Discover essential tools and techniques to improve OSINT, surface, and dark web investigations safely, efficiently, and anonymously.
For investigators scouring the web for clues, time-saving tools and tips can make the difference that leads to a successful inquiry. There are several tools that can unlock the data lurking in the background and help you find the breakthrough you’re looking for in your search. These tips can help with easier and safer ways to search the internet — including the dark web — and discover who may be behind nefarious content.
With these simple tools, investigators can find site owners of surface sites, see bitcoin transactions and discover details behind photos on the web.
Tools for investigating site ownership and history
When searching for information on the surface web, the websites themselves hold several keys about who might be behind the content. (On the dark web, you won’t be so lucky as site operators and owners are anonymous.) These services provide user-friendly protocols for retrieving that information from the databases that house domain data.
Identify site owners with WHOIS
WHOIS is a lookup protocol that reveals who owns a domain — including registration details, hosting location, and contact data. Investigators use WHOIS to uncover potential links between sites and operators.
By combining WHOIS query and response protocols with additional search tools, investigators can uncover more information.
Inspect site details with URLscan.io
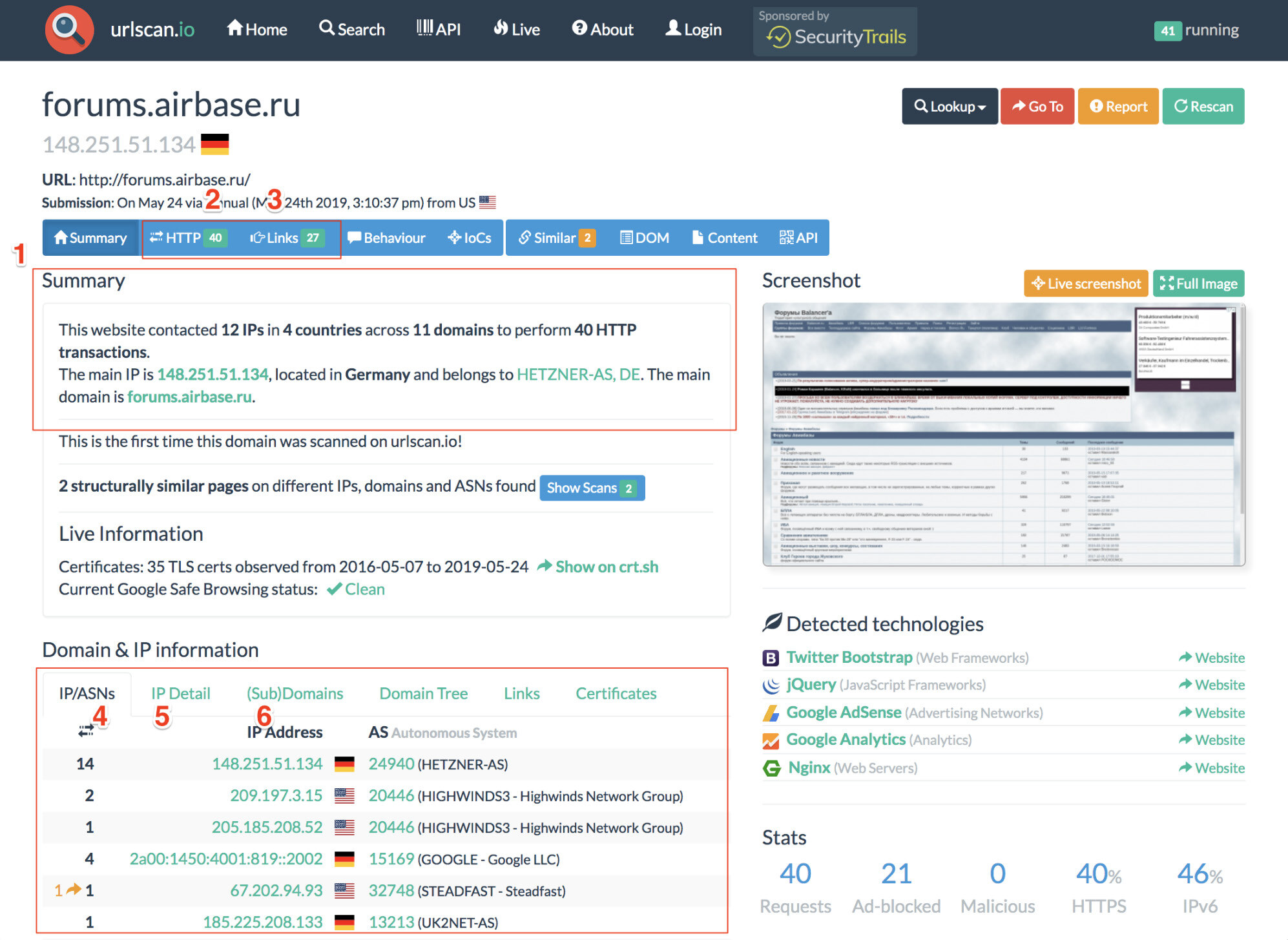
URLscan.io is a service that provides the end user with analysis of the IP address information and HTTP connections made during the site’s retrieval. The result panels include a top-level survey of what country the site is hosted in, what links are included on the main page and the IP location details. Details about how many subdomains it contains and what external links it contains can be found as well.
Through WHOIS analysis, hosting details can also be discovered. This can help lead investigators to find servers that host multiple sites or share webmasters, as well as valuable owner information.
Investigate domain ownership with DomainIQ
DomainIQ operates similarly to URLscan.io and can provide identifying details about the site owner, host and what other pages they may be operating.
Using advanced search engine techniques
By using advanced search engine techniques, we can search the identifying data from WHOIS records (such as emails, names, servers or IP addresses) and find additional clues or information that may be lurking on other sites.
Carbon Date
Carbon Date uses the advanced search engine technique of “carbon dating” that analyzes a website and gives the earliest known creation date of the page. You can also view previous versions of the page, including the first known scrape through archive.org.
Google Dorking
“Google Dorking'' is the process of using advanced search parameters on Google. There are several techniques that can be used ranging from simple to more advanced. Some of the most common Bolean logic search operators are using quotes to search for exact phrasing or the dash symbol (-) to exclude specific words. You can also use Google to search specific file types or recent caches of a specific site.
These techniques can be used to find identifying information about moderators or search a site for identifying pieces. It can also be used to string together sites sharing specific information.
Common Google Dorking techniques include:
- Intitle: identifies any mention of search text in the web page title
- Allintitle: only identifies pages with all of the search text in the web page title
- Inurl: identifies any mention of search text in the web page URL
- Intext: only identifies pages with all of the search text in the web page URL
- Site: limits results to the specified file type
- Filetype: limits results to only the specified file type
- Cache: shows the most recent cache of a site specified
- Around (X): searches for two different words within X words of one another
All of these tools can help investigate ownership and hosting information about the sites relevant to your research. Using WHOIS records and advanced search engine techniques can reveal identifying details on the host, moderator and IP, as well as what other sites might be sourced from the same owners.
Learn more about WHOIS records analysis, advanced search engine use and real-world examples of these techniques in action in our flash report, Investigating Site Ownership and History >
Cryptocurrency and its role in money laundering
Cryptocurrency, once a fringe anti-big banking trend, has taken a sharp rise in popularity over the last decade. According to Chappuis Halder, it has now grown to more than 69 million users worldwide.
The decentralized privacy offered by Bitcoin and its crypto competitors have also become popular as money laundering tools. The anonymity of cryptocurrency provides cover for traders and a convenient way to purchase illicit substances. When tracking cybercriminals or potential hackers, the flow of currency behind major leaks or bad actors could prove insightful.
Bitcoin Who’s Who
Bitcoin Who’s Who allows investigators to search for identifiers from bitcoin blockchains. If a bitcoin address holds any identifying information, investigators can find it here. It also offers reports on scam alerts connected to the account. You can check the wallet balance, owner information and set up transaction alerts to notify you when exchanges with the account are made.
Other fields of interest in a Bitcoin Who’s Who report include the last known IP address used in a transaction and any website where the address has appeared. This can help identify if the address is being used for sinister purposes.
Blockchain Explorer
Blockchain Explorer lets researchers search blockchain details of major cryptocurrencies including Bitcoin and Ethereum. Explorer captures historical prices, the most recently mined blocks, the mempool size of unconfirmed transactions and data for the latest transactions. Researchers can search by block number, address, block hash, transaction hash or public key to find out more information on cryptocurrency transactions.
See how to obtain Bitcoin address reports in our flash report, Crypto Money Laundering on the Rise >
Using Exif data to gather intel
Behind every image on the internet — on the surface as well as dark web — is valuable data which holds information about where the photo was taken, when, the file size and often what specific camera was used. These details are captured in exif — or “exchangeable image file format” — data. This hidden information can provide helpful leads for investigators.
By using tools like FotoForensics, researchers can analyze the Exif data on photos to help inform investigations.
FotoForensics
FotoForensics provides detailed reports on the Exif data embedded in photos. There are two ways to glean a report: Users can upload the saved image directly or paste the image URL.
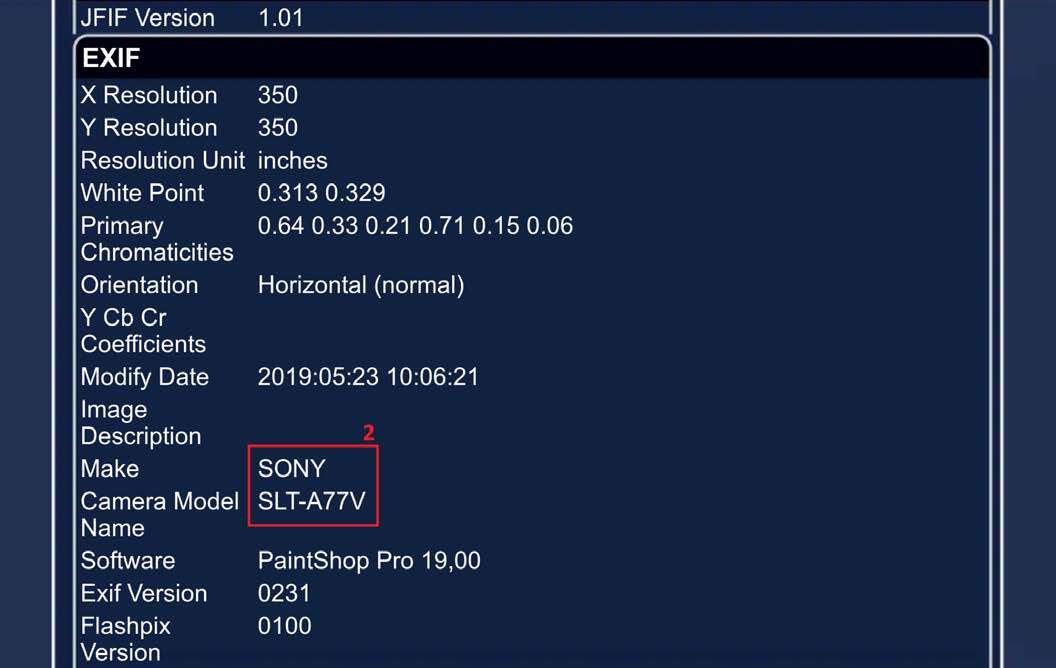
The report provided may include the geolocation in the form of coordinates. (These coordinates plugged into Google maps can provide the exact pinpoint on a map.) It also includes the time stamp and camera make and model. This analysis can provide a wealth of data about otherwise anonymous pages.
See a real-world scenario of using Exif data provided by FotoForensics to decipher intelligence regarding a cargo ship image >
When conducting an investigation, analysis tools and OSINT techniques can help greatly improve the efficiency and effectiveness of research. By researching site owners, investigators may learn about patterns of activity; cryptocurrency analysis can help understand the context for how and when money is being exchanged; and Exif data can help provide context and intel behind anonymous images.
Who you’re looking up can look back
In any investigation, remaining anonymous is imperative. Any time you visit a site, some level of detail is disclosed to that site's owner — even on the dark web.
If you think the dark web is fully anonymous, think again. Read the blog: 3 things to consider before you start your dark web investigation >
While the tools described in this post should be safe to use, collecting the information you feed them carries risk. By visiting an investigative target’s site, they could learn a range of details about your digital fingerprint — your location, preferred language, device details, browsing history, etc. The combination of these details is highly specific and, when pieced together, could unveil your actual identity and the purpose of your investigation. And with that information, your target could feed you disinformation, go into hiding or retaliate against you.
So to protect your investigation, your organization and yourself, investigators must be prepared to control the details of their digital fingerprint. With this capability, proper tradecraft and the tools and techniques above, you can improve the quality and efficiency of investigations without increasing its risks.
To learn more tips and techniques for open and dark web research, as well as how Silo for Research can aid safe and anonymous investigations, download our guide.
More from our dark web blog series:
- Understanding the dark web and how it can aid your investigation: What is the dark web and how does it vary from the internet most of us use everyday? Which darknet should I use for my investigation? And how can I access it safely?
- Leveraging the dark web in online investigations: Why you should utilize the dark web in your investigation, where to begin and how to protect yourself (and your company) along the way.
- 3 things to consider before you start your dark web investigation: When trying to determine if you should begin a dark web investigation, ask yourself these three questions concerning content, risk and precautions.
- Best practices for creating a dark web access policy: Protect your company and employees by creating a dark web access policy to set protocol for investigations to mitigate security and legal challenges.
- 4 things you shouldn’t do on the dark web: Avoid a world of trouble by following these four simple recommendations of what not to do on the dark web during online investigations.
Tools for surface and dark web research FAQs
What are the best dark web investigation tools?
Top dark web investigation tools include URLscan.io, DomainIQ, Blockchain Explorer, Bitcoin Who’s Who, and FotoForensics. These help uncover ownership, crypto flows, and image data safely.
How can investigators research the dark web safely?
Investigators should use isolated browsers, VPNs, and identity-masking tools like Silo for Research to protect anonymity during dark web investigations.
What OSINT tools help with dark web research?
WHOIS, Google Dorking, Carbon Date, and URLscan.io support dark web research by helping investigators collect open-source intelligence without exposing identity.
Tags Dark web basics Dark web research

