Using the local computer and network to collect open-source content puts OSINT teams and investigators at risk. In order to minimize that risk, organizations use a variety of tools such as client-side virtualization, segregated internet access, VPNs, stand alone storage and advanced malware-scanning solutions. These are costly to deploy, and the complicated IT management requirements create security and attribution gaps.
“Ninety percent of intelligence comes from open sources.” - Lieutenant General Sam Wilson, USA (Ret.), former Director, Defense Intelligence Agency

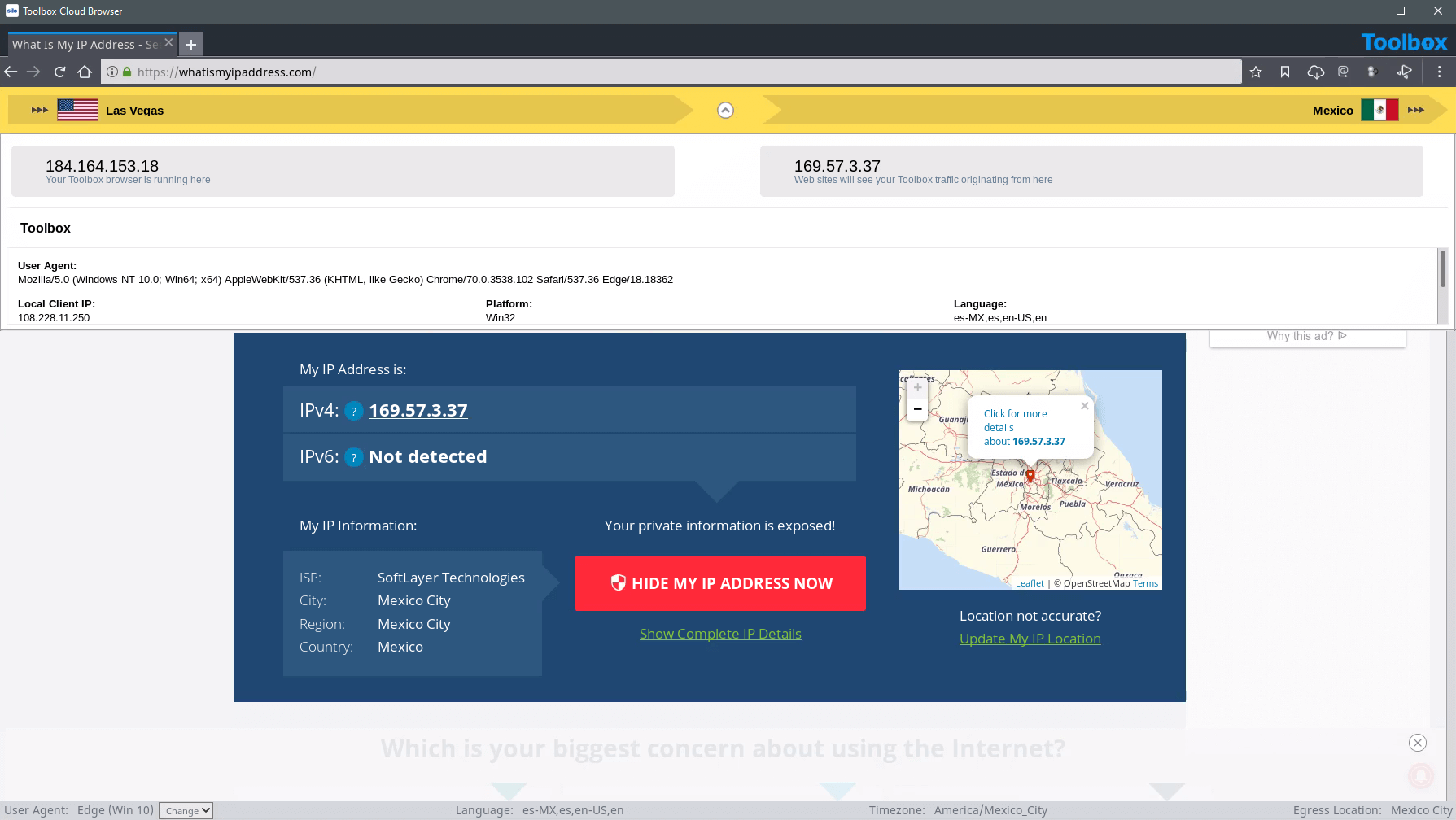
Complete isolation from all web content through a cloud-based virtual browser that connects to an anonymous network across geographies. This network allows analysts to appear as in-region visitors; customize language, time zone, OS, browser type and more to help analysts blend in with the crowd and avoid arousing suspicion.
Separate virtual windows support simultaneous collection actions across resources and networks, and multi-search workflows can be automated. Automate any collection in line with tradecraft, and share research materials with other investigators with cloud-based storage.
Tipping off the target of an investigation can ruin months of painstaking work. Silo manages attribution through customization of browser and platform parameters, including language, time zone, keyboard settings and user agent string. Analysts blend into the local environment through a network of globally distributed egress locations.
Analysts need to access web resources that fall outside of standard corporate policies — including on the dark web. Silo for Research logs all analyst activity in encrypted audit logs. Compliance teams can review analyst activity and remediate issues. Customer-managed encryption keys maintain a proper chain of control for non-repudiation of activity logs.