When performing incident response to APTs, balance priorities of fully rooting out adversaries and limiting disruption to the business.
When an organization suffers a compromise by an advanced adversary, incident responders leap into action to detect, contain and eradicate the adversary’s presence in their systems. Incident responders not only need to remove the adversary’s initial back door, but they must also comb through the entire infrastructure for any other back doors that were installed post-breach. For incidents with lengthy incident response processes — such as those associated with the recently uncovered SolarWinds compromise — CIOs and CISOs face difficult decisions to balance immediate response needs, long-term security and business continuity.
Decision-makers — fearing ongoing data loss of unknown origin — may elect to sever the organization's connection to the internet while incident responders scour networks for signs of an adversary. However, this option comes with tremendous business impact and may be impractical if not impossible. With a zero-trust browsing model, organizations can maintain business continuity while preserving security and enabling effective incident response.
Yes, it is indeed possible to “stop the bleeding” and gain much needed time for a thorough incident response — all while allowing users continued access to the internet.
Having spent most of my career working in or standing up security operations centers, I understand the pressures associated with incident response, including incidents involving advanced persistent threats.
Most often, successful data breaches and other compromises have three components in common:
It’s paramount to enable efficient and thorough incident response while maintaining continuity of operations. By breaking an adversary’s two-way communication, cyber defenders can worry less about data exfiltration and can focus efforts on detecting, mitigating and eradicating the adversary’s presence.
As a remote web browser within a secure cloud-based container, Silo allows validated users to safely interact with web content in a familiar browser interface while keeping external code and data off of the endpoint. With trusted users browsing the web via Silo, organizations can effectively block all unverified outbound communications on port 80 and 443 (and more). This severs the adversaries’ communication channel, prevents further data loss and greatly reduces the scope of what incident responders must investigate.
Deploying SIlo across an enterprise takes mere hours (not days or weeks), even for large enterprises with thousands of users. When deployed as described here, it’s a force-multiplier for incident response to an ongoing network compromise:
Deploy the Silo browser across the enterprise, installing as any other web-browser client. Because of its familiar browser interface, no user training is required — it looks and feels like other popular web browsers.
Configure your organization’s web proxy or gateway to direct all outbound web requests through Silo. Silo integrates easily with any standards-based web gateway or proxy appliance.
Gain breathing room in incident response while enabling business continuity.
Even after incident recovery, organizations benefit from Silo as part of a modern, zero-trust architecture to isolate the trusted from the untrusted.
Even the most capable cybersecurity professionals can be overwhelmed by the large volume of internet-based malware, suspicious web traffic and general noise. By blocking all external web connections other than those to the Silo browser service, security teams effectively deny all but trusted and verified relationships. Relief from web-based attacks continues to offer tremendous benefit to security operations center (SOC) teams, which recoup time and resources that can instead be used to hunt malicious insiders, supply chain attacks and other advanced threats.
The Silo platform shifts the browser from a critical vulnerability to a center of administrative governance and control. In addition to secure web browsing, Silo enables enhanced auditing, data loss prevention, and integration with other enterprise security investments — giving cyber defenders additional insight and control of data security.
With a career spent focusing on incident response and the SOC, I know the difficulty and frustration of preventing and detecting attacks from well-resourced adversaries, and I wish that I would have rethought the concept of web browsing years ago. It’s incredibly simple in hindsight, and I hope that others can benefit from this message.
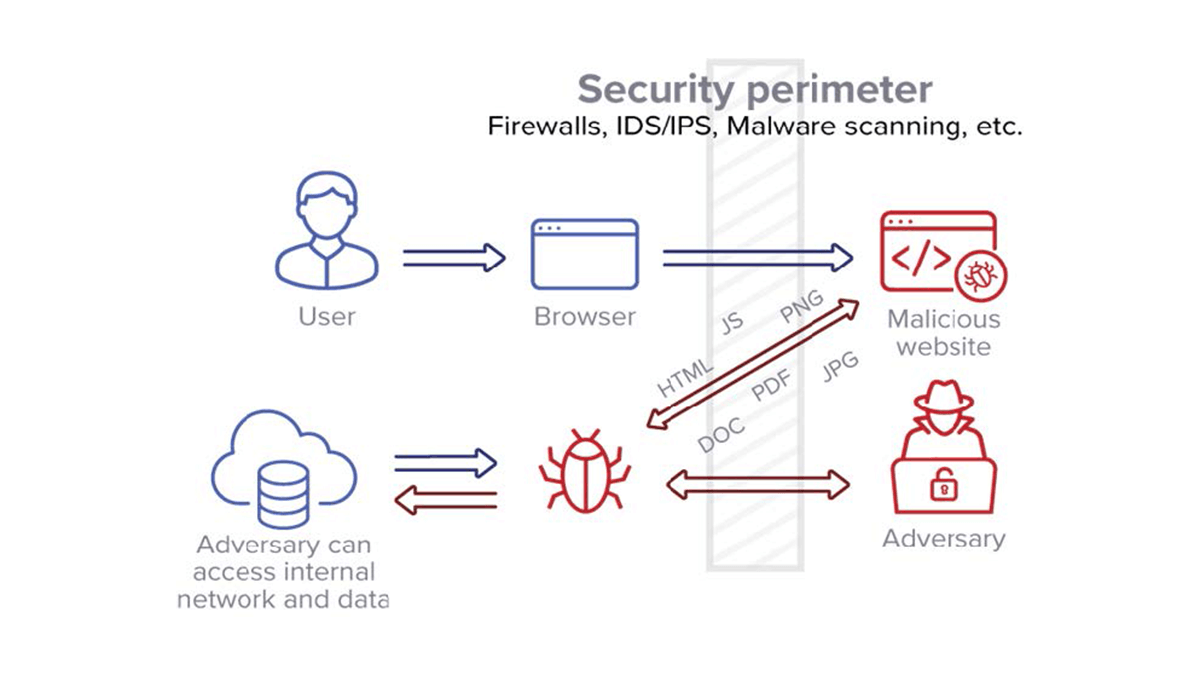
Legacy browsing architecture can still allow an adversary to access the internal network and data.
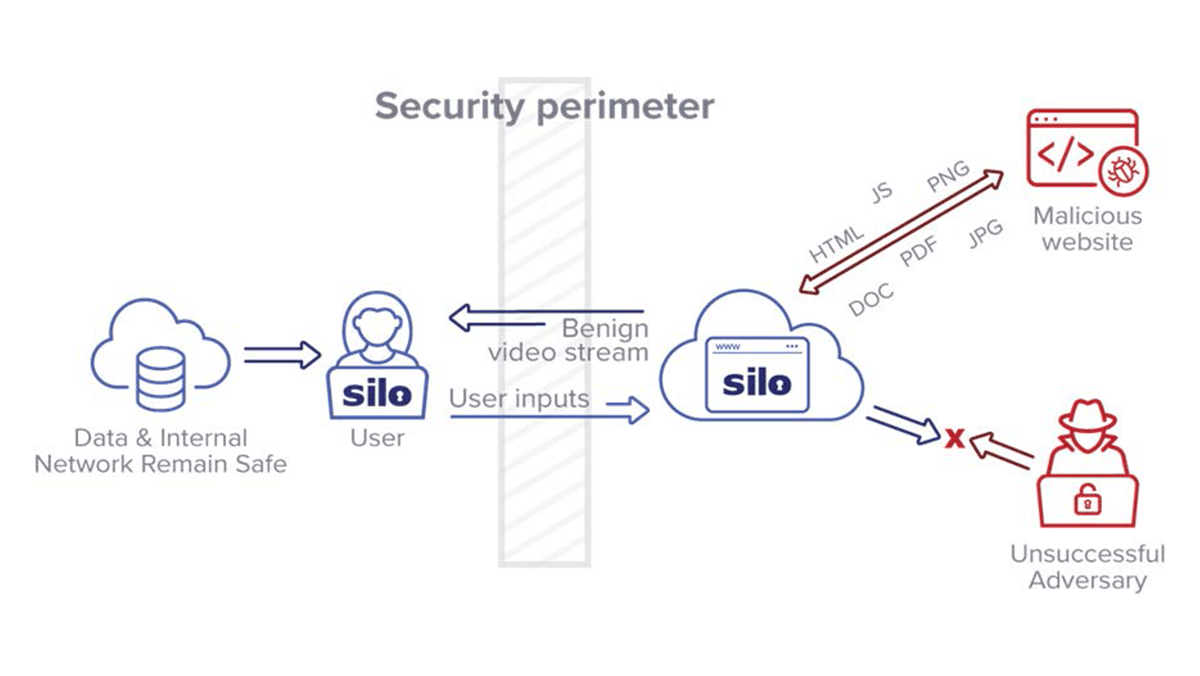
The Silo Web Isolation Platform guarantees 100-percent isolation from the web and the user, keeping the internal network and data safe.
Through the Silo Web Isolation Platform, organizations can rapidly implement a real zero-trust web browsing architecture while preserving a familiar web browser interface to end users. It also integrates incredibly well with the mission of audit, incident response and data loss prevention teams, keeping CIOs, CISOs and users happy.
To get started on securing your organization’s web browsing, contact Authentic8 here >