Successful detection is crucial in defending organizations against cyberattacks. Learn how your SOC can leverage OSINT to identify phishing sites with this comprehensive guide.
Phishing attacks continue to pose a significant risk for individuals and organizations. Phishing is a type of social engineering (SE) attack that deceives internet users into revealing sensitive information or downloading software to infect their computers with malware for malicious purposes. Cybercriminals find that attacking their targets using phishing attacks is more feasible than breaking security solutions (such as firewalls, intrusion detection systems (IDS) and intrusion prevention systems (IPS)) installed across organizations' IT environments.
Phishing remains the preferred attack vector by cybercriminals to gain unauthorized access to protected resources. According to CISA, over 90% of all cyberattacks begin with phishing. These attacks result in tremendous losses that increase year after year. For instance, the recent FBI Internet Crime Report found that phishing scams cost the USA more than $12.5 billion in losses in 2023.
To stop the ever-increasing number of phishing attacks and other online scams, security professionals can leverage a plethora of tools, techniques and online services that are available publicly to discover and investigate phishing websites. This collection of methods is collectively known as open source intelligence (OSINT). OSINT provides a powerful arsenal of resources that can be employed to uncover cybercriminals' complex web of deception. Let’s dive in.
The anatomy of a phishing website
Before I begin describing the OSINT techniques for discovering phishing websites, let me first describe in some detail the general characteristics of a phishing website.
Phishing websites are intentionally designed to deceive unaware users into revealing sensitive information, such as online account login credentials, financial data, or other personal details. The following characteristics describe the general anatomy of a typical phishing website:
Domain name
Threat actors commonly utilize deceptive domain names that closely resemble the legitimate websites they intend to impersonate. For instance, they may use techniques such as typosquatting to create a domain name that is very similar to the target. For example: "www.authentic18.com" (adding the number 1 to the domain name) to mimic the legitimate "www.authentic8.com" domain.
Visual appearance
Phishing websites are designed to mimic the look and feel of legitimate websites. For instance, phishers copy logs, color schemes and layout elements to completely impersonate the target website and trick users into believing they are interacting with a genuine website. Phishers commonly clone target websites using automated tools such as HTTrack to create identical copies of them and upload them to their hosting space.
Obfuscated code
The source code of phishing websites may contain hidden code designed to conceal malicious behavior, such as data exfiltration. For example, attackers may conceal JavaScript code that contains encoded functions to capture user input and send it to attackers' remote servers.
Use redirects
Phishing websites may use hidden JavaScript routines to redirect unaware internet users to other destinations to steal their credentials or install malware. These redirects are known as web redirects and hackers implement them using two ways: client-side redirects (using JavaScript) and server-side redirects (using HTTP status code such as 301 or 302).
Use URL shortening service
Phishing websites may try to hide the actual destinations of their links using a free URL shortening service. For example, a phishing website may display a shortened URL which, when clicked, redirects the user through the URL shortening service to the final malicious webpage. Some examples of free shortening services include ShortURL and TinyURL.
Psychological tactics
Phishing websites commonly use threatening language to make users feel afraid to act promptly without thinking. For example, a malicious website impersonating another legitimate website may display a pop-up window asking its users to log in and change their password instantly to avoid losing access to their account – such as a banking account.
Detecting phishing websites using OSINT techniques
OSINT provides a rich library of tools, tactics and methods to identify phishing websites. Here are the most useful ones:
Domain name analysis
When we are suspicious of a phishing website, the first thing we need to do is analyze its domain name:
WHOIS records
WHOIS records show different information about domain names, such as:
- Registrar: the entity where the domain name is registered
- Registrant: information about the person/organization that registered the domain, such as their name, email address, mailing address and phone number
- Administrative contact: contact information for the entity responsible for managing the domain registration
- Technical contact: contact information for the entity responsible for handling technical issues related to the domain
- Name servers: the DNS servers of the domain
- Creation date: the date when the domain was initially created
- Expiration date: the date when the domain registration will expire
- Updated date: the last time the domain registration information was updated
However, phishing websites hide their WHOIS information to avoid revealing who is behind them. They use the following tactics to conceal their WHOIS information:
- Make it private: Website owners can pay a small annual fee to keep their domain information private and avoid making their information publicly available in the WHOIS database. If you encounter a newly created domain name that makes their WHOIS information private, this is a red flag that this website could be used for phishing or other malicious purposes.
- Register under fake or stolen identities: Phishers often use fake or stolen identiies to register their phishing domains. For example, there are many free online services for generating completely fake personal profiles (including personal photos), such as: Createfakeperson (generate personal photos based on criteria provided by users), Fakepersongenerator (generate complete fake personal information including email, education and employment) and Fakenamegenerator (generate fake people profiles for 37 languages and 31 countries (see Figure 1).
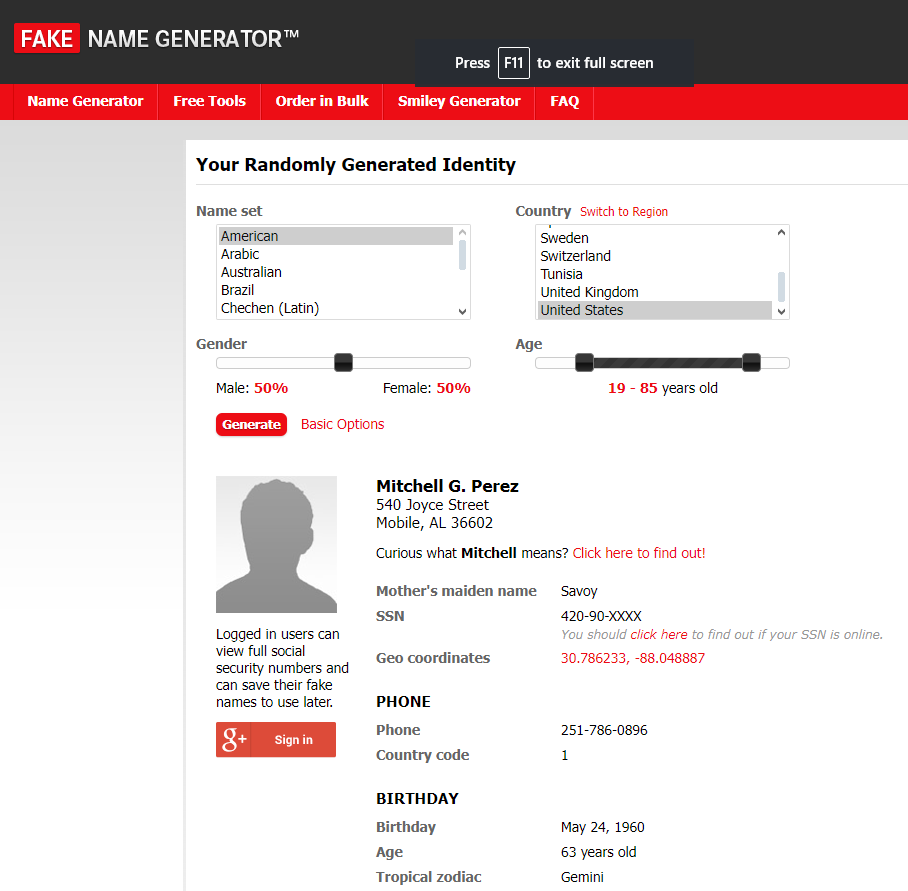
Figure 1 - Generate fake personal profiles
Website content analysis
After analyzing the domain name, we can move forward to inspect the content of the suspicious website. Here is what we should look for:
Text analysis
The first thing we need to do is analyze the text that appears on the suspicious website. Phishing websites tend to use urgency and fear tactics to force unaware internet users to feel panic and act promptly without thinking. It is also common for phishing sites' texts to have spelling and grammatical mistakes and to borrow large amounts of data from other legitimate websites. Here are examples of urgent phrases used in phishing websites:
- Urgent action required
- Your account is suspended
- Immediate attention needed
- Security breach detected
- Verify your account now
- Unauthorized access detected
- Your account will be closed
- Confirm your identity immediately
- Limited time offer
- Act now to avoid penalties
- Emergency security alert
- Update your information now
- Your account has been compromised
- Last chance to secure your account
- Avoid account termination
- Critical security warning
- Immediate password reset required
When a suspected phishing website uses correct grammar and spelling to describe its services, then you can copy and paste a complete paragraph of text into Google to find where similar text appears. WayBack Machine should also be used to check previous phishing website versions.
URL analysis
Phishing websites use different tactics to conceal the true destination of their links. For example, the link's visible text does not match its true destination. We can hover over the link using our mouse to reveal the actual destination (see Figure 2).
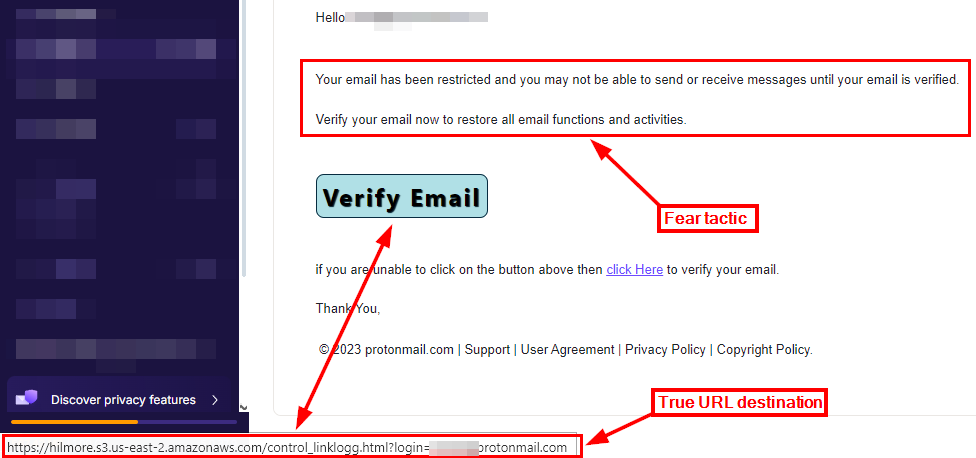
Figure 2 - Hover your mouse over suspicious links to reveal their final destination
There are online services for detecting phishing or fraudulent links. Some services are now powered by artificial intelligence (AI), which provides an excellent capability to perform real-time phishing link checking. Here are some reputable online URL phishing checkers:
- EasyDMARC: paste suspicious links and emails to see if they are malicious and point to a phishing website
- Norton Safe Web: check if the sites you visit are safe according to their ratings and community reviews
- Skysnag: detect if a URL has a phishing link or is malicious
- IPQS malicious URL scanner: check for phishing links and malware domains
Build multi-site searches in Silo to run the same custom search across several websites. Learn how in this demo >
Form analysis
Phishing websites contain forms to capture users' input (sensitive information such as login credentials or credit card details) and send them to the attacker's server. It is common for phishing websites to ask for sensitive information that is not usually requested via web forms, such as your Social Security number. Besides, phishing sites may request such details over a non-secure HTTP connection.
Image analysis
Phishing websites use stolen images and logos from other websites to make their appearance more legitimate. Stolen images/logos commonly have less resolution than original images. Some phishing websites sometimes use images with watermarks (see Figure 3) acquired from image repositors' websites such as Pixabay and Unsplash. We can track the origin of images (where they appeared before) using reverse image search. Here are some links to do this:
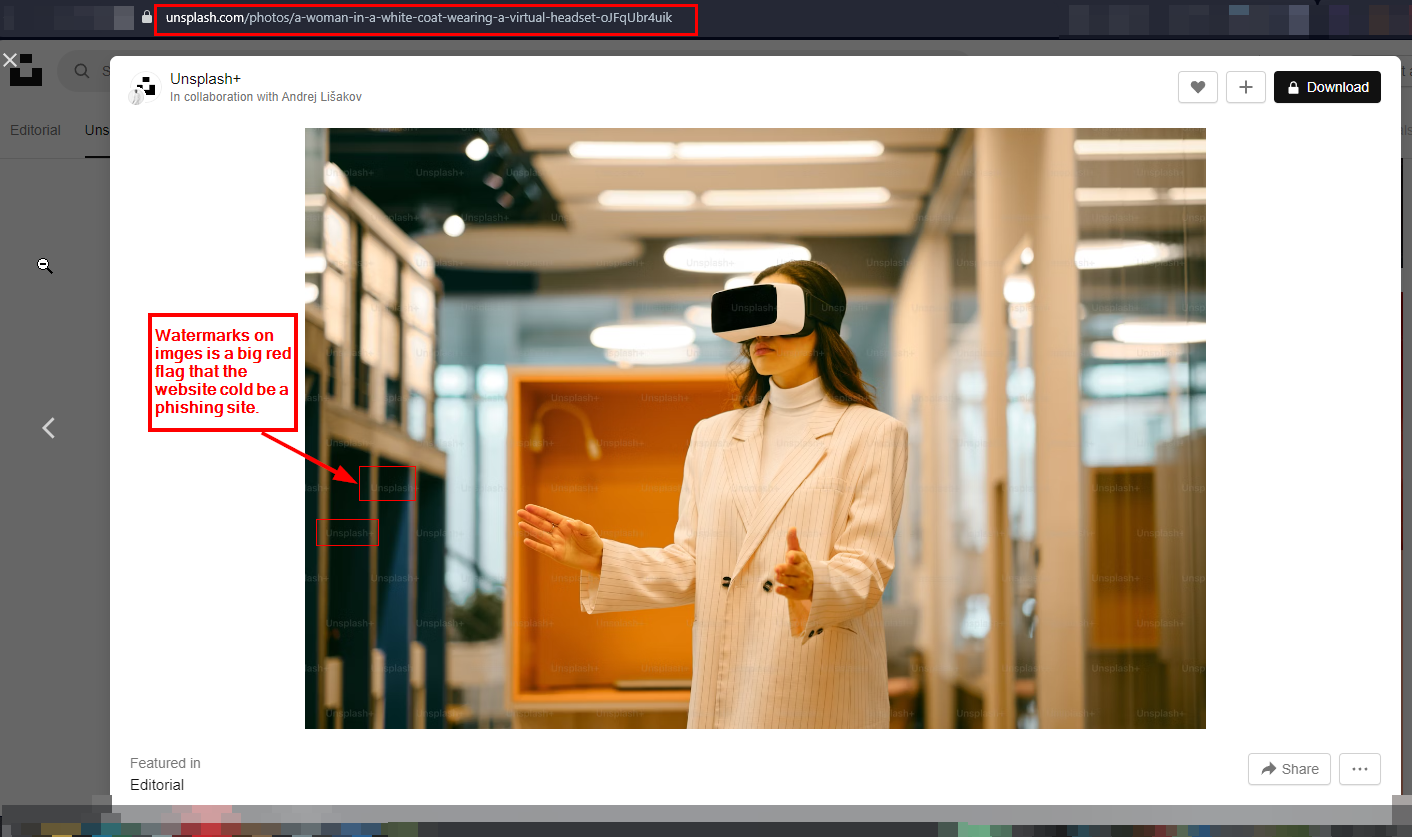
Figure 3 - Using images with watermarks is a phishing red flag — reputable websites purchase their images and logo
Examine social media profiles
The absence of social media links on a website is a red flag. Nowadays, all companies have a presence on major social media platforms, such as Facebook, Instagram and X (formerly Twitter). Some phishing websites may have a presence on social media platforms; if this is the case, we should inspect these accounts to identify if they are fake. Here are some signs to identify fake social media accounts associated with phishing websites:
- Recently created: Phishing accounts are generally newly created, with activity after the phishing campaign began.
- Suspicious account names: Account names may be misspelled to resemble the legitimate brand or company they're impersonating. Check out my typosquatting article for a comprehensive guide on how typosquatters misspell domain names to mislead unaware internet users into falling victim to phishing attacks.
- Not verified: Legitimate brands and companies typically have verified badges on their social media accounts, while phishing accounts cannot verify their accounts because they are fake.
- Low follower/following/like counts: Phishing accounts have a low number of followers.
- Inconsistent style: The phishing account picture, cover photo and other branding elements in the feed may differ from the legitimate brand they're impersonating.
- Suspicious links: Phishing account posts may contain links to phishing websites or other suspicious URLs that contain redirects. These links are often disguised as legitimate links using shortening services.
These were some techniques to reveal phishing websites. There are more tactics OSINT gatherers can leverage to detect phishing websites and their associated social media accounts, which we will cover in future articles.
How Silo fast-tracks phishing incident response
While we’ve discussed many details that can be gleaned from a suspected phishing website without accessing it directly, sometimes you have to go right to the source. Silo Workspace provides an isolated, anonymous browsing environment to safely access phishing websites and experience them as would a phishing target.
- Navigate to the suspected website via a cloud-based remote browser to protect your machine and network from malware
- Conduct a visual inspection to determine if the site is convincing, malicious, attempting to harvest credentials; screen capture your findings
- Manipulate your user agent string and point of presence to see if the page reacts (i.e., determine what phishing targets may experience on the page)
- Use DevTools to analyze the HTML (Network, Sources, Inspect and Console tabs)
- Identify redirects (domains and URLs) to be blocked; screen capture and annotate Javascript and CSS to understand what the page is loading
- Download code into Silo Drive, and transfer it safely to a sandbox to analyze the phishing kit
Discover all that Silo can do for your SOC team and start a 30-day free trial today.
Tags Cybersecurity Phishing/malware SOC

