Stay up to date the most pressing cyber threats, emerging trends and what they mean for enterprise security, critical infrastructure and global risk.
Classification: TLP: CLEAR
Executive Summary
Cyber threat actors continue to weaponize zero-day flaws within hours of discovery and launch sophisticated campaigns targeting critical infrastructure. Exploitation of Google Chrome zero-day CVE-2025-6554 by suspected nation-state actors demonstrates the speed at which threats now evolve, while Iranian cyber threat escalation targets U.S. defense contractors and Israeli entities amid geopolitical tensions. The emergence of AI-enhanced malware evasion techniques and Scattered Spider's expansion into aviation sectors also signal a dangerous evolution in threat actor capabilities and scope.
Two significant themes define this week's threat landscape: the ongoing collapse of vulnerability disclosure timelines and the intersection of geopolitical tensions with cyber operations. Organizations face immediate risks from thousands of unpatched Citrix NetScaler instances, critical Cisco ISE vulnerabilities enabling full system compromise, and massive data breaches affecting over 8.8 million individuals across healthcare, retail, and aviation sectors.
Analyst Comment: As we have been reporting for the past several weeks, the speed of exploitation for zero-day CVEs demonstrates that traditional patch management timelines are no longer viable defensive strategies. Organizations must implement zero-trust architectures and assume breach mentality.
Critical Incidents
1. Google Chrome Zero-Day CVE-2025-6554 Actively Exploited by Nation-State Actors
Google patched a type confusion vulnerability in Chrome's V8 JavaScript engine affecting versions prior to 138.0.7204.96, with active exploitation confirmed by Google's Threat Analysis Group on June 25.1 This marks the fourth Chrome zero-day patched in 2025, demonstrating sustained adversary focus on browser-based attack vectors.2 This particular vulnerability enables remote code execution via crafted HTML pages and affects all major platforms including Windows, macOS, and Linux.3 CISA added the vulnerability to the KEV catalog on July 2, requiring federal agencies to patch immediately under BOD 22-01.4
Analyst Comment: Browser zero-day exploitation means adversaries are shifting their tactics towards targeting the most ubiquitous attack surface across all organizations regardless of security posture.
2. Critical Cisco ISE Remote Code Execution Vulnerabilities Enable Full System Compromise
Two critical unauthenticated remote code execution vulnerabilities (CVE-2025-20281 and CVE-2025-20282) discovered in Cisco Identity Services Engine allow remote attackers to gain root access through insufficient input validation in exposed and internal APIs.5 The vulnerabilities affect ISE and ISE-PIC versions 3.3 and 3.4, enabling arbitrary OS command execution without authentication.6 These flaws represent immediate threats to enterprise network access control infrastructure.
Analyst Comment: Threat actors utilize Identity Services Engine compromises to gain administrative control over network access policies, effectively turning security infrastructure against defenders.
3. Iranian Cyber Threat Escalation Targets U.S. Defense and Critical Infrastructure
A new Joint CISA, FBI, and NSA statement warns of the potential for Iranian-affiliated cyber actors targeting U.S. critical infrastructure amid ongoing Middle East tensions. One example of that threat Iran-affiliated cyber actors pose is the spear-phishing campaigns that IRGC affiliated threat group Educated Manticore reportedly conducted against Israeli journalists and cybersecurity academics using multistage React-based credential harvesting across 130+ domains.7
Analyst Comment: Iranian cyber operations demonstrate coordinated state-level campaigns aligning with geopolitical objectives, requiring heightened defensive postures across targeted sectors. Defense Industrial Base companies with Israeli research ties face a particularly elevated risk as Iran deploys sophisticated social engineering and exploits unpatched vulnerabilities.
Active Threat Actors
Scattered Spider Expands Aviation Sector Targeting
The financially-motivated cybercrime group Scattered Spider expanded operations from retail and insurance sectors to target critical transportation infrastructure. Hawaiian Airlines disclosed a cybersecurity incident on June 27, with FBI confirmation of Scattered Spider involvement.8 This reported attack was just two weeks after WestJet’s 13 June confirmation of being targeted, signifying systematic aviation sector reconnaissance.9 The group, reportedly comprised primarily of teens and young adults from the UK and US, employs enhanced social engineering and phishing-resistant MFA bypass techniques, representing evolution from opportunistic to targeted infrastructure attacks.
Iranian APT Educated Manticore Intensifies Espionage Operations
Islamic Revolutionary Guard Corps (IRGC)-affiliated threat actors (Educated Manticore) conducted sophisticated spear-phishing campaigns targeting Israeli journalists and cybersecurity academics via email and WhatsApp.10 The group deployed multistage React based credential harvesting kits across over 130 domains supporting vast espionage infrastructure.11 Campaign objectives include stealing credentials and 2FA codes for Google, Yahoo, and Outlook accounts, enabling persistent access to victim communications and networks.
North Korean APT BlueNoroff Targets Cryptocurrency Organizations with macOS Malware
BlueNoroff deployed Nim-compiled macOS malware targeting web3 and cryptocurrency organizations through fake Zoom SDK updates delivered via Calendly meeting invitations.12 The NimDoor malware features encrypted configuration handling and signal-based persistence, demonstrating advanced technical capabilities.13 Attack chains establish persistent access through AppleScripts and bash scripts for data exfiltration, specifically targeting employees at cryptocurrency and blockchain companies.
Trends
Zero-Day Vulnerability Weaponization Timeline Collapse
Analysis confirms attackers increasingly exploit vulnerabilities within hours of disclosure, representing a fundamental shift in threat actor capabilities. Multiple CVEs showed exploitation signs before inclusion in CISA's KEV catalog, with threat actors demonstrating rapid weaponization capabilities. The Chrome zero-day detection and mitigation timeline compressed to 24 hours from initial discovery to patch deployment,14 indicating sophisticated monitoring of security research and development cycles.
Analyst Comment: Traditional patch management cycles cannot match current threat actor weaponization speed, requiring organizations to implement zero-trust architectures and continuous monitoring.
AI-Enhanced Malware Evasion Techniques Emerge
Threat actors developed unique AI prompt injection techniques to manipulate security analysis models, instructing AI systems to ignore previous instructions and avoid malware analysis.15 While currently ineffective against large language models like OpenAI's GPT-4, this represents evolving tactics at the intersection of malware and AI technologies.16 Check Point Research identified malware campaigns specifically designed to evade AI-powered security tools through embedded prompt manipulation code.
Analyst Comment: AI-enhanced evasion represents the beginning of adversarial machine learning in operational malware, requiring security teams to understand AI system limitations and manipulation vectors.
Critical Infrastructure Ransomware Acceleration
Industrial entities worldwide experienced 708 ransomware incidents in Q1 2025, up from 600 in Q4 2024, with manufacturing sectors accounting for 68% of attacks.17 Two new OT cyber threat groups emerged: GRAPHITE (Russia-linked) and BAUXITE (Iran-linked), with BAUXITE deploying IOCONTROL malware targeting IoT and OT devices in U.S. and Israeli infrastructure.18
At least nine threat groups reportedly maintain active OT operations, with four possessing ICS Cyber Kill Chain Stage 2 capabilities.19
Analyst Comment: Industrial control system targeting represents strategic adversary investment in critical infrastructure disruption capabilities, aligning with geopolitical objectives and hybrid warfare strategies.
Vulnerabilities
Critical Patches Required This Week
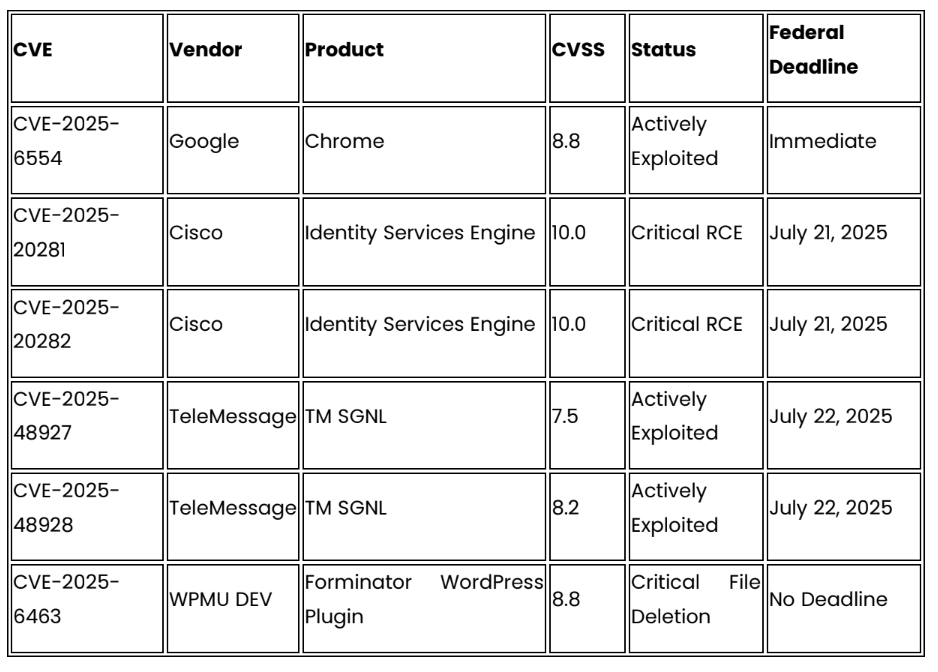
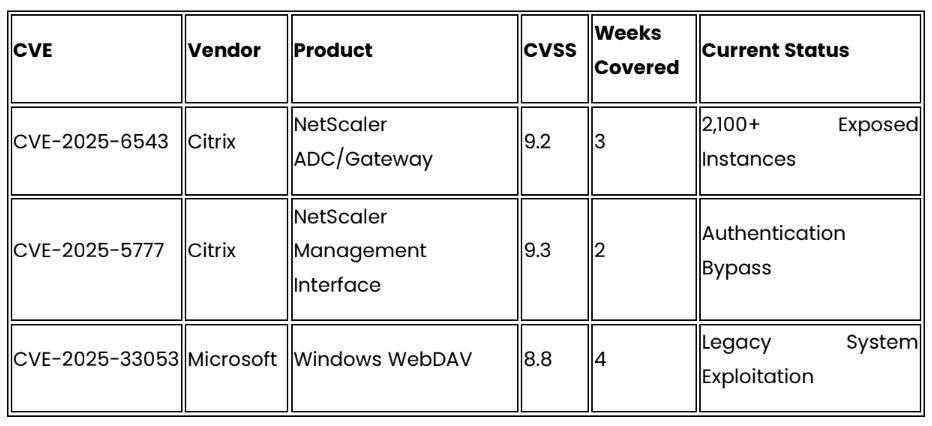
Continuing Active Exploitation
Recommendations
Immediate Actions (0-24 Hours)
• Update all Chrome installations immediately to version 138.0.7204.96 or later to address actively exploited zero-day CVE-2025-6554
• Implement emergency Cisco ISE patching protocols for CVE-2025-20281 and CVE 2025-20282 due to unauthenticated RCE capabilities
• Activate enhanced monitoring for Iranian threat indicators including suspicious authentication attempts, WebDAV exploitation, and social engineering targeting defense contractors
• Verify Citrix NetScaler patch status and implement workarounds for the 2,100+ globally exposed vulnerable instances
Short-term Actions (1-7 Days)
• Deploy phishing-resistant multi-factor authentication across aviation and transportation sector organizations following Scattered Spider targeting patterns
• Implement AI-powered security tool validation procedures to identify potential prompt injection manipulation in security analysis workflows
• Strengthen industrial control system network segmentation and monitoring to counter emerging OT-focused threat groups GRAPHITE and BAUXITE
• Enhance vulnerability management processes to match accelerated threat actor weaponization timelines through automated patching and zero-trust implementation
- Google. (2025, June 30). Stable channel update for desktop. Chrome Releases. https://chromereleases.googleblog.com/2025/06/stable-channel-update-for-desktop_30.html
- Google. (2025, June 30). Stable channel update for desktop. Chrome Releases. https://chromereleases.googleblog.com/2025/06/stable-channel-update-for-desktop_30.html
- Google. (2025, June 30). Stable channel update for desktop. Chrome Releases. https://chromereleases.googleblog.com/2025/06/stable-channel-update-for-desktop_30.html
- CISA. (2025, July 2). CISA adds one known exploited vulnerability to catalog. Cybersecurity and Infrastructure Security Agency. https://www.cisa.gov/news-events/alerts/2025/07/02/cisa-adds-one-known-exploited-vulnerability-catalog
- Check Point Research. (2025, June 29). 29th June – Threat Intelligence Report. Check Point Research. https://research.checkpoint.com/2025/29th-june-threat-intelligence-report/
- Center for Internet Security. (2025, June 25). Multiple vulnerabilities in Cisco ISE and ISE-PIC could allow for remote code execution. MS-ISAC Advisory 2025-059. https://www.cisecurity.org/advisory/multiple-vulnerabilities-in-cisco-ise-and-ise-pic-could-allow-for-remote-code-execution_2025-059
- Check Point Research. (2025, June 29). 29th June – Threat Intelligence Report. Check Point Research. https://research.checkpoint.com/2025/29th-june-threat-intelligence-report/
- SecurityWeek. (2025, June 30). Hawaiian Airlines hacked as aviation sector warned of Scattered Spider attacks. SecurityWeek. https://www.securityweek.com/hawaiian-airlines-hacked-as-aviation-sector-warned-of-scattered-spider-attacks/
- SecurityWeek. (2025, June 30). Hawaiian Airlines hacked as aviation sector warned of Scattered Spider attacks. SecurityWeek. https://www.securityweek.com/hawaiian-airlines-hacked-as-aviation-sector-warned-of-scattered-spider-attacks/
- Check Point Research. (2025, June 29). 29th June – Threat Intelligence Report. Check Point Research. https://research.checkpoint.com/2025/29th-june-threat-intelligence-report/
- Check Point Research. (2025, June 29). 29th June – Threat Intelligence Report. Check Point Research. https://research.checkpoint.com/2025/29th-june-threat-intelligence-report/
- SecurityWeek. (2025, July 3). North Korean hackers use fake Zoom updates to install macOS malware. SecurityWeek. https://www.securityweek.com/north-korean-hackers-use-fake-zoom-updates-to-install-macos-malware/
- SecurityWeek. (2025, July 3). North Korean hackers use fake Zoom updates to install macOS malware. SecurityWeek. https://www.securityweek.com/north-korean-hackers-use-fake-zoom-updates-to-install-macos-malware/
- Google. (2025, June 30). Stable channel update for desktop. Chrome Releases. https://chromereleases.googleblog.com/2025/06/stable-channel-update-for-desktop_30.html
- Check Point Research. (2025, June 29). 29th June – Threat Intelligence Report. Check Point Research. https://research.checkpoint.com/2025/29th-june-threat-intelligence-report/
- Check Point Research. (2025, June 29). 29th June – Threat Intelligence Report. Check Point Research. https://research.checkpoint.com/2025/29th-june-threat-intelligence-report/
- Dragos. (2025, May 22). Dragos industrial ransomware analysis: Q1 2025. Dragos Blog. https://www.dragos.com/blog/dragos-industrial-ransomware-analysis-q1-2025/
- Dragos. (2025, May 22). Dragos industrial ransomware analysis: Q1 2025. Dragos Blog. https://www.dragos.com/blog/dragos-industrial-ransomware-analysis-q1-2025/
- Dragos. (2025, May 22). Dragos industrial ransomware analysis: Q1 2025. Dragos Blog. https://www.dragos.com/blog/dragos-industrial-ransomware-analysis-q1-2025/


