The job of the analyst is getting harder with no slowdown in sight. Keeping up KYC, BSA, AML or other investigatory caseload is a growing productivity problem. And as adversaries move across web properties and networks, investigators are often unequipped to follow leads to all corners of the web.
That’s why leading financial institutions rely on Silo to support secure, anonymous and efficient investigations into financial fraud, money laundering and other activities that either jeopardize the business or are subject to regulations.

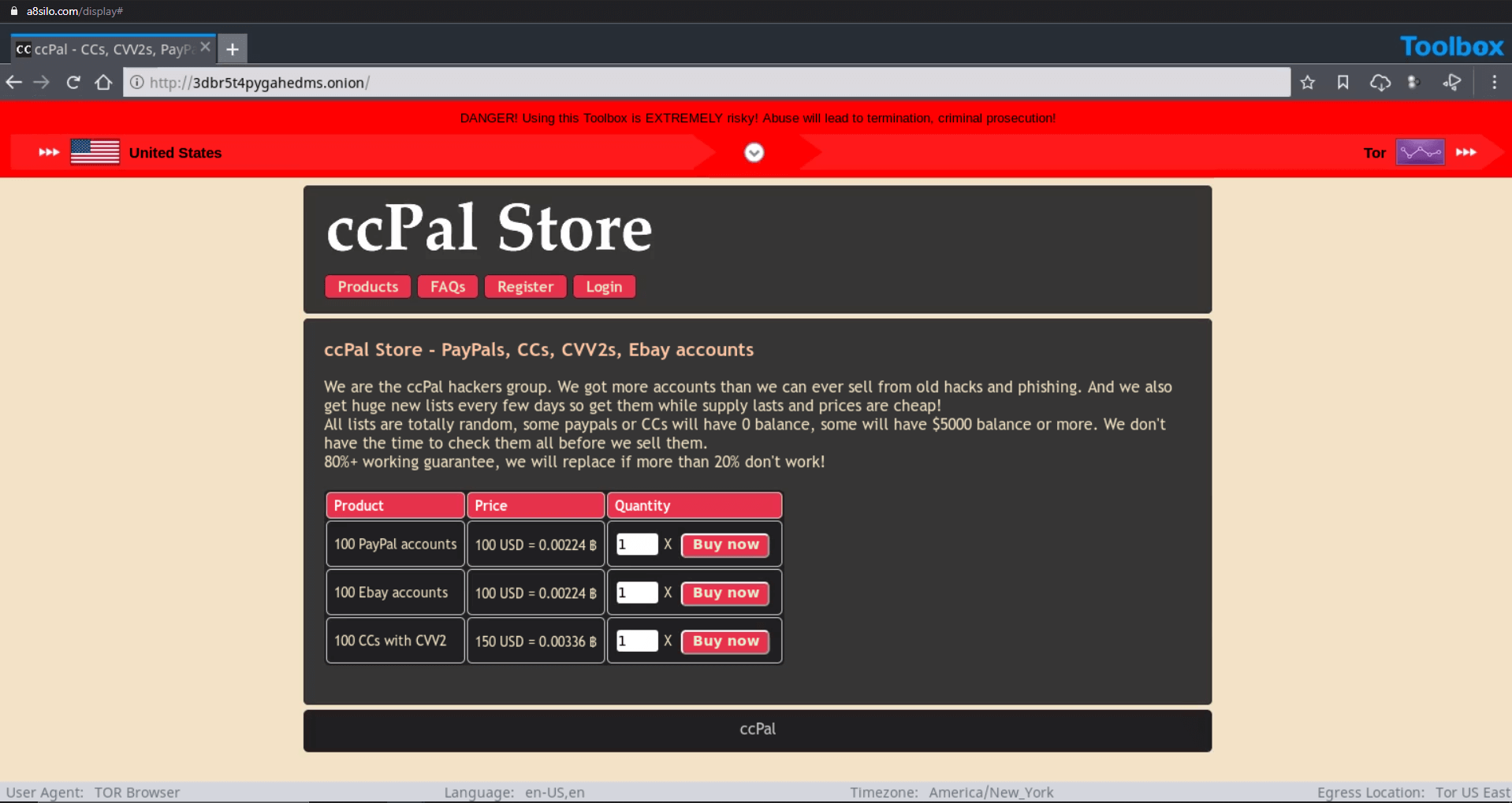
As a cloud-based app, Silo for Research builds isolation environments on demand. Whether for one user or thousands, each session is created fresh and populated with user-specific policies and configurations. Upon session closing, the virtual container is destroyed, only saving log data or collected materials. On the next launch, users get a completely fresh environment.
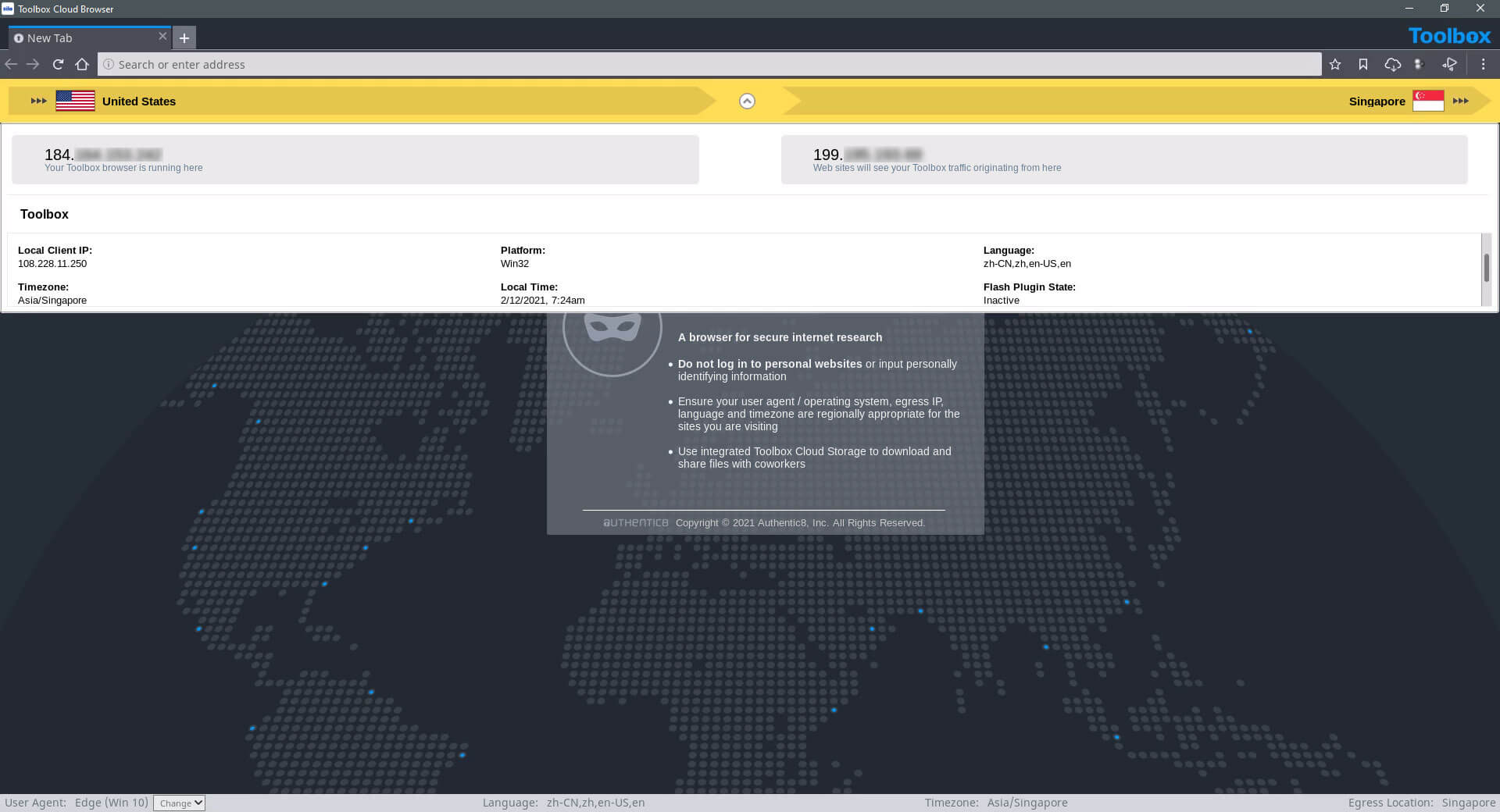
Because Silo executes remotely, no web-native code ever reaches the endpoint, and no endpoint code can affect web data. Silo keeps all scripts, cookies, trackers, executables, binary content and everything in between in the secure, remote container. Thanks to our proprietary access protocol, users get full fidelity access to the web without ever actually touching it.
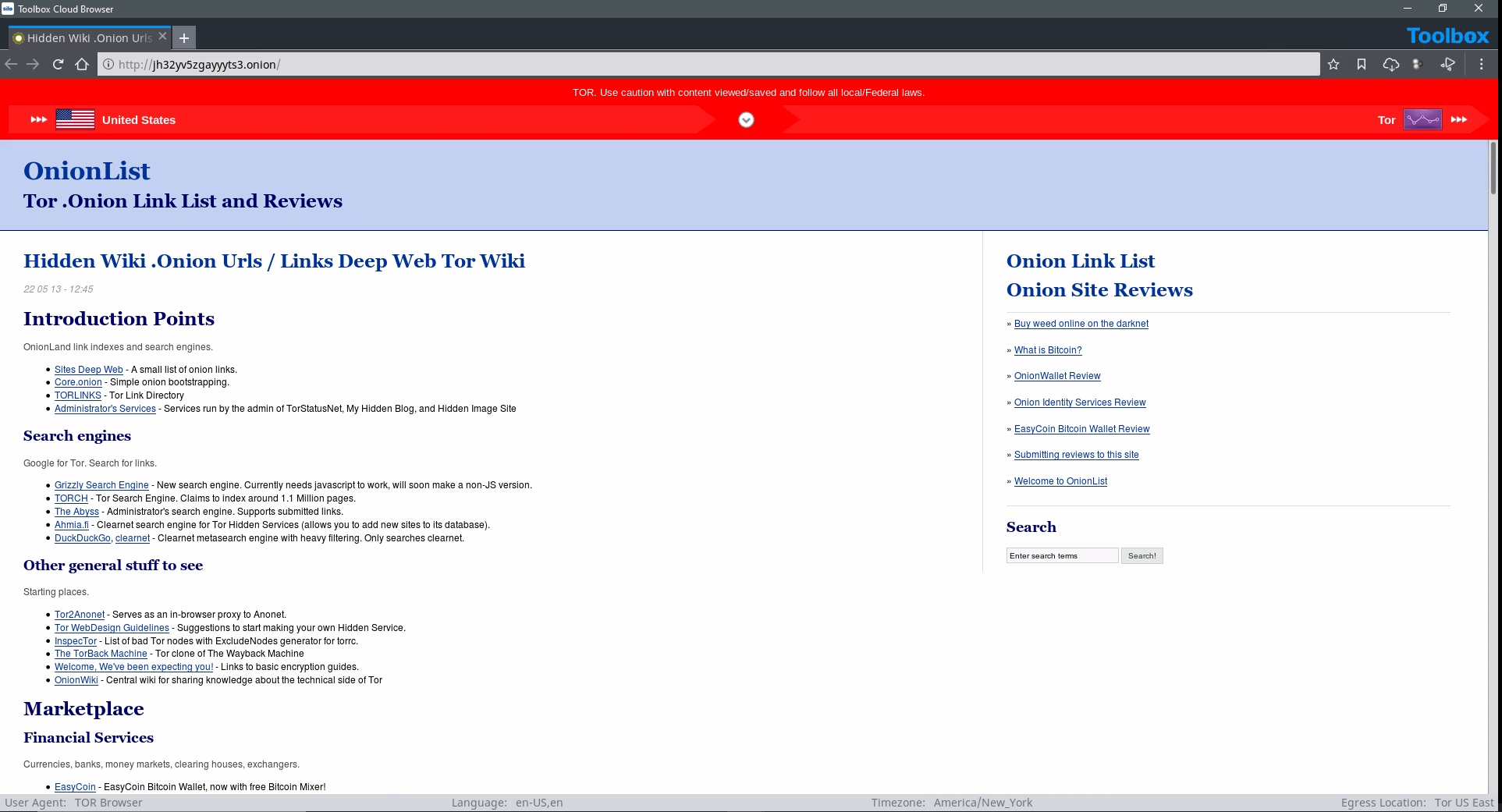
Analysts need to hide in plain sight. Silo for Research can execute in dozens of geographies around the world, showing a local IP that never refers back to your organization. And it can be configured to fit the local requirements, including OS, browser, time zone, language, keyboard settings and more. And you can spin multiple parallel Silo for Research instances, each reflecting a different configuration.
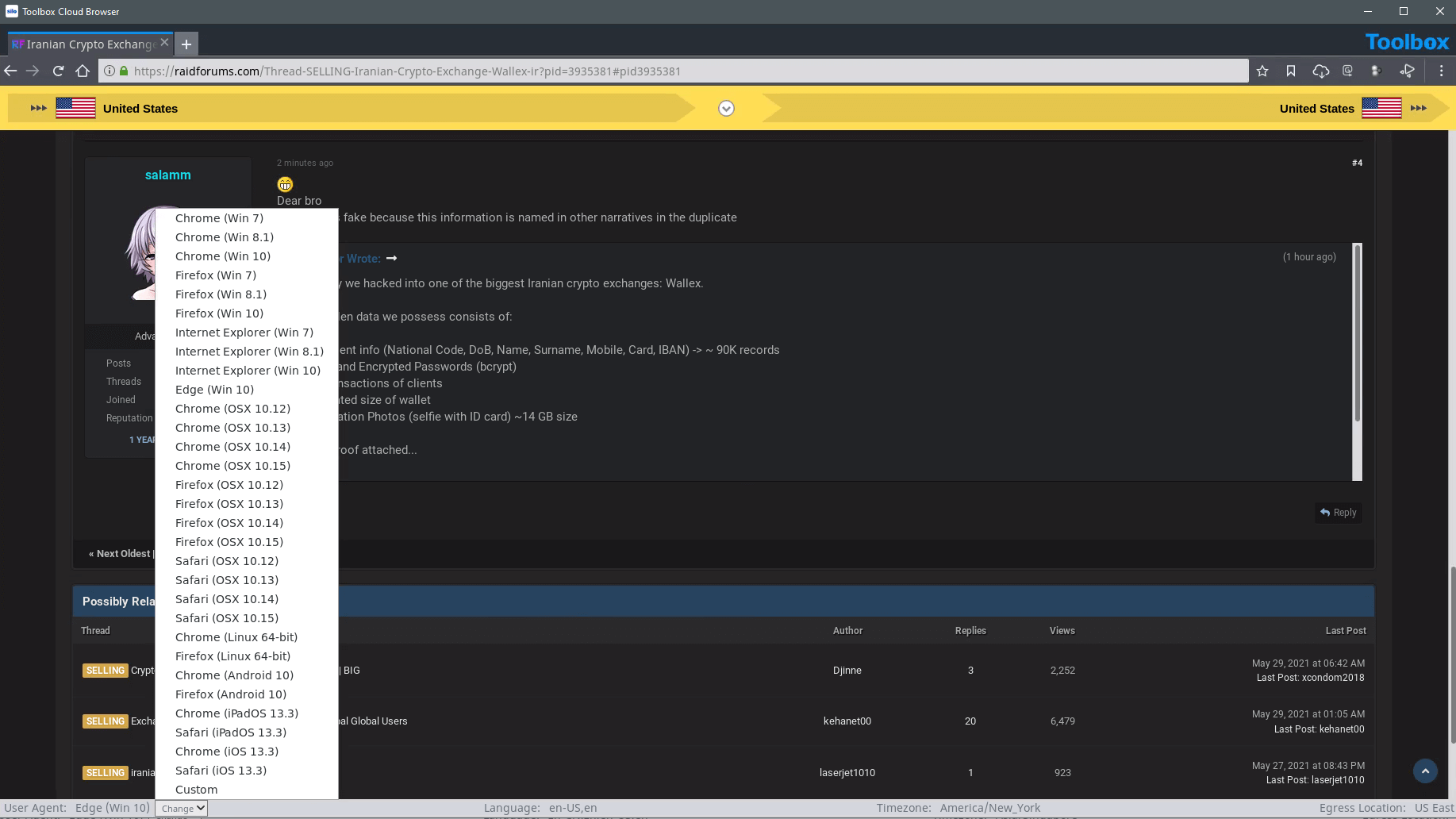
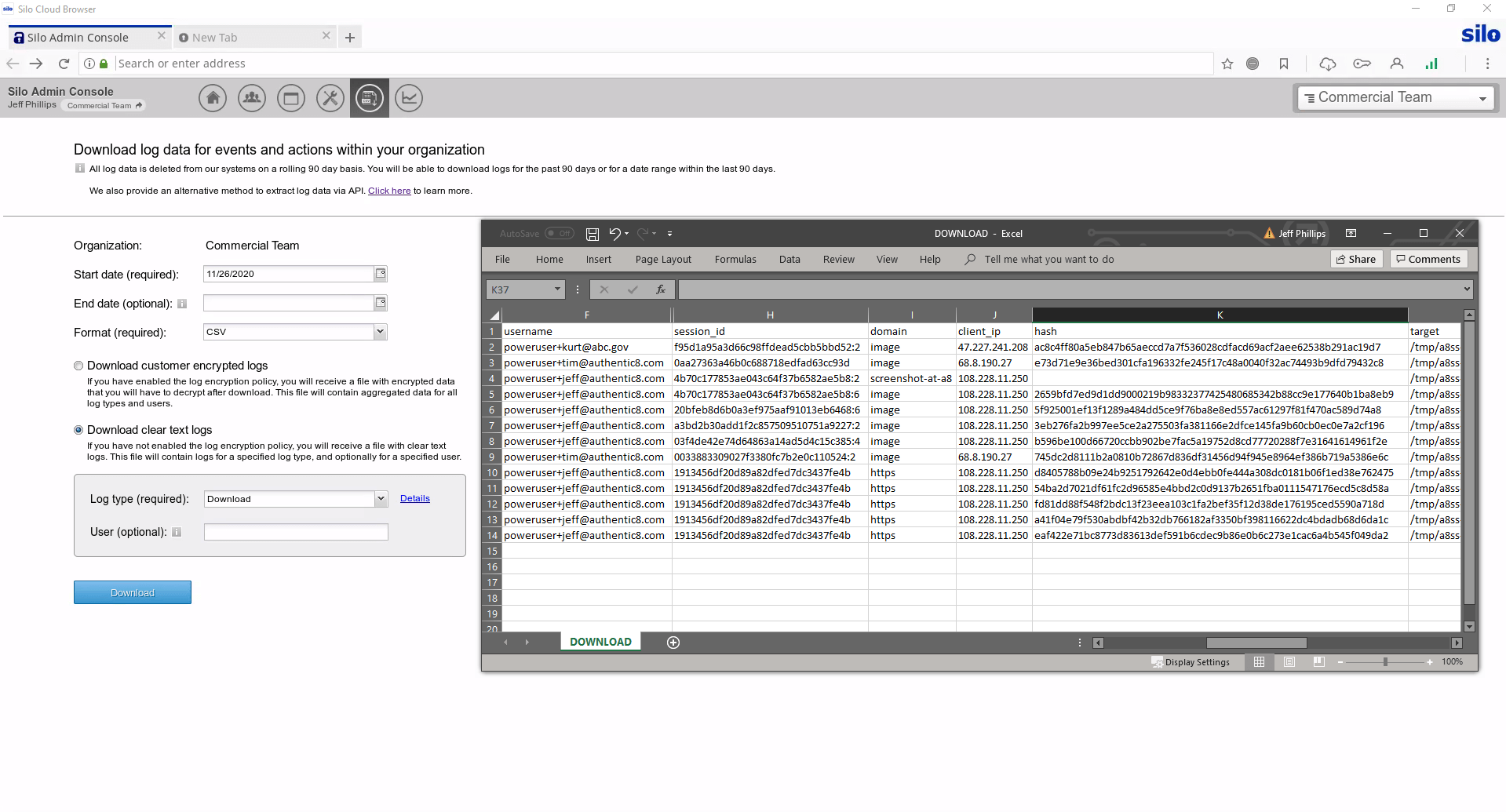
Collected data needs to be logged, attributed to an analyst and checked for validity. Chain of custody protections are critical to proper collection. When using Silo for Research collection tools — whether manual or automated — all aspects of the process are logged and available for post-facto review.
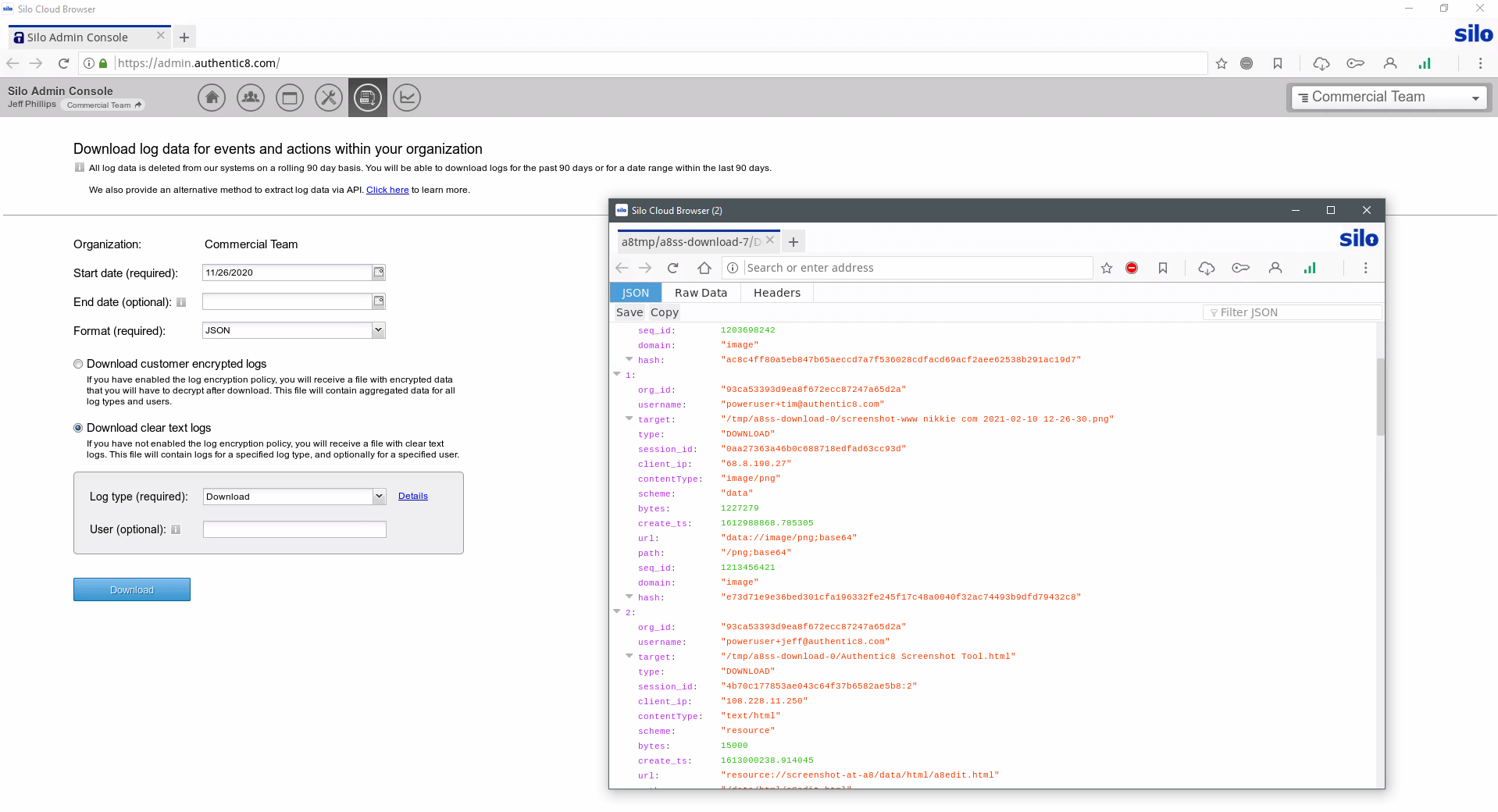
Some investigations lead to more formal review, whether by internal teams, regulators or or the courts. Presenting evidentiary logs and case materials starts with centralized processes and clear custodial records. Silo for Research provides a single framework for tracking collections and monitoring workflows, with all activity logged and encrypted with customer-managed keys.




Keeping up AML, KYC, BSA or other investigatory caseload is a growing productivity problem. And as adversaries move across web properties and networks, investigators are often unequipped to follow leads to all corners of the web. Silo for Research supports secure, anonymous and efficient investigations into financial fraud, money laundering and other activities that either jeopardize the business or are subject to regulations.
Yes, Silo for Research is a FedRAMP-authorized service. It has been assessed and approved as a cloud service offering (CSO) that meets the stringent security requirements to process, store and transmit federal government data.
Yes, dark web access is seamlessly integrated within Silo for Research and its suite of analyst tools. You do not need a separate, standalone dark web browser. This integration provides investigators with full isolation from dark web cyberthreats (e.g., malware-laden sites, forums, marketplaces) and anonymity from counter-surveillance efforts utilized by malicious actors.
Yes, Silo for Research integrates with Authentic8 Secure Storage, an encrypted, audited and cloud-based storage repository for users and groups. Investigators may be required to capture and collect content as part of their process. And to maintain efficacy of potential evidence, a proper chain of control and evidentiary requirements must be met.
Collected data needs to be logged, attributed to an analyst and checked for validity. Chain of custody protections are critical to proper collection. When using Silo for Research collection tools — whether manual or automated — all aspects of the process are logged and available for post-facto review.