The security industry has been talking about the need for new security architectures for years. Are organizations finally listening?
The security industry has been writing about the death of the traditional perimeter and the need for organizations to consider new security architectures for a number of years. The story has become a familiar one:
Users and devices are increasingly untethered from the corporate network, and apps and data are living in cloud services. Traditional network-based remote access tools like VPNs have become outmoded in this new cloud-first world — especially when users are not only employees but consultants, contractors, franchisees and other more loosely affiliated workers using devices that IT cannot touch or manage.
There is no doubt that we are going through a fundamental transformation in IT architecture. While the COVID-19 crisis has rapidly forced businesses into a telework mode, this shift has been years in the making. According to Global Workplace Analytics, regular work-at-home has grown 173% since 2005, and will continue to increase as business becomes more global, flexible and decentralized.
A new crop of direct-to-cloud secure access solutions are rising to meet this transformation. Termed Zero Trust or SASE (Secure Access Service Edge) architectures, they rethink the traditional ideas of internal versus external users and shift the focus to protecting resources rather than network segments with a “never trust, always verify” access model.
The ZT/SASE model is based on certain core principles: identifying and authenticating the user and device, looking up application authorization policies, granting least privilege access rights, delivering data over an encrypted channel and shielding app(s) from direct internet access.
More complete solutions include in-line enforcement of user behavior analytics and activity logging. Google’s BeyondCorp and Netflix LISA are two showcase examples of these concepts in action.
Our approach to ZT/SASE addresses several of these core principles but we designed the Silo Web Isolation platform with one major difference.
When granting access we maintain a zero-trust posture towards the user’s device and browser -- which is particularly germane with the increase in unmanaged devices being used to access business applications.
If the sanctity of data is the ultimate objective, jumping the standard ZT/SASE hurdles to authenticate, authorize and access corporate data is necessary but insufficient to fully secure the environment. The risk boundary needs to include data exposure at all tiers; server, network and client.
Critically, IT is exposed and blind as users work from unmanaged devices where the machine’s integrity cannot be verified using endpoint management tools, and network traffic cannot be governed using a VPN.
In a complete ZT/SASE architecture, security and control should be maintained regardless of the accessing device. We designed Silo assuming a user is accessing sensitive data from a compromised device. With this as our center of gravity, our ZT/SASE approach casts a broader net over the end-to-end risks that organizations are facing.
To make this more specific, let’s take a look at how accessing applications through Silo meets and then extends the standard definition of the ZT/SASE architecture.
Using Silo to implement a device and location-independent security architecture
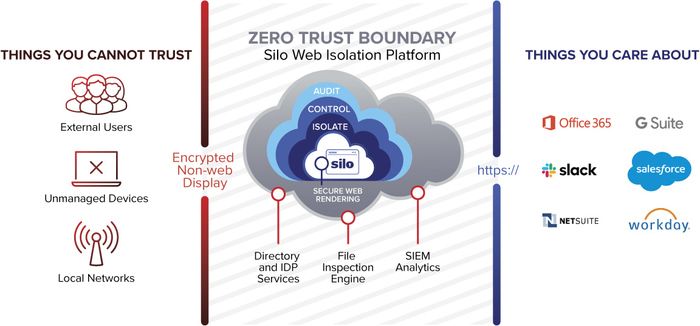
Reading the diagram from left to right, let’s consider a user accessing web-based applications (either SaaS or homegrown) from an untrusted location/network and an unmanaged device using the Silo Web Isolation Platform. The following capabilities are applied to achieve secure access:
Device identification and user authentication:
Users are required to perform authentication explicitly or via federation with the customer’s identity provider (IdP), and can be augmented with multi-factor methods by policy. Silo performs device identification to differentiate trusted from unmanaged machines and adjusts policy accordingly.
Isolated workspace:
When accessing a cloud service through Silo, all content is executed within an isolated environment in the cloud, air-gapped from untrusted devices, browsers and third-party web content that could compromise sensitive data.
Role-based provisioning:
Silo’s configuration flexibility allows narrow aperture access to only administrator-provisioned cloud services within the isolated workspace. Services and authentication credentials are provisioned directly, or via federation with the customer’s IdP.
Segmented access:
Silo eliminates the need for full access to the internal environment and network to deliver corporate applications externally. Unlike a VPN, Silo operates at the app layer and reduces the possibility of accessing internal systems over other ports and protocols.
Application shielding:
1st party services sitting on-premise or within IaaS environments are not directly discoverable or accessible over the public internet. Access is restricted to only the Silo platform which eliminates direct attacks on the server, as well as client-based attacks from untrusted browsers.
Policy enforcement:
Silo sits in-line with the data path and can enforce policies to control user actions, including file transfer, clipboard actions, printing and more. These policies can be tied to device identity to flex based on a trusted versus an unmanaged machine.
End-to-end encryption:
Silo delivers all content using end-to-end encryption that can be configured to be resilient to man-in-the-middle attempts if users are accessing from hostile networks. What’s more, the traffic between the user and the isolated workspace is flattened to a simple non-web display protocol. Silo’s log data provides IT with full visibility without the need to perform SSL break/inspect across different traffic types.
Visibility and audit:
Silo captures and logs user actions against sensitive data to provide full audit records for security and compliance. Logs can be encrypted with customer-supplied keys and are retrievable via API to ensure full chain of custody.
As traditional perimeters dissolve and VPNs go the way of the dinosaur, organizations are increasingly considering ZT/SASE architectures to secure direct-to-cloud work. As you make this transition, incorporate workspace isolation into your decision criteria to ensure your security boundary spans the risk of compromised devices accessing your data. Omitting this component undermines your data security goals.
Silo can be deployed in a standalone manner, or it can be integrated with existing IT tools such as directory systems, IdPs, content inspection gateways and SIEM platforms. In my next post, I’ll look at how Silo can be paired with your IdP investment to deliver security through isolation in high-risk access scenarios.