Cloud-based apps help boost productivity, but they also complicate IT’s task to secure resources and protect data. Typically, an organization would need to deploy various endpoint and network tools, routing employee sessions back to HQ, installing client software on personal assets and pulling data from cloud apps via API. Zero Trust Application Access presents an alternative, giving IT leverage that is as centralized and efficient as the cloud apps themselves.



As more workflows move to the web, IT's job of securing data gets harder. Applications and devices live outside of their control, but that doesn't mean they're not still responsible. Rather than deploying network, gateway or endpoint solutions, Zero Trust Application Access is a secure, high-trust environment that enables access without sacrificing security or compliance.
As a cloud-native platform, Silo meets the needs of your business at any point in time, from one user to all users, from simple policies to the complex. No upfront investment is required to adopt Silo, and its flexible capacity allows users to be easily added or deleted. All administrative actions — from adjusting data policies of revocation to access — are conducted centrally and in real time.
Today’s environment has more diverse points of risk than organizations can effectively manage. Trends like mobility and cloud applications put organizations under even greater pressure. Zero Trust Application Access provides the web environment a single point of control. Networks become utility services, devices become simple displays and all the intelligence and enforcement shifts to the central Silo Web Isolation Platform.
Rather than chasing endpoints or pulling data via APIs, use the browser as the central point of management and control. Zero Trust Application Access embeds all access policies, device authorizations and data permissions into the user’s profile. No matter what device or network they come from, Zero Trust Application Access gives centralized command and control over how users access your data and what they do with it.

Zero Trust Application Access can be locked down to a single app or a collection of business apps that are specific to the user’s role. By creating a workspace that is segregated from the device and the rest of the web, you minimize external vulnerabilities. IT has one choke point to configure and one master view to ensure proper handling of corporate assets.
Zero Trust Application Access lets you define specific data policies across managed and unmanaged computers. For instance, authorized or trusted devices may be allowed to download or copy/paste, while a personal device can be limited to read-only access or blocked from accessing the data altogether.

All management actions are performed in the cloud, and admins can seamlessly grant or revoke access to applications and data based on device policies. Changes happen in real time, even in live sessions. Regardless of the user, location or device, Silo’s central policy framework defines control, whether you’re granting access or taking it away.

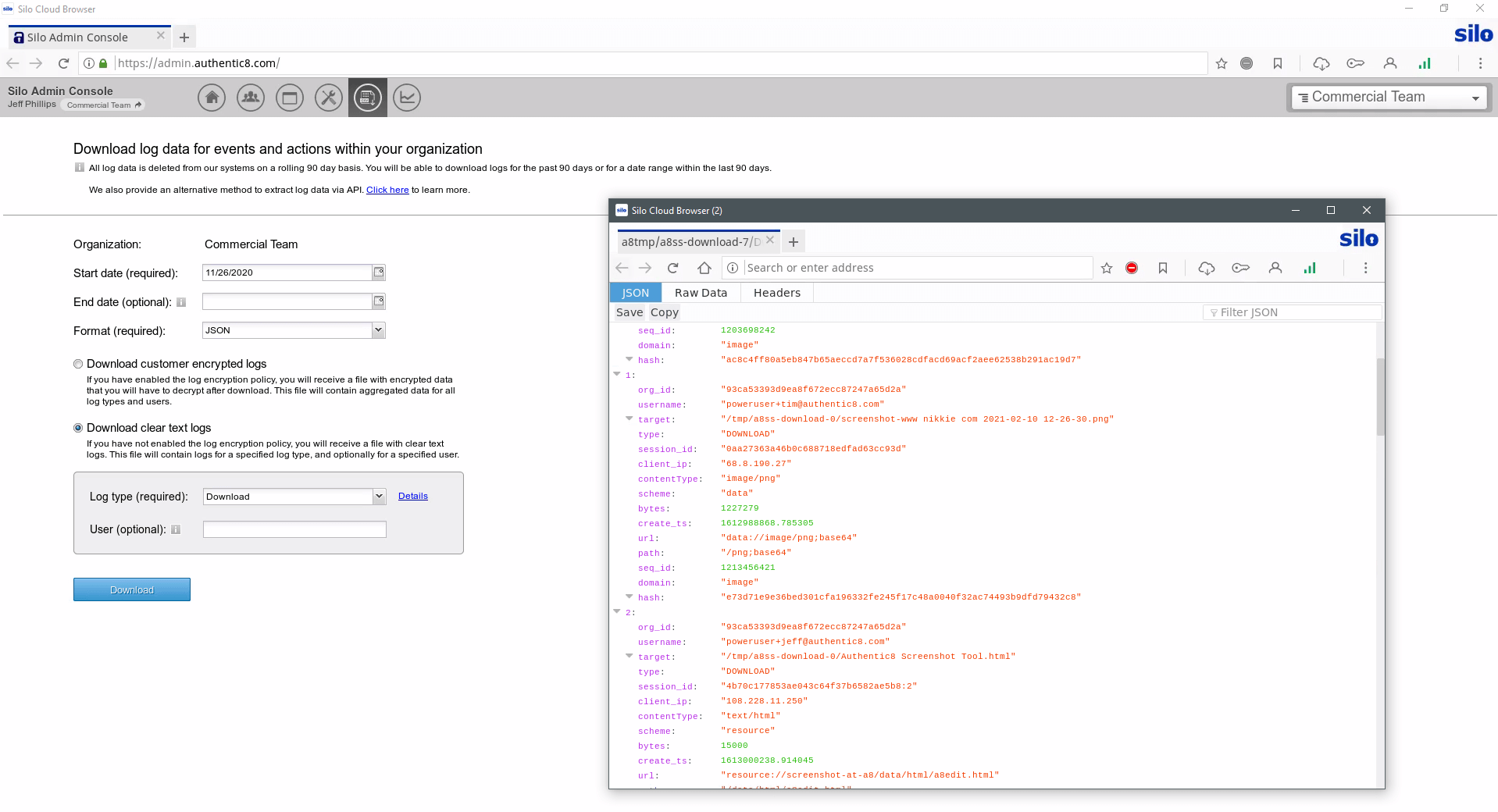
Whether conducting comprehensive monitoring via log analysis, integrating with an orchestration platform or spot-checking for violations, Zero Trust Application Access logs and encrypts all user and admin activity for post-factum analysis. This keeps your dynamic and mobile workforce in compliance with organizational policies.