Securing access to business apps against today’s reliance on third-party contractors, suppliers and outsourcers is an IT nightmare. Traditional perimeter security tools (e.g., VDI, VPN) are blunt instruments, granting broad access for unmanaged devices to access critical apps and data. The alternative of shipping corporate managed laptops is expensive, time-consuming and prone to logistical hurdles.
Zero Trust Application Access from Silo allows users to work on their own devices without installing software. It leverages user, device and network context to constrain access to only specified apps and control how data is used.

You can uncross your fingers that third-parties will use your security solution.
Shield apps and critical data from unmanaged devices' “last-mile” vulnerabilities.
Decide when isolation and DLP controls are needed in specific access scenarios
Gain visibility into how your apps are being accessed and actions taken with data.
Built for the cloud, our solution deploys and scales easily to for same-day enablement.
Insert isolation where and when you need it without disrupting user workflows.

1. IT sets policy for third-party access to only work through Silo
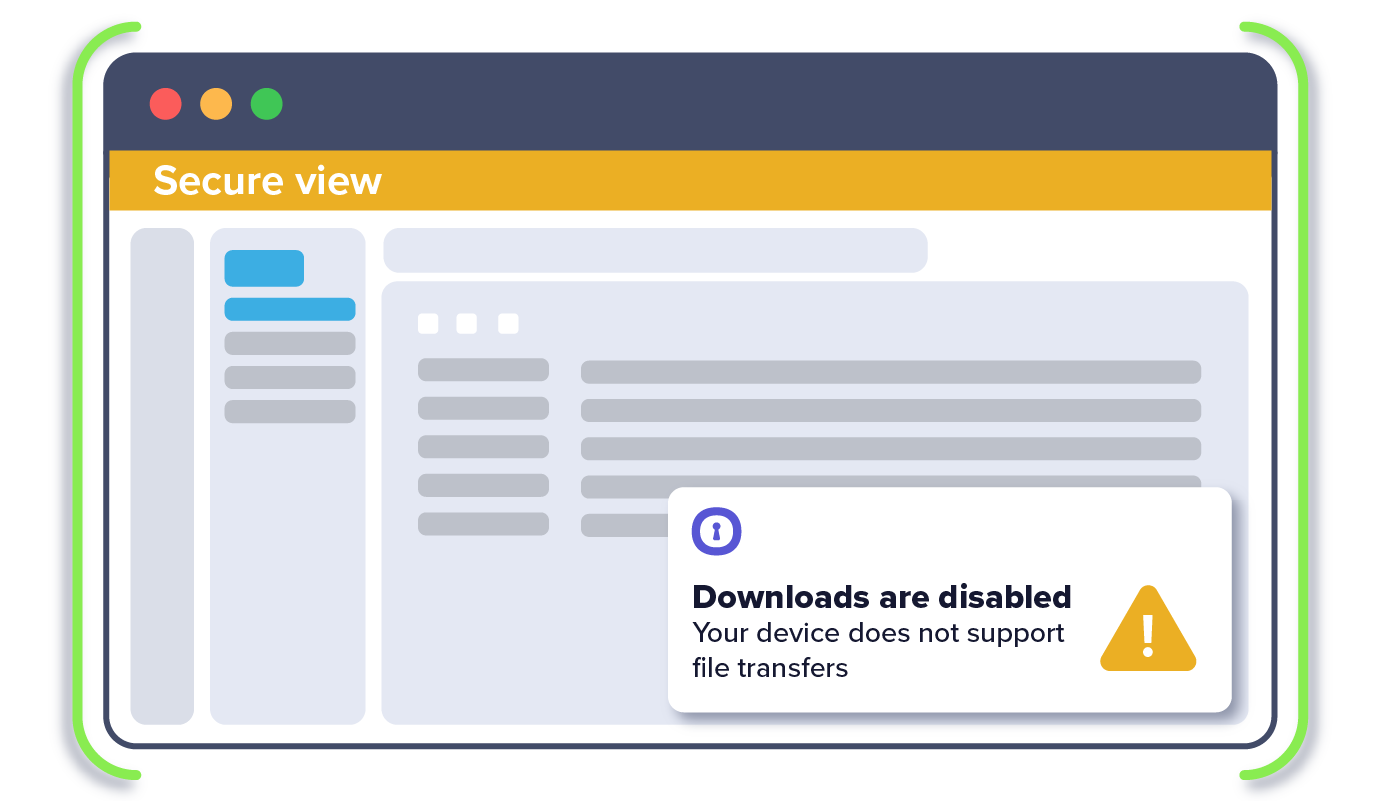
2. IT sets policy for data transfer permissions
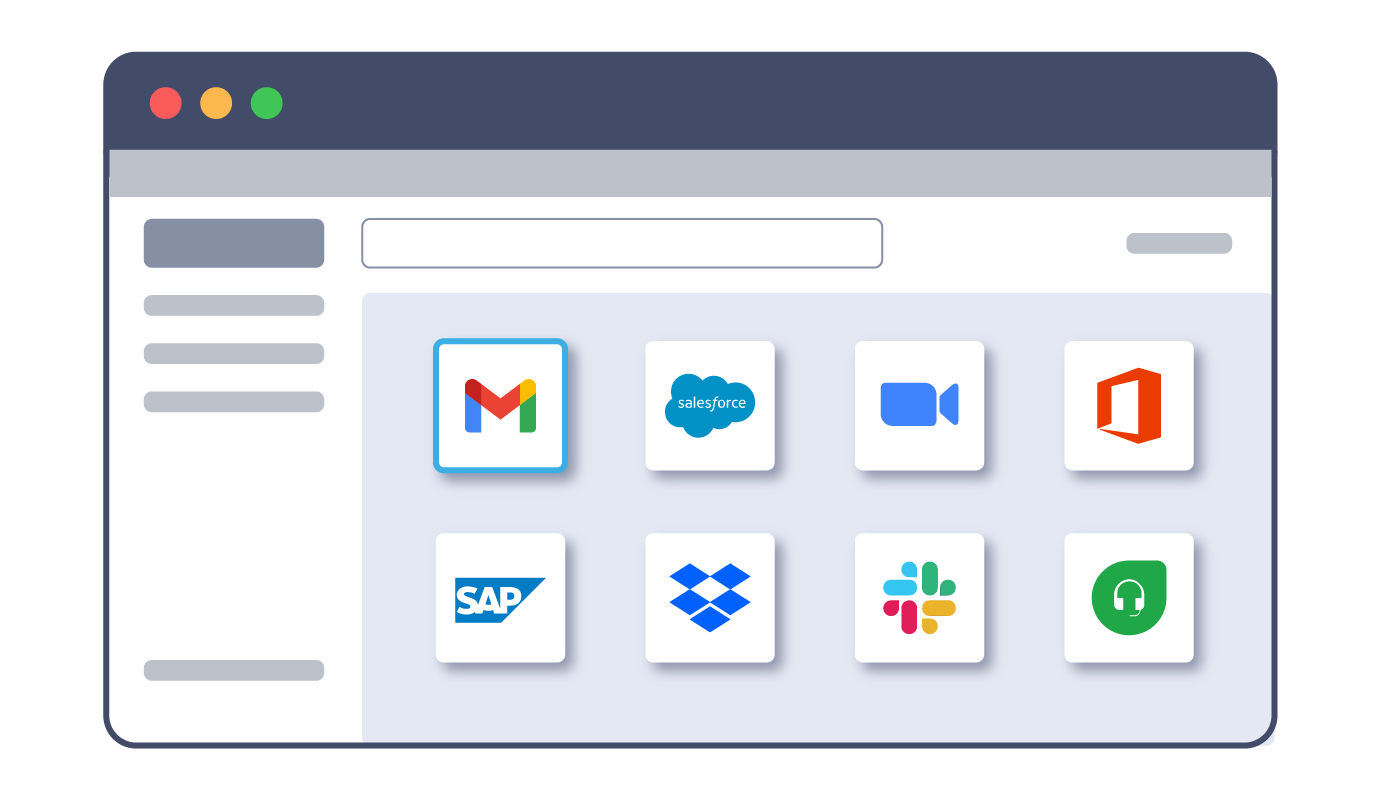
3. Third party opens application on existing browser (e.g., Chrome) on unmanaged device
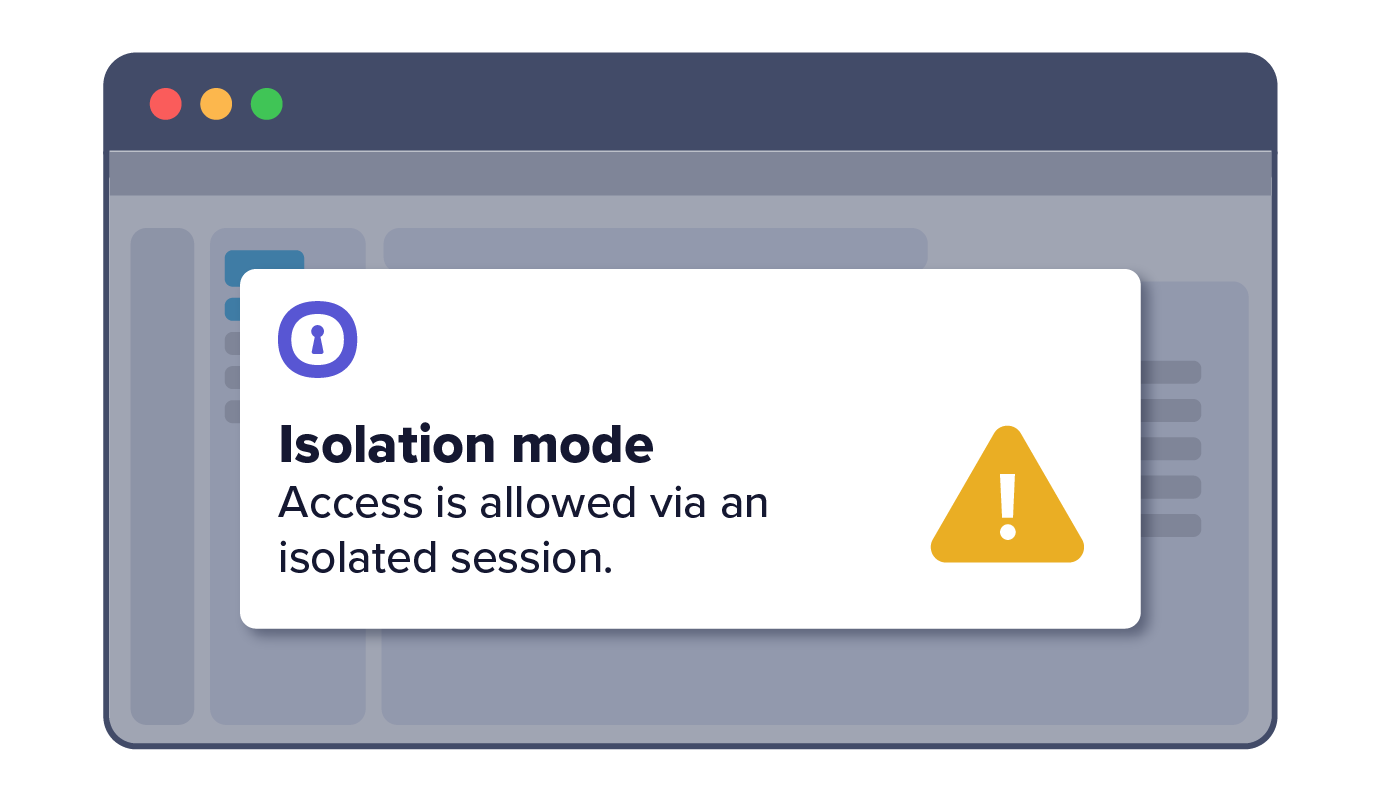
4. Third-party receives notice that they must proceed in isolated tab
5. Third party is granted access, but cannot perform certain data actions within the app