain cemetery records, birth, death, marriage, census, obituaries and more
- Searchpeoplefree
We can also use Google Dorks to search across the internet for anything related to the target X account name (in the examples below First refers to the target's first name and Last refers to the target's last name:
"First Last" (filetype:pdf OR filetype:doc OR filetype:docx OR filetype:xls OR filetype:ppt)
intitle:"First Last"
inurl:"First Last"
intext:"First Last"
allintext:"First Last"
allintitle:"First Last"
allinurl:"First Last"
"First Last" "contact information"
"First Last" "resume"
"First Last" "CV"
"First Last" "biography"
"First Last" "profile"
"First Last" "publication"
"First Last" "conference paper"
X profile and header images
Most Twitter users have a valid profile and header image. If the image contains small letters and other details that we need to enlarge to see them clearly, we can use the following image enlargement tools:
- Imglarger: Enlarge images up to 400% for free and to 800% after paying a fee.
- AI Image Enlarger from BigJPG
- Iloveimg: Upscale image
- Imgupscaler
We should conduct a reverse image search to see where the profile and header images appear online. For example, a user may use the same image on different social media accounts under different usernames. Here are some reverse image search engines:
- Bing Visual Search
- Google image search
- Pimeyes: Face search engine and reverse image search
- FaceCheck.ID by Sentient Labs
- Search4faces
User bio
X bios can be a rich source of information for OSINT gatherers. For instance, an X bio may contain the following data points that could be expanded to retrieve more information about the target X account:
- Links to the user's personal website or portfolio
- Connections to other social media accounts (e.g., Mastodon, Reddit)
- Professional affiliations or certifications, such as membership in professional communities or holding professional training certifications
- Personal interests, such as climbing
When a target user's X bio contains links to a personal website, it's crucial to conduct a thorough inspection using the following techniques:
WHOIS records analysis
Examine registration details, including registrant name, company name, administrative and technical contact information, domain name creation and expiration date. We can also reveal the registrar and hosting provider to expand our investigation. Here are some links to retrieve WHOIS records for domain names:
- WHO.is
- DomainTools
- Whois Lookup from MXToolBox
- Viewdns: Reveal different technical information about the target domain name, such as DNS, WHOIS and IP history (see Figure 2)
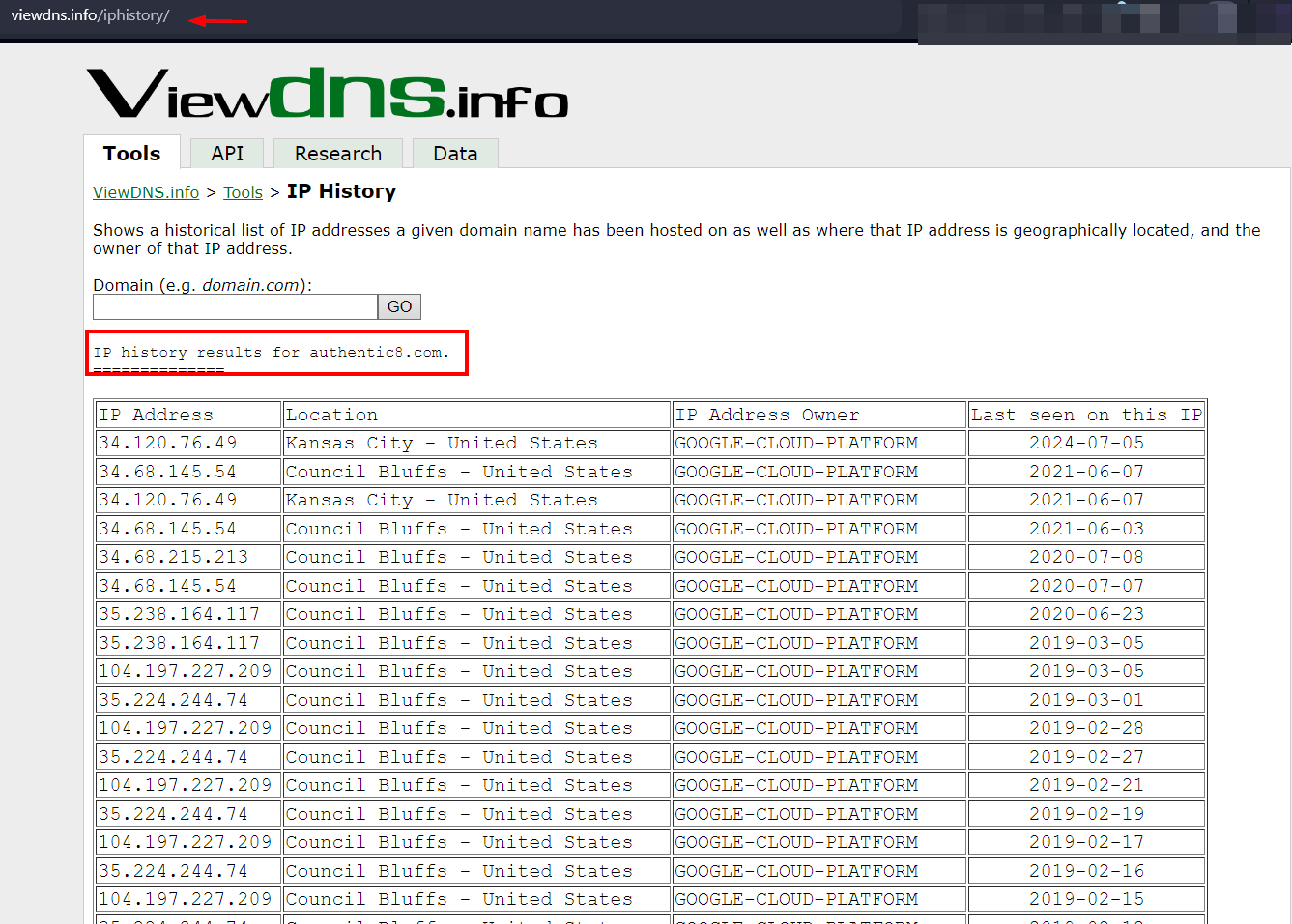
Figure 2 - Viewdns display various technical information about any domain name
Website version history
Archived websites may contain valuable information for OSINT gatherers that can help them discover new relations or reveal hidden connections with other entities. For instance, we can get the following info by checking past versions of websites:
- Previous job posting: by checking previous job postings, we may get an idea about the type of IT infrastructure used in the target company
- Technology used to build the website: previous versions may reveal the technology stack used to power the target company. Such knowledge can be used to discover vulnerable components and fix them before they get exploited by cybercriminals
- May reveal contact information such as email and phone numbers of key employees working in the company
- Previous versions of websites may contain links to PDF and MS Office documents that contain confidential information or could contain metadata that can help us reveal some information about who created these documents and the tools (software versions) used to create them
Learn more about uncovering website ownership >
The most popular websites for retrieving previous website copies are:
We can also use any of the above services to search for deleted and old posts. The process is straightforward:
- Choose the archive service
- Enter the full URL of the target X account (e.g., https://x.com/username)
- Browse through the archived versions of the account
There is also a dedicated service for fetching deleted posts from various archival services such as Google Cache, Wayback Machine, Archive.is, Ghost Archive and Yandex. The service is called Deleted Tweet Finder (see Figure 3).
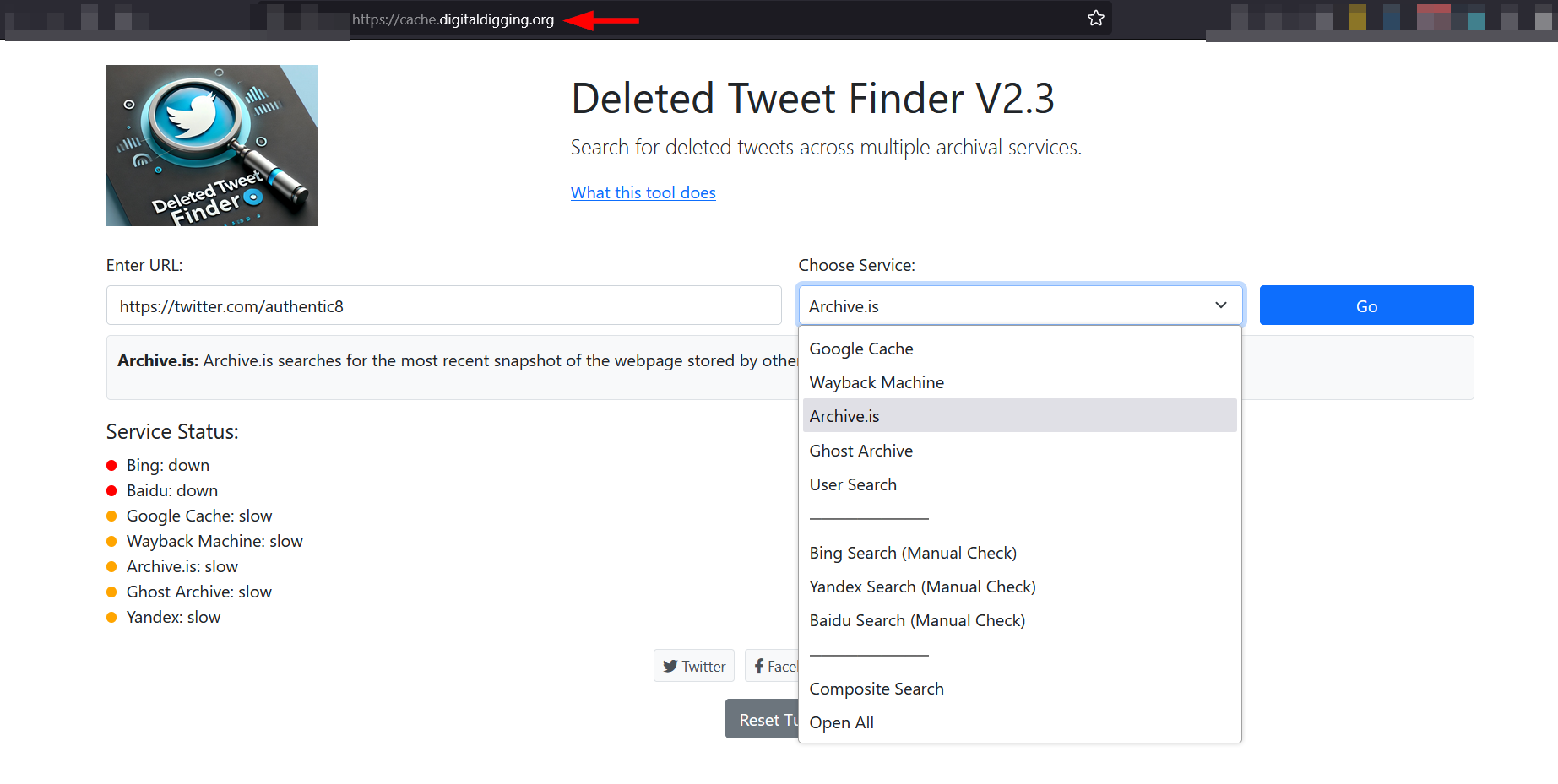
Figure 3 - Search for deleted X posts across multiple archival services
Technology used to build the website
Leverage tools like Wappalyzer or BuiltWith to identify the technologies used in website construction.
Linked websites
We can use different methods to identify linked websites. These methods include:
- Shared hosting: We can use services such as Who Hosts This and Website Hosting Checkert o detect target website hosting providers.
- Common IP address: Check if multiple websites are hosted on the same IP address using tools such as Shodan and ViewDNS.
- Similar domain registration details: By checking WHOIS records or by using an automated online service to reveal the WHOIS history of domain names such as Whoxy (see Figure 4).
- Shared analytics or tracking codes: This includes shared Google Adsense or Google Analytics. We can use services like SpyOnWeb to find linked domain names of a particular website using different methods (see Figure 5).
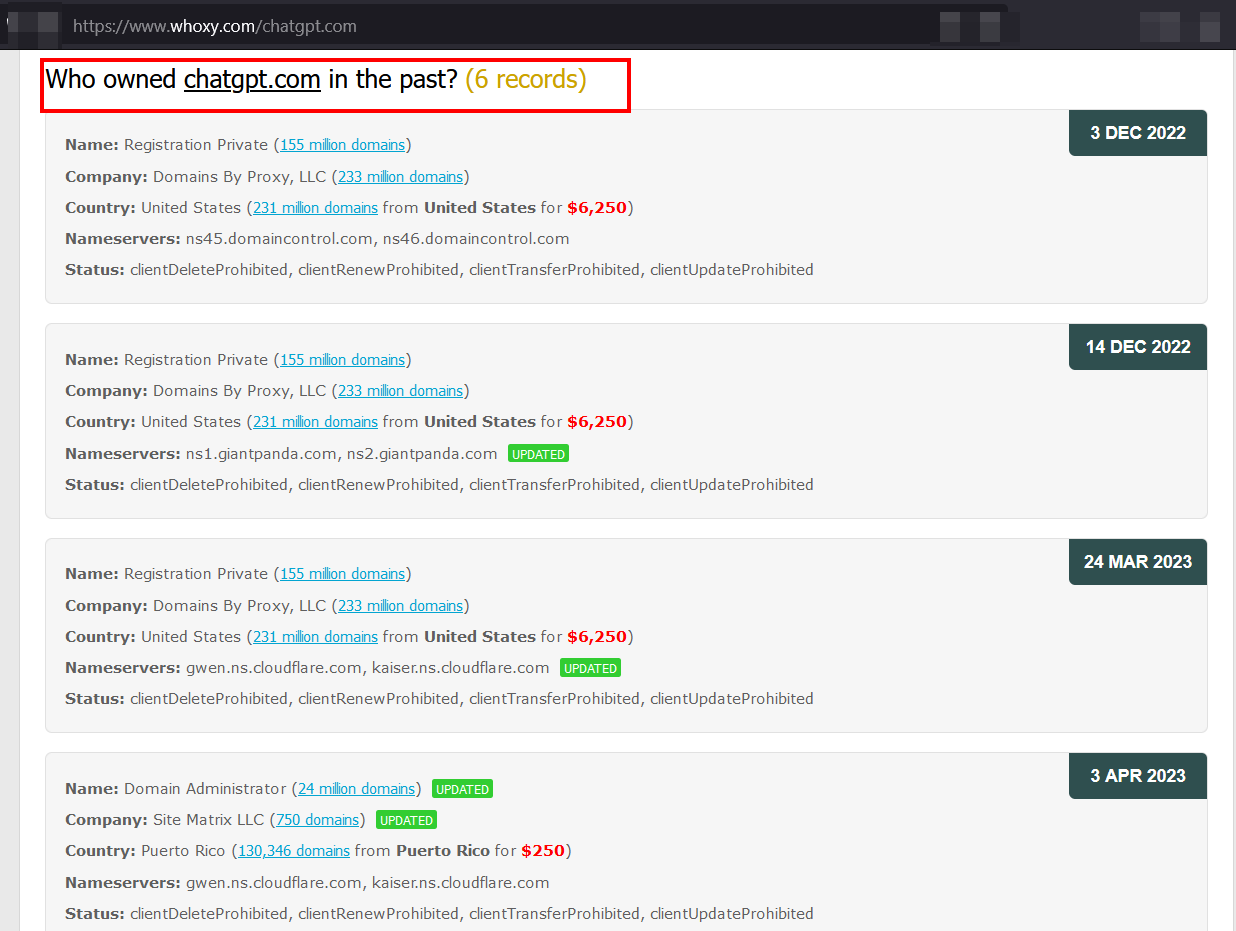
Figure 4 - Whoxy, a free online service for displaying WHOIS records history
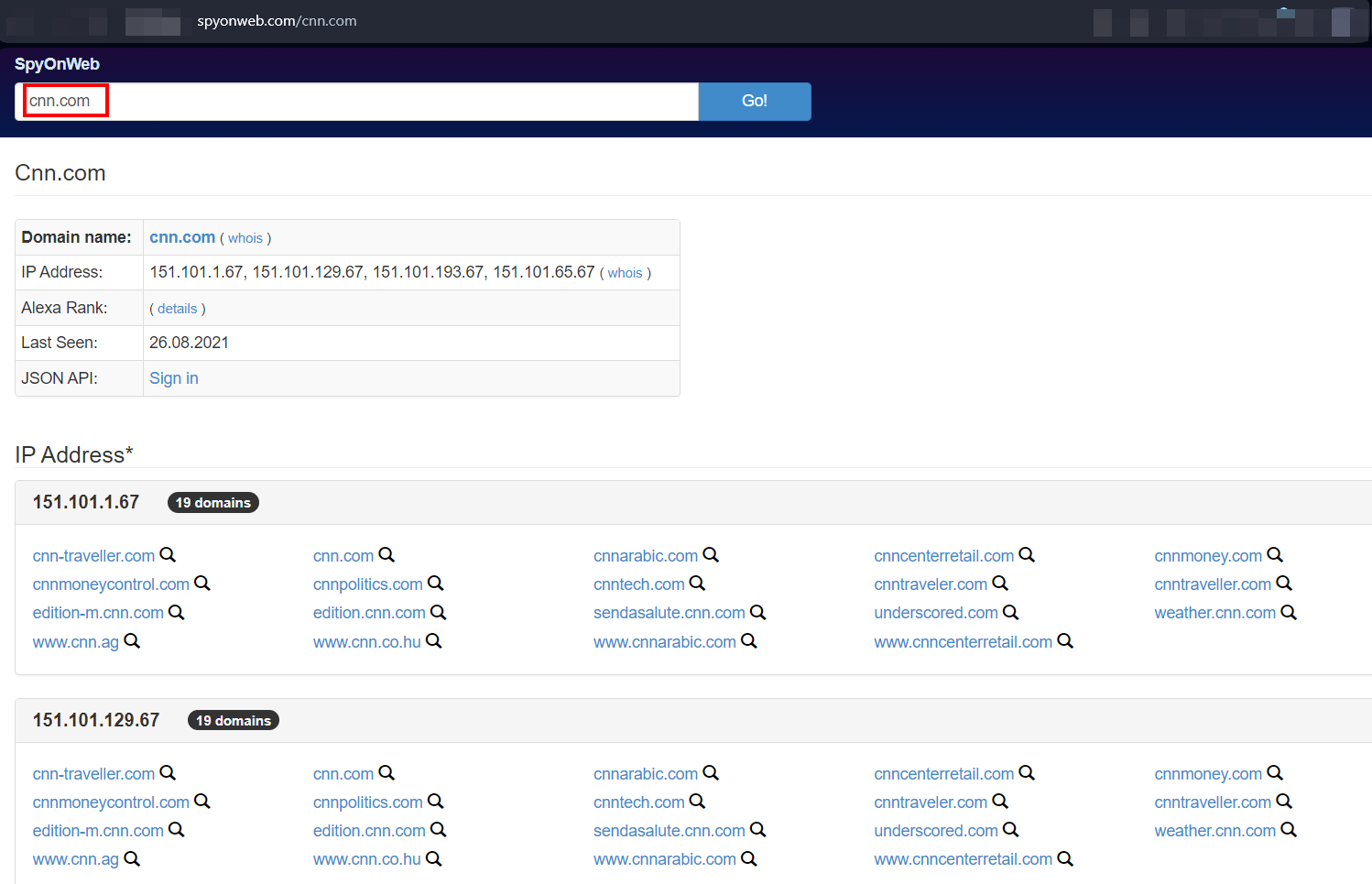
Figure 5 - Find out related websites using SpyOnWeb free online service
Search on X
Like other social media platforms, X has a built-in search functionality. The search box is located on the top right side when accessing X on your computer (web interface). We can search for keywords, hashtags, usernames or phrases using the simple search box. After entering the search query and hitting the Enter button, X will display results and group them into five category sections within the same page (see Figure 6).
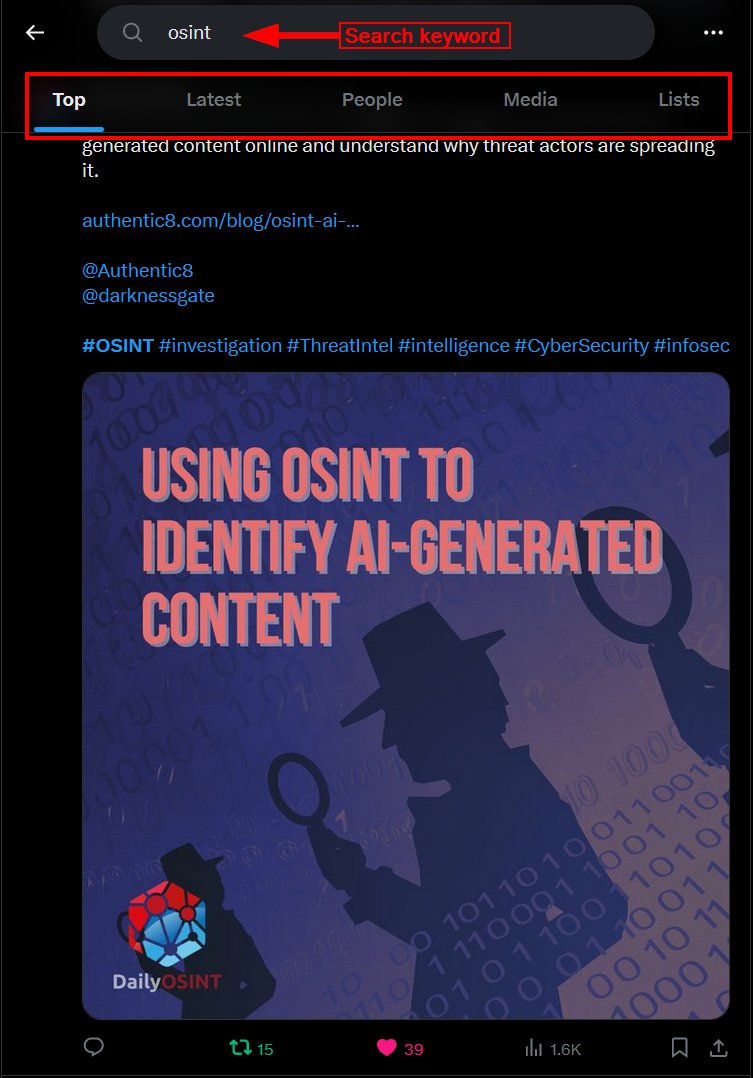
Figure 6 - X’s built-in search feature groups results into five groups
Here is a breakdown of what each category means:
- Top: These posts are ranked by X’s algorithm as most relevant based on your search query
- Latest: This section displays the most recent posts containing your search keywords, regardless of their engagement or number of likes and reposts
- People: This section will display profiles of users relevant to your search; these accounts don't need to be followed by you — it could be any X account that is relevant to the search terms you entered
- Media: This section contains posts with multimedia content related to your search keywords, such as posts containing images, videos and GIF images
- Lists: Search within public posts lists relevant to your search keywords
Advanced X searches
X’s advanced search provides a powerful tool for searching within the X platform. Here is how to access this functionality:
- Enter a search query into X’s basic search bar
- On the X search results page, click the three dots right next to the search bar
- In the dropdown menu, click "Advanced Search" (see Figure 7), and a pop-up window showing X’s advanced search dialog (see Figure 8)
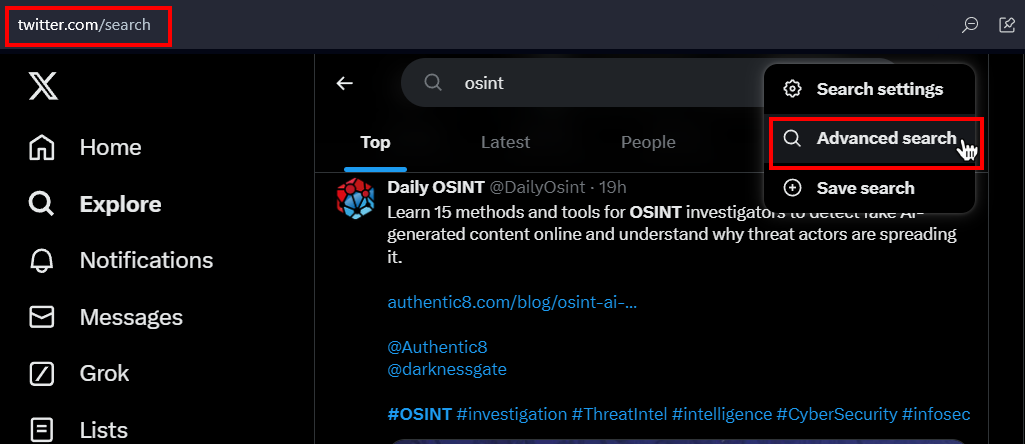
Figure 7 - Accessing X advanced search functionality
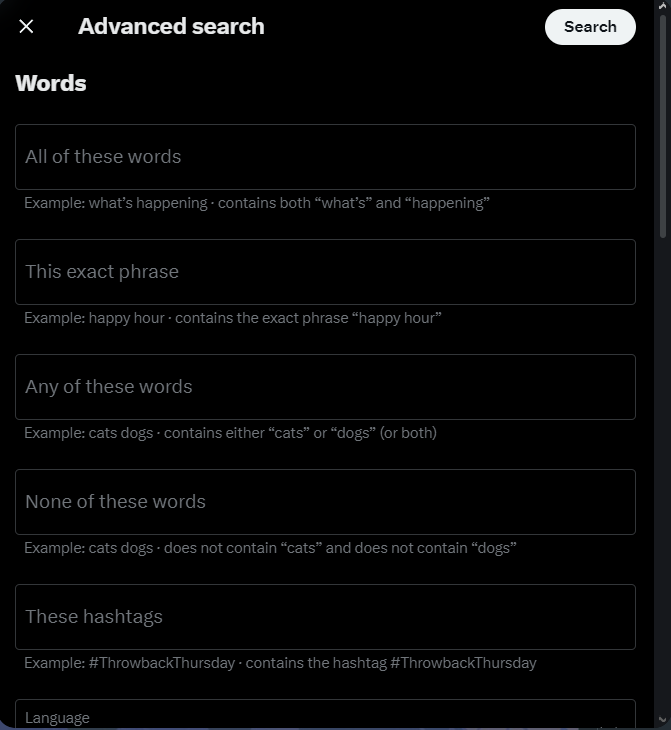
Figure 8 - X’s advanced search dialog window containing various fields for narrowing down your search
Here is how to use X’s advanced search:
Words section
- All of these words: Find posts containing a specific set of keywords (one or more); for example, we can search for OSINT and Authentic8 to find all posts with both keywords
- This exact phrase: Search for specific phrases; for example, Discord OSINT
- Any of these words: Search for two or more keywords at once; for example, we can enter OSINT, Authentic8 and Discord to search for all posts containing one or more of these words.
- None of these words: The opposite of the previous query
- These hashtags: To find posts that include one or more of the searched hashtags; for example, search for #osint #discord #guide.
- Language: Use the option "Any language" to return posts in any language; however, if you want to restrict your search results to a specific language, such as Arabic, specify the language from the dropdown menu (see Figure 9)
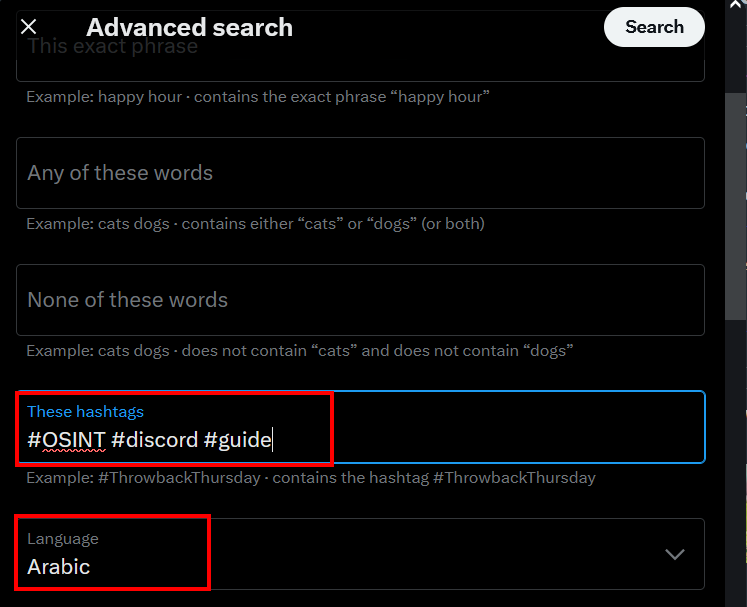
Figure 9 - Use the language filter to return results in one specific language, such as Arabic or Chinese
Accounts section
- From these accounts: Restrict your search to a specific X account; for example, @authentic8 — this will search for posts only from the @authentic8 X account
- To these accounts: Search for posts sent as replies to a specific X account; for example, @authentic8 — this will display posts that are replies to the @authentic8 X account
- Mentioning these accounts: This will find all posts mentioning a specific X account; for example, entering "authentic8" will find all posts that mention the @authentic8 X account
Filters section
The filter section contains different options, such as including posts with links and replies with the original post. It is good to leave the default options for comprehensive search coverage.
Engagement section
The engagement section allows users to further refine search results by specifying:
- The post's minimum number of replies
- The post's minimum number of likes
- The post's minimum number of reposts
This allows users to only return posts with a high level of engagement (see Figure 10).
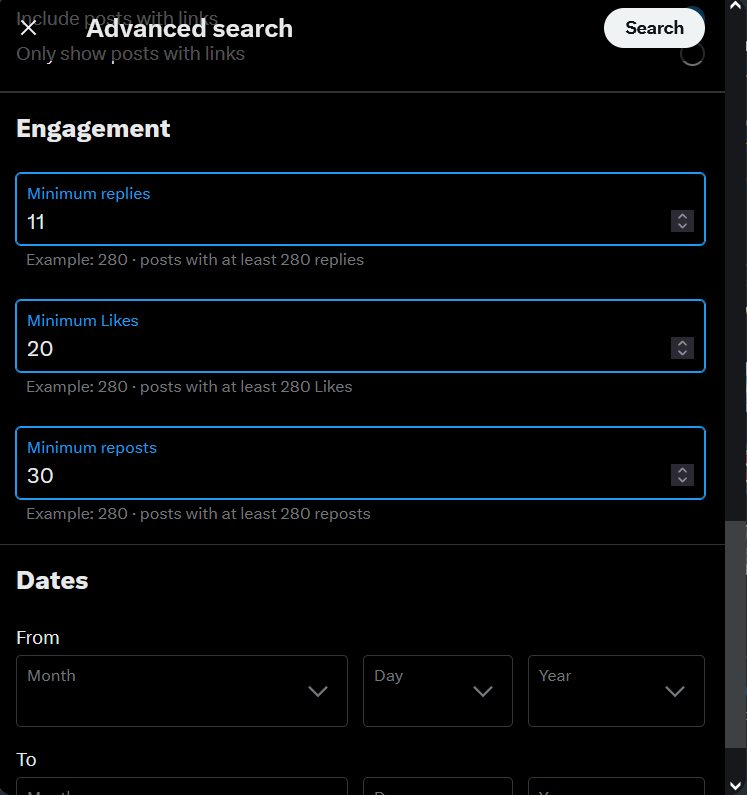
Figure 10 – The engagement section allows the return of posts that meet specific criteria (number of likes, reposts and replies)
Dates section
Use the dates section to search for posts within a specific time frame. This allows users to specify the start and end dates for the returned posts (see Figure 11).
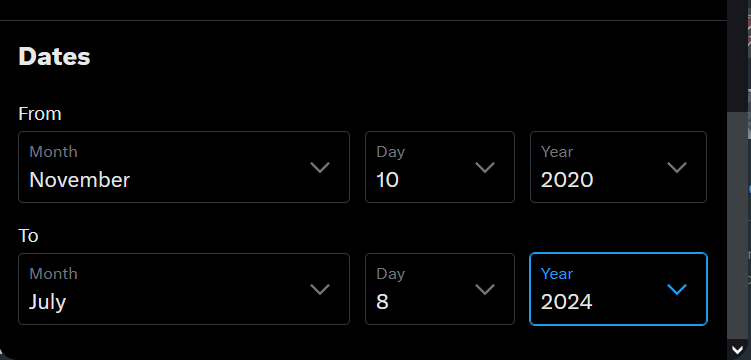
Figure 11 - Search within a specified time frame
Save X search
X allows its users to save up to 25 searches per account. This is a useful feature for OSINT researchers, as they may be executing repeatable searches to monitor a particular account or brand mentions and need to execute these searches continually.
To save your X search:
- Execute your desired search query
- Click on the three dots on the right side of the search bar
- Select "Save search" from the dropdown menu (see Figure 12)
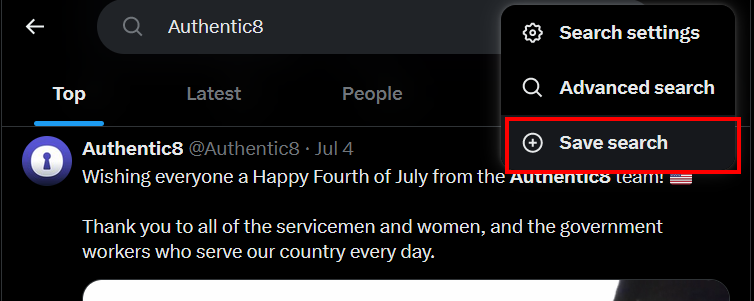
Figure 12 - Save X searches
X advanced search operators
In addition to X’s advanced search feature, users can enter advanced search queries (similar to Google Dorks) in the X search box to return more refined results. Here are some useful X search operators for OSINT gatherers:
Twitter Geo operators
- near:city | The Twitter search operator "near:city" returns posts posted by users located near a specific city. OSINT gatherers can use this operator to find local information, events or discussions. For example, near:London rain will show posts about the rain from users living near London; "breaking news" near:London will return posts containing the phrase "breaking news" from users near London
- near:me | Similar to the near:city operator, however, it returns posts from users located in a location near my location (where X thinks I'm located — learn how to manipulate your location through managed attribution)
- Geocode | This operator is used to find posts in a specific geographical location; for example, festival geocode:52.5200,13.4050,10km tries to find posts about festivals based on their location. The numbers 52.5200,13.4050 represent specific coordinates (somewhere near Berlin, Germany), and the radius is 10km.
To find the geolocation coordinates of any location on Earth, follow these steps:
- Open Google Maps in your web browser
- Navigate to the specific location where you want to get its coordinates
- Right-click on the exact spot to get its coordinates
- The latitude and longitude should appear at the top of the pop-up menu that appears (see Figure 13). Please note the coordinates are displayed in decimal degrees format.
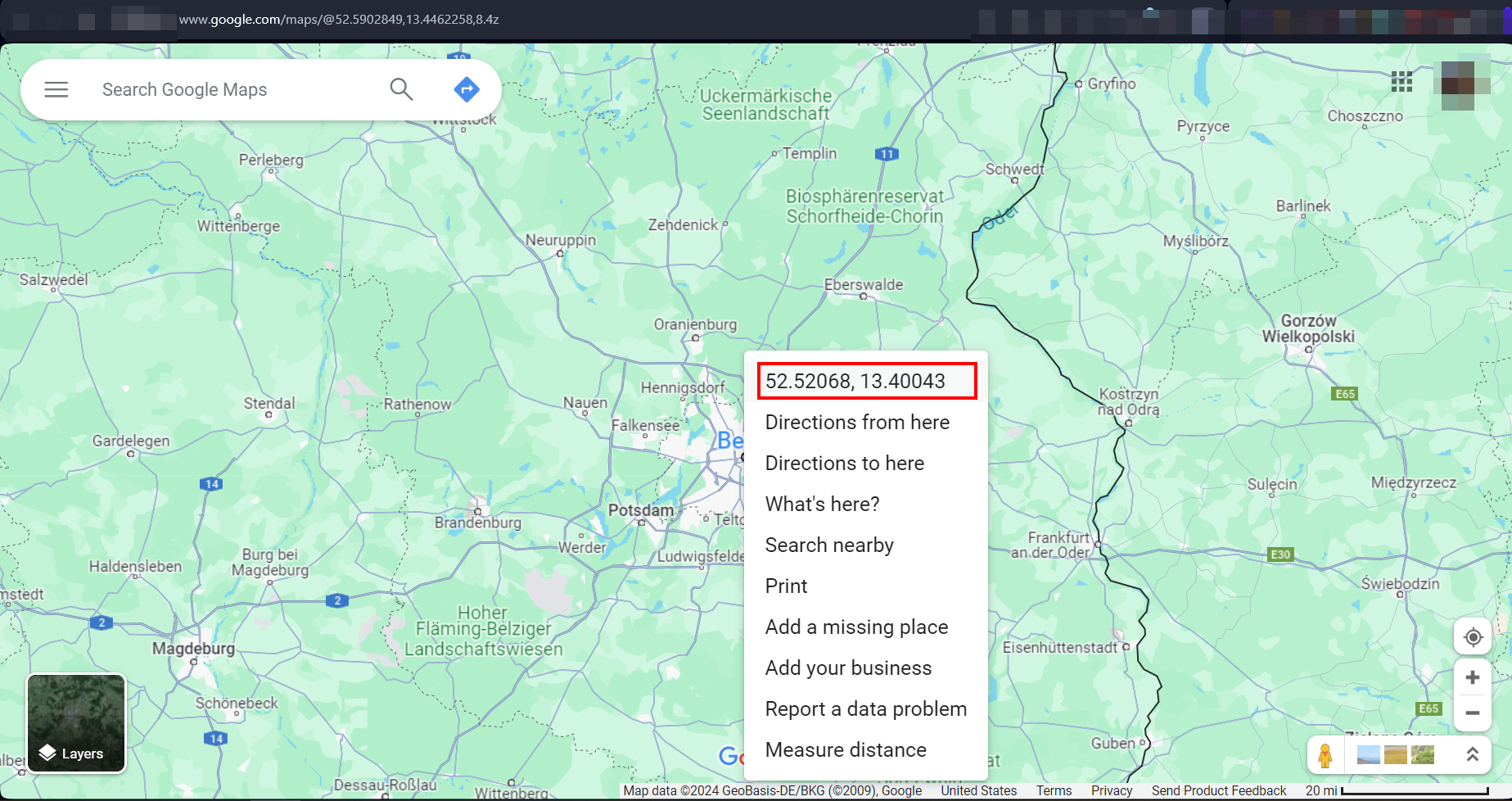
Figure 13 - Google Maps shows the geo-coordinates of any location on Earth
Twitter media search operators
- filter:media | Return posts containing all media types (image, video); for example OSINT filter:media | Return all posts about OSINT and containing media within them
- filter:images | Searches for posts containing images; for example OSINT filter:images | Search for posts about OSINT and containing images (see Figure 14)
- filter:videos | Search for posts containing all video types, including native X videos and external sources such as YouTube; for example OSINT filter:videos returns all relevant posts containing the keyword "OSINT" and a video attached or linked within them
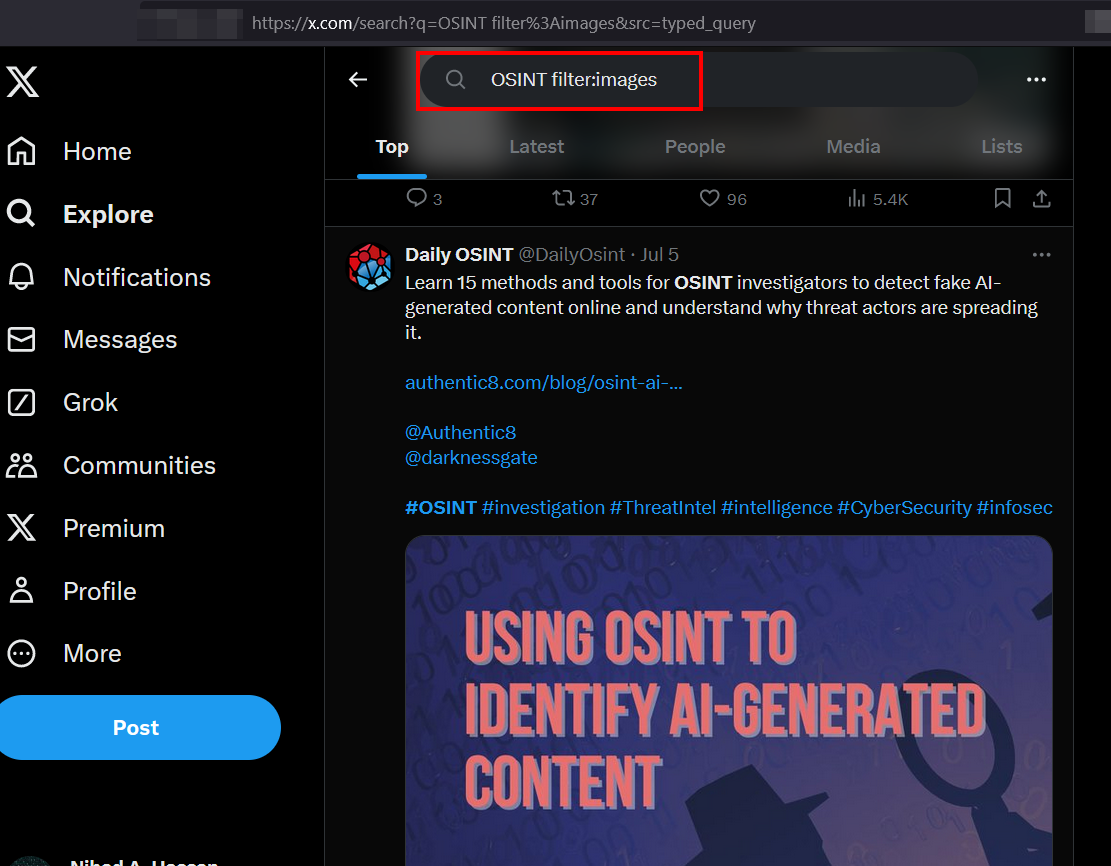
Figure 14 - Using the images filter will return posts containing images within them
Combining many X search operators in one query
It is worth noting that we can combine more than one search operator to return more specific results. For example
- OSINT filter:videos lang:en from:authentic8 OR from:darknessgate | This query will show OSINT video posts in English from either @authentic8 or @darknessgate
- #OSINT from:authentic8 filter:links -filter:replies lang:en | This query finds all English posts from @authentic8 Twitter account containing #OSINT and links, excluding replies (see Figure 15)
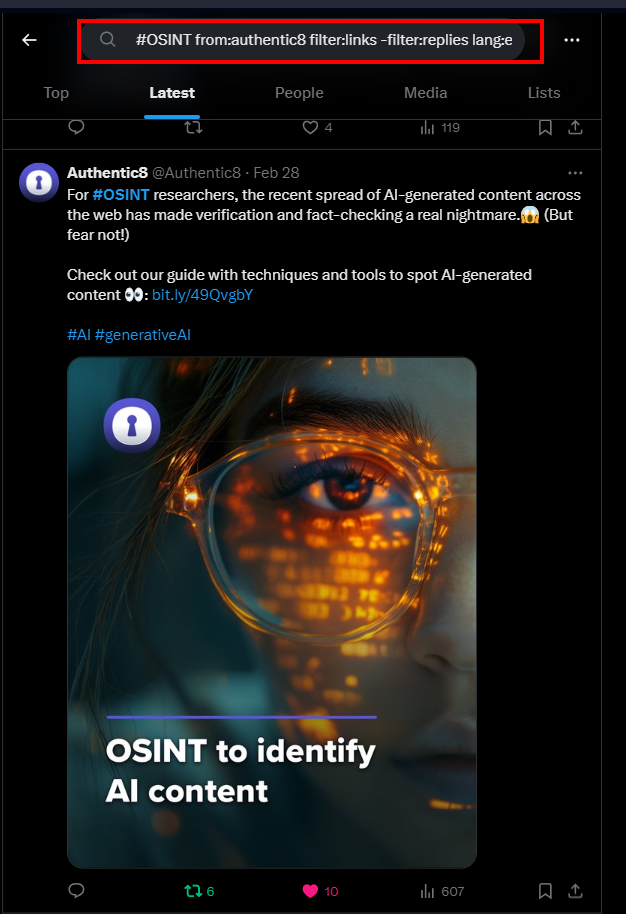
Figure 15 - We can combine many Twitter search operators in one search query
Using Google Dorks to search X
Google Dorks can be used efficiently to search within X. Here are some example search queries:
- site:twitter.com inurl:status "cybersecurity" "vulnerability" -"update" after:2022 | This Dork will find X posts about cybersecurity vulnerabilities without mentioning “update” posted after 2022
- site:twitter.com intext:"data breach" | This Dork will search for posts containing "data breach"
- site:twitter.com intext:"zero-day exploit" after:2023 | This Dork will find posts mentioning "zero-day exploit" after 2023
- site:twitter.com intext:"social engineering tactics" (inurl:media OR inurl:video) -intext:game after:2023 | This Dork will search for posts containing media or videos about social engineering tactics published after 2023, excluding gaming content
- site:twitter.com inurl:lists intitle:"OSINT" -inurl:members -inurl:subscribers | This Dork will search for X lists with "OSINT" in the title, excluding member and subscriber pages
Other tools to search X
Numerous tools exist to help OSINT gatherers automate and expand on X’s native search capabilities. Here are the main ones:
- Twint: This Python tool scraps data from X profiles without relying on X’s API
- Tweepy: This is a Python library that simplifies interacting with the X API, allowing X access via its API to search for posts based on keywords, hashtags, locations and other criteria
- Botometer X (formerly Botometer): This tool is now in archival mode, but it provides access to historical data collected before May 31, 2023; it is used to detect bot X accounts
- Mecodify: This is an open-source tool created to help gather, analyze and visualize X data
- Twitter Video Downloader: Download X videos and GIFs from posts (also check out the Silo for Research Video Download extension)
- NodeXL Basic: A free social network analysis (SNA) and visualization tool, designed as an add-on to Microsoft Excel
- Gephi: An open-source visualization software that runs on Windows, Mac and Linux
In this guide, OSINT gatherers have a comprehensive practical manual into the various techniques for leveraging X as an OSINT resource. We’ve thoroughly covered advanced search operators, AI-powered tools and third-party platforms to enhance data collection and analysis. And we’ve explored X profile elements and given links to numerous online resources to inspect each component, including extracting valuable intelligence from associated websites. We also discussed using Google Dorks to create complex queries and searches within the X platform.
As always, it’s important to employ best-practice tradecraft while OSINT gathering to avoid tipping off targets and, in the case of SOCMINT, appearing in their recommended connections. Learn how Silo can help you remain anonymous while you search by requesting a demo.
Twitter (X) OSINT FAQs
What is Twitter OSINT?
Twitter OSINT is the practice of collecting and analyzing public data from X (formerly Twitter) to support investigations. Analysts examine handles, bios, posts, media, lists, and interactions, then apply operators like from:, filter:, and geocode: plus Google dorks to map identities, verify events, and preserve admissible evidence.
What are the best Twitter OSINT tools?
The best Twitter OSINT tools align to tasks: profile triage (reverse-image tools), search enrichment (advanced operators, Google dorks), data collection (API libraries, scrapers compliant with policy), and analysis/visualization (network graphing). Choose tools that support attribution control, evidence preservation, and clear audit trails for defensible, repeatable workflows.
How do I find OSINT Twitter accounts to follow?
Start with list discovery and mention graphs: search inurl:lists intitle:"OSINT" and use @ mentions of known analysts. Layer from: with topical hashtags, then evaluate bios, posting cadence, and network overlap. Maintain a private list for monitoring, and document why each account merits inclusion in your methodology.
How do X advanced search operators improve OSINT?
X operators narrow noise and surface patterns. Combine from: or to: with lang: and filter:images|videos, add since:/until: and geocode: for time and place, then raise minimum engagement to prioritize signal. Save searches for repeatable monitoring and export hits for archiving and analysis downstream.
Twitter (X) OSINT operators and Google Dorks
Twitter operators:
| Task | Operator | Example | When to use |
|---|---|---|---|
| By author | from: | from:authentic8 lang:en | Scope to a handle |
| Mentions | @ | @authentic8 "OSINT" | Find mentions + keyword |
| Media only | filter:images | videos | media |
| Time bound | since: / until: | "data breach" since:2024-01-01 | Event windows |
| Geo | near: / geocode: | geocode:52.52,13.405,10km "protest" | Place-based triage |
Google Dorks:
| Intent | Dork | Why |
|---|---|---|
| Event claims | site:twitter.com inurl:status "zero-day" after:2023 | Fresh claims |
| Lists | site:twitter.com inurl:lists intitle:"OSINT" -members -subscribers | Curated sources |
| Media only | site:twitter.com "social engineering" (inurl:media OR inurl:video) | Visual evidence |


