Stay up to date the most pressing cyber threats, emerging trends and what they mean for enterprise security, critical infrastructure and global risk.
9 Aug – 15 Aug, 2025 | TLP: CLEAR
EXECUTIVE SUMMARY
The August 9-15, 2025 timeframe includes state-sponsored infrastructure attacks and sophisticated criminal operations consistent with the continuing severity of the threat landscape. This report highlights several high-priority intelligence items requiring immediate executive attention, including active exploitation of managed service provider infrastructure, zero-day vulnerabilities in enterprise identity systems, and demonstrated state control over critical infrastructure.
Multiple critical vulnerabilities created cascading organizational risks, with N-able RMM platform compromise affecting managed service providers and their downstream customers, FortiSIEM active exploitation targeting security monitoring infrastructure, and Microsoft Kerberos zero-day enabling complete domain takeover. State-sponsored actors demonstrated operational control over Norwegian water systems, while criminal groups rapidly adopted nation-state techniques including custom EDR evasion platforms and sophisticated driver-based attacks.
CRITICAL INCIDENTS
1. N-able N-Central RMM Platform Mass Compromise
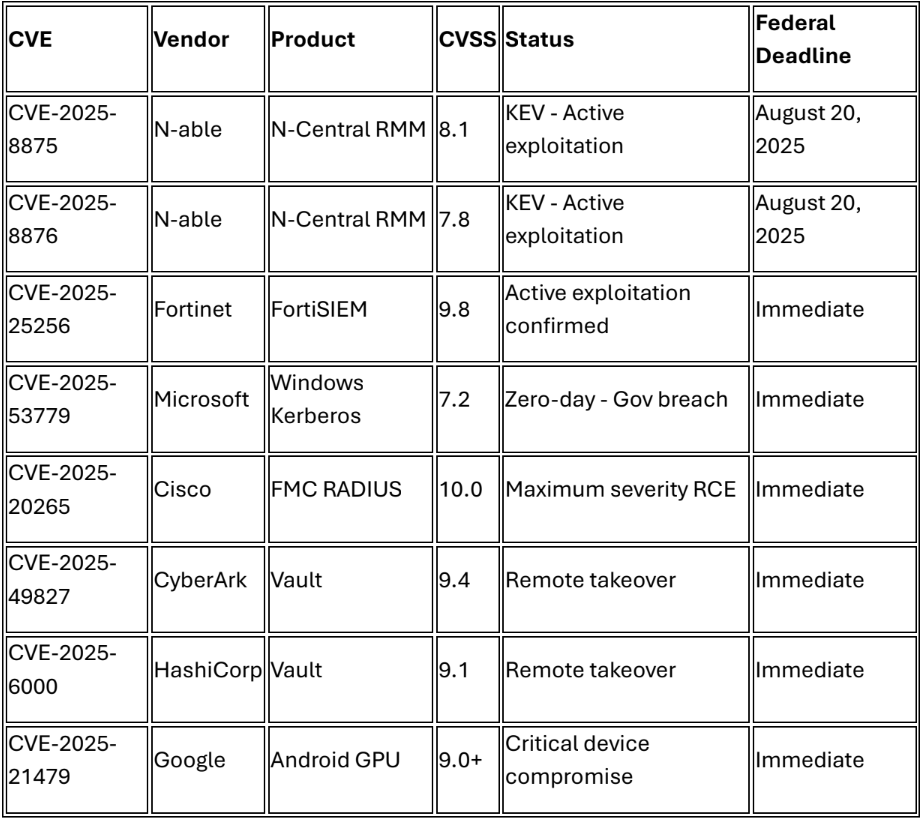
CISA added CVE-2025-8875 (insecure deserialization) and CVE-2025-8876 (command injection) to the Known Exploited Vulnerabilities catalog on August 13, confirming active exploitation of N-able N-Central RMM platform affecting managed service providers nationwide.1 Federal agencies must remediate by August 20, 2025, while MSPs face cascading risk to all downstream customers. The vulnerabilities affect versions prior to 2025.3.1 and enable authenticated attackers to achieve remote code execution on management infrastructure.2
Analyst Comment: MSP compromise creates exponential risk multiplication, potentially affecting hundreds of organizations per compromised provider.
2. FortiSIEM Critical Security Infrastructure Under Attack
CVE-2025-25256 enables unauthenticated OS command injection in FortiSIEM with practical exploit code discovered circulating in criminal forums.3 The vulnerability affects core security monitoring infrastructure used by enterprises for threat detection, creating operational blind spots during compromise. Fortinet confirmed active exploitation attempts with attackers targeting TCP port 7900 to deploy persistent backdoors on SIEM platforms across multiple organizations.
Analyst Comment: Compromise of security monitoring platforms enables attackers to operate undetected while manipulating security alerts and forensic evidence.
3. Microsoft Kerberos Zero-Day Domain Infrastructure Takeover
Microsoft disclosed CVE-2025-53779, the "BadSuccessor" Kerberos vulnerability enabling complete Active Directory compromise through relative path traversal attacks on delegated Managed Service Accounts.4 Research demonstrated privilege escalation from any authenticated user to domain administrator, affecting all Windows domain environments. Canada's House of Commons suffered confirmed exploitation on August 9, exposing employee data including names, job titles, office locations, and email addresses.5
Analyst Comment: The combination of public disclosure and confirmed government exploitation demonstrates immediate domain infrastructure risk across all sectors.
4. CyberArk and HashiCorp Vault Critical Authentication Bypass
Fourteen vulnerabilities disclosed in enterprise secure vaults enable remote vault takeover without credentials, affecting CyberArk (CVE-2025-49827) and HashiCorp Vault (CVE 2025-6000) systems.6 The vulnerabilities include authentication bypasses, privilege escalation, and remote code execution flaws that compromise corporate identity system infrastructure. Responsible disclosure occurred in May 2025 with patches now available for immediate deployment across all vault installations.
Analyst Comment: Vault compromise enables attackers to access all stored credentials and secrets, creating complete organizational identity infrastructure failure.
5. Norwegian Critical Infrastructure Demonstration Attack
Pro-Russian threat actors successfully demonstrated operational control over Norwegian Bremanger dam water flow systems, releasing 7.2 million liters in April 2025 with disclosure delayed until August 14.7 Norwegian PST confirmed attribution to state sponsored groups with video evidence published on Telegram featuring pro-Russian watermarks. The attack represents demonstration of capability rather than maximum damage intent, indicating preparation for future escalation scenarios.
Analyst Comment: Demonstration attacks against critical infrastructure indicate state preparation for strategic escalation scenarios against Western targets.
6. Cisco Maximum Severity RADIUS Infrastructure Vulnerability
CVE-2025-20265 represents maximum severity (CVSS 10.0) unauthenticated remote code execution vulnerability in Cisco Secure Firewall Management Center RADIUS subsystem.8 Path traversal enables arbitrary shell command injection on FMC Software releases 7.0.7 and 7.7.0 with RADIUS authentication enabled. The vulnerability affects critical network security infrastructure with immediate emergency patching required for all affected systems.
Analyst Comment: Maximum severity vulnerabilities in network security infrastructure create immediate organizational compromise risk.
ACTIVE THREAT ACTORS
RomCom (Russian APT Group)
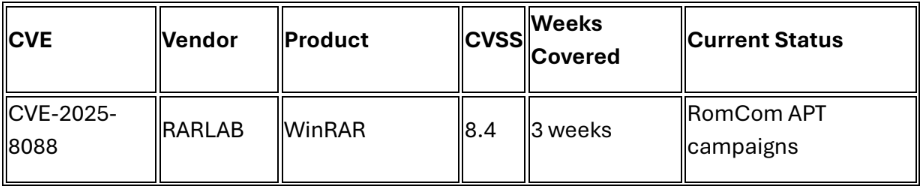
Russian-aligned espionage group maintaining sustained zero-day exploitation capabilities with confirmed operations across Europe and Canada targeting critical sectors. Current campaign exploits WinRAR CVE-2025-8088 through sophisticated spearphishing delivering Mythic Agent, SnipBot, and MeltingClaw backdoors.9 Group demonstrates advanced operational security with alternate data stream abuse and precision targeting of finance, manufacturing, defense, and logistics organizations. ESET research confirms third documented zero-day exploitation, indicating substantial resource allocation and strategic focus.
Akira Ransomware Affiliates
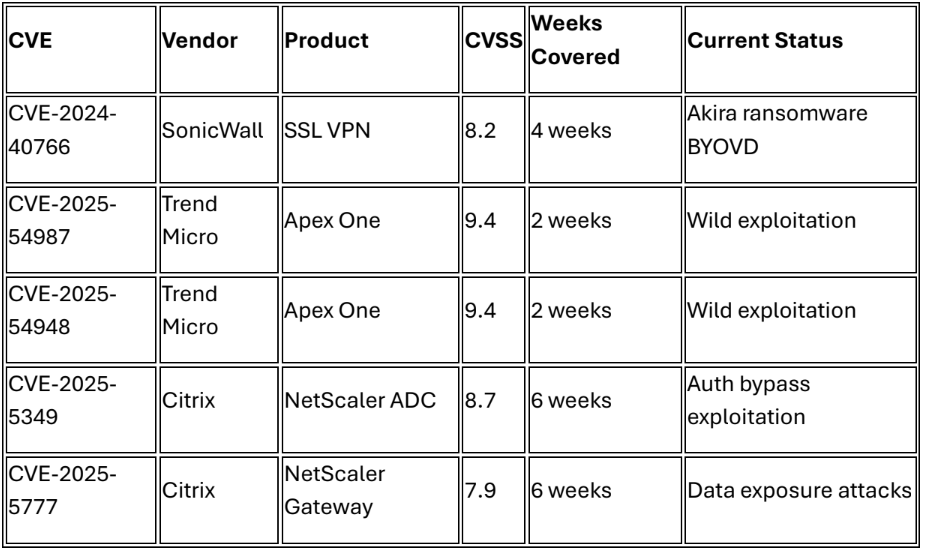
Criminal ransomware operation demonstrating rapid technical evolution with sophisticated BYOVD (Bring Your Own Vulnerable Driver) techniques targeting VPN infrastructure. Recent campaigns against SonicWall SSL VPN (CVE-2024-40766) employ legitimate signed drivers (rwdrv.sys, hlpdrv.sys) to terminate security processes before encryption deployment.10,11,12 GuidePoint Security confirmed campaign activity from late July through early August 2025 with focus on enterprise VPN infrastructure and managed service providers.
Charon Ransomware Group (Earth Baxia Techniques)
Sophisticated ransomware operator employing China-linked Earth Baxia APT techniques targeting Middle East public sector and aviation industries.13 Technical analysis reveals DLL side-loading via Edge.exe → msedge.dll (SWORDLDR) → process injection into svchost.exe with dormant anti-EDR capabilities (Dark-Kill project). Group utilizes Curve25519 + ChaCha20 hybrid cryptography with partial encryption strategy, network propagation via NetShareEnum, and mutex "OopsCharonHere" for operational coordination.
ShinyHunters and Scattered Spider Criminal Merger
Elite cybercriminal groups announced operational merger creating enhanced data extortion capabilities with 12% increase in financial sector targeting since July 2025.14
Combined operations leverage ShinyHunters' data theft expertise with Scattered Spider's social engineering and infrastructure access capabilities. Recent collaboration compromised Allianz Life Salesforce instance exposing 2.8 million customer records including names, addresses, phone numbers, dates of birth, Tax IDs, and professional licenses.15
Fortinet Infrastructure Targeting Coalition
Coordinated threat campaign involving 780+ unique IP addresses conducting synchronized brute-force attacks against Fortinet SSL VPN infrastructure with shift to FortiManager targeting.16 Geographic distribution spans US, Canada, Russia, Netherlands with primary targeting of US, Hong Kong, Brazil infrastructure. Peak activity observed August 3, 2025, indicating coordinated criminal or state-sponsored operations against enterprise VPN and management infrastructure.
TRENDS
Criminal Adoption of Nation-State Techniques
Intelligence confirms accelerated adoption of advanced persistent threat methodologies by criminal ransomware operators, with Charon ransomware incorporating Earth Baxia APT techniques and Crypto24 deploying custom EDR evasion platforms.17,18 Crypto24 group targets finance, manufacturing, entertainment, and technology sectors across US, Europe, and Asia using custom RealBlindingEDR variant designed to defeat 12+ security vendors. Analysis reveals criminal groups now employ DLL side-loading, BYOVD techniques, and sophisticated anti-forensics previously exclusive to nation-state actors.
Identity Infrastructure Vulnerability Cascade
Multiple simultaneous disclosures of critical vulnerabilities across enterprise identity management platforms created unprecedented attack surface expansion. Affected systems include Microsoft Kerberos (CVE-2025-53779), CyberArk Vault (CVE-2025-49827), HashiCorp Vault (CVE-2025-6000), and Cisco FMC RADIUS (CVE-2025-20265) with CVSS scores of 7.2-10.0.19,20,21 Pattern suggests coordinated vulnerability research targeting foundational authentication systems enabling complete organizational compromise without traditional credential theft.
Android Critical Infrastructure Mobile Targeting
Google addressed critical Android vulnerabilities affecting billions of devices, including CVE-2025-21479 and additional GPU micronode vulnerabilities enabling device compromise without user interaction.22 Assessment confirms targeting of Android 13, 14, 15, and 16 with Qualcomm Adreno GPUs powering critical enterprise and consumer
infrastructure. Vulnerability pattern indicates systematic research targeting mobile infrastructure supporting critical business operations and government systems.
VULNERABILITIES
Critical Patches Required This Week
Continuing Active Exploitation
RECOMMENDATIONS
Immediate Actions (0-24 Hours)
- Deploy Microsoft August 2025 patches immediately, prioritizing CVE-2025-53779 in all domain environments with focus on dMSA configurations
- Emergency patching of FortiSIEM CVE-2025-25256 or immediate restriction of TCP port 7900 access for all FortiSIEM deployments
- Audit and patch all N-able N-Central RMM deployments before August 20 CISA deadline; consider temporary service suspension if patching not feasible
- Conduct emergency assessment of CyberArk and HashiCorp Vault configurations with immediate access control review and privilege validation
- Implement emergency patching for Cisco FMC RADIUS systems (CVE-2025-20265) or disable RADIUS authentication pending patches
- The Hacker News. (2025, August 13). CISA alerts on N-able N-Central deserialization and injection flaw under active exploitation. The Hacker News. https://thehackernews.com/2025/08/cisa-adds-two-n-able-n-central-flaws-to.html
- Cybersecurity and Infrastructure Security Agency. (2025, August 13). CISA adds two known exploited vulnerabilities to catalog. CISA News. https://www.cisa.gov/news-events/alerts/2025/08/13/cisa-adds-two-known-exploited-vulnerabilities-catalog
- The Hacker News. (2025, August 13). CISA alerts on N-able N-Central deserialization and injection flaw under active exploitation. The Hacker News. https://thehackernews.com/2025/08/cisa-adds-two-n-able-n-central-flaws-to.html
- The Hacker News. (2025, August 15). Microsoft August 2025 Patch Tuesday fixes Kerberos zero-day among 111 total new flaws. The Hacker News. https://thehackernews.com/2025/08/microsoft-august-2025-patch-tuesday.html
- BleepingComputer. (2025, August 14). Canada's House of Commons investigating data breach after cyberattack. BleepingComputer. https://www.bleepingcomputer.com/news/security/canadas-house-of-commons-investigating-data-breach-after-cyberattack/
- The Hacker News. (2025, August 14). CyberArk and HashiCorp flaws enable remote vault takeover without credentials. The HackerNews. https://thehackernews.com/2025/08/cyberark-and-hashicorp-flaws-enable.html
- BleepingComputer. (2025, August 14). Pro-Russian hackers blamed for water dam sabotage in Norway. BleepingComputer. https://www.bleepingcomputer.com/news/security/pro-russian-hackers-blamed-for-water-dam-sabotage-in-norway/
- The Hacker News. (2025, August 14). Cisco warns of CVSS 10.0 FMC RADIUS flaw allowing remote code execution. The Hacker News. https://thehackernews.com/2025/08/cisco-warns-of-cvss-100-fmc-radius-flaw.html
- BleepingComputer. (2025, August 11). Details emerge on WinRAR zero-day attacks that infected PCs with malware. BleepingComputer. https://www.bleepingcomputer.com/news/security/details-emerge-on-winrar-zero-day-attacks-that-infected-pcs-with-malware/
- GuidePoint Security. (2025, August 8). GRITREP: Observed malicious driver use associated with Akira SonicWall campaign. GuidePoint Security. https://www.guidepointsecurity.com/blog/gritrep-akira-sonicwall/
- CyberPress. (2025, August 8). Akira ransomware uses Windows drivers to evade AV/EDR in SonicWall attacks. CyberPress. https://cyberpress.org/akira-ransomware-uses-windows-drivers/
- Arctic Wolf. (2025, August 8). Arctic Wolf observes July 2025 uptick in Akira ransomware activity targeting SonicWall SSL VPN. Arctic Wolf. https://arcticwolf.com/resources/blog-uk/arctic-wolf-observes-july-2025-uptick-in-akira-ransomware-activity-targeting-sonicwall-ssl-vpn-copy/
- Trend Micro. (2025, August 14). New ransomware Charon uses Earth Baxia APT techniques to target enterprises. Trend Micro Research. https://www.trendmicro.com/en_fi/research/25/h/new-ransomware-charon.html
- The Hacker News. (2025, August 14). Cybercrime groups ShinyHunters, Scattered Spider join forces in extortion attacks on businesses. The Hacker News. https://thehackernews.com/2025/08/cybercrime-groups-shinyhunters.html
- BleepingComputer. (2025, August 12). Hackers leak Allianz Life data stolen in Salesforce attacks. BleepingComputer. https://www.bleepingcomputer.com/news/security/hackers-leak-allianz-life-data-stolen-in-salesforce-attacks/
- The Hacker News. (2025, August 12). Fortinet SSL VPNs hit by global brute-force wave before attackers shift to FortiManager. The Hacker News. https://thehackernews.com/2025/08/fortinet-ssl-vpns-hit-by-global-brute.html
- Trend Micro. (2025, August 14). New ransomware Charon uses Earth Baxia APT techniques to target enterprises. Trend Micro Research. https://www.trendmicro.com/en_fi/research/25/h/new-ransomware-charon.html
- BleepingComputer. (2025, August 14). Crypto24 ransomware hits large orgs with custom EDR evasion tool. BleepingComputer. https://www.bleepingcomputer.com/news/security/crypto24-ransomware-hits-large-orgs-with-custom-edr-evasion-tool/
- The Hacker News. (2025, August 15). Microsoft August 2025 Patch Tuesday fixes Kerberos zero-day among 111 total new flaws. The Hacker News. https://thehackernews.com/2025/08/microsoft-august-2025-patch-tuesday.html
- The Hacker News. (2025, August 14). CyberArk and HashiCorp flaws enable remote vault takeover without credentials. The Hacker News. https://thehackernews.com/2025/08/cyberark-and-hashicorp-flaws-enable.html
- The Hacker News. (2025, August 14). Cisco warns of CVSS 10.0 FMC RADIUS flaw allowing remote code execution. The Hacker News. https://thehackernews.com/2025/08/cisco-warns-of-cvss-100-fmc-radius-flaw.html
- Malwarebytes. (2025, August 8). Critical Android vulnerabilities patched---update as soon as you can. Malwarebytes Labs. https://www.malwarebytes.com/blog/news/2025/08/android-critical-vulnerabilities-patched-update-as-soon-as-you-can


