In many companies, VPN has become a staple of the traditional IT security stack. Annually, mid-sized organizations (<5,000 employees) spend an average of $60 per user on VPN technology and maintenance. Not much longer though, it seems.
While VPN has been around for more than 20 years, it now looks as if its promises of secure and private web access have worn off - many of them unfulfilled. In the words of Patrick Sullivan, Global Director of Security at Akamai, we are witnessing The death of VPN.
In his article for SC Magazine, Sullivan proclaimed: “It’s time to say goodbye.”
Sullivan’s farewell to VPN sounds timely, and he is not alone. Organizations large and small have found a way to cut their VPN costs or eliminated them altogether. In the same step, they attained a level of secure and private web access that VPN has never been able to deliver. What happened?
They discovered cloud-based remote browser isolation, that’s what happened. Recent surveys prove: Companies who use a cloud browser delivered as-a-service offsite, such as Silo Cloud Browser by Authentic8, were able to reduce their VPN expenses to $0, as well as eliminate other “traditional” security spend.
The reason is simple. While VPN can make connecting with networks and resources more secure, the encrypted “tunnel” it provides across the web has been showing numerous cracks.
Not only has it proven to be quite unreliable; in larger organizations, VPN often also creates new risks. For an in-depth examination of VPN, check out our whitepaper VPN for Secure and Private Web Access? Think Again.
VPN’s problem is that it leaves the larger issue unsolved. Most security, privacy, and compliance violations online are browser-related. Regular web browsers, whether connecting through VPN or not, process and store code from the web on the local machine.
This opens the door for data leaks and exploits. Connecting to the wrong web page can result in malware and spyware infiltration or data exfiltration and de-anonymization by third parties - the very risks VPN users believe they don’t have to worry about.
To illustrate how VPN instilled this false sense of security and dispel the myths, we have created the VPN vs. Cloud Browser: At-a-Glance Comparison table below:
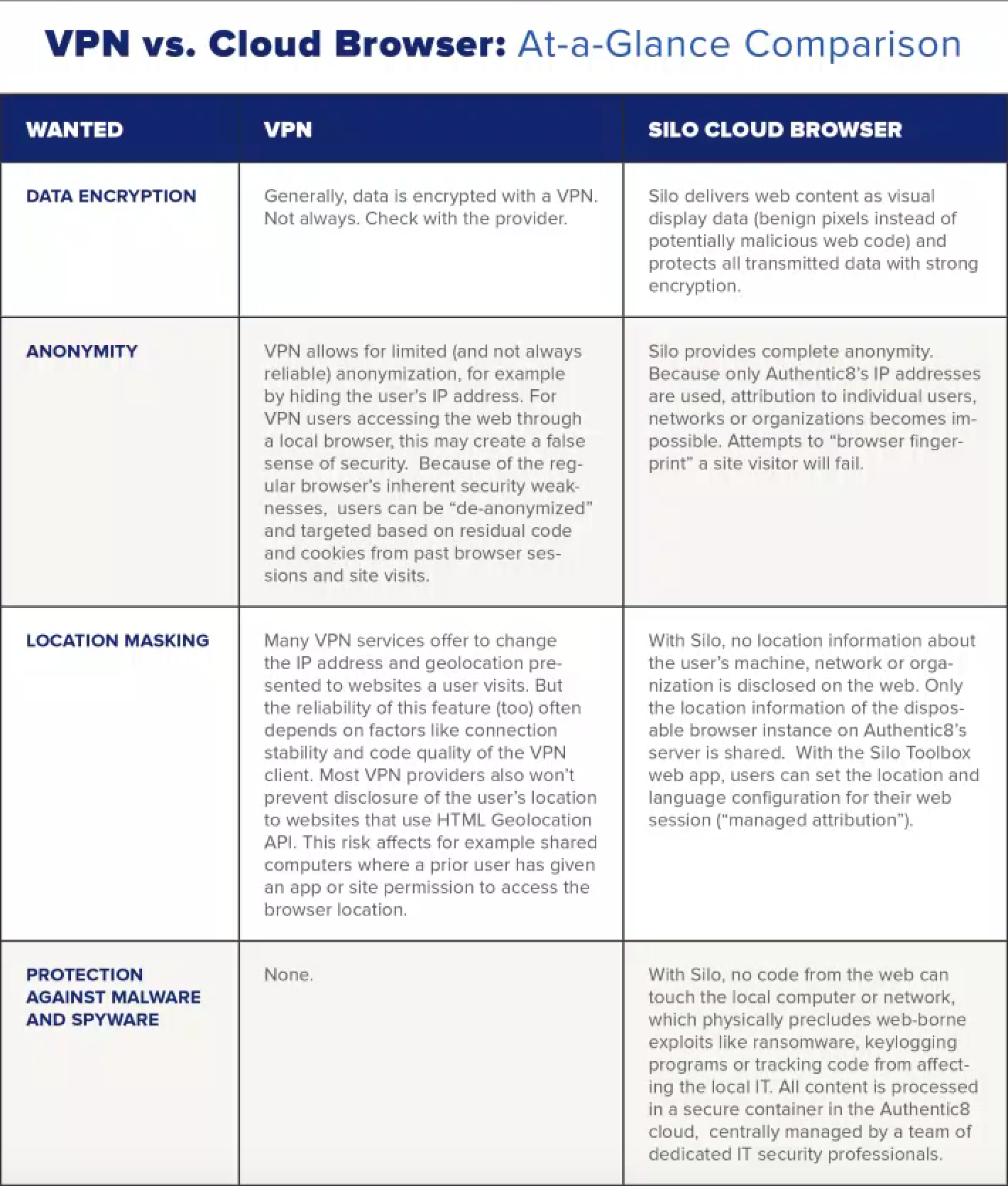
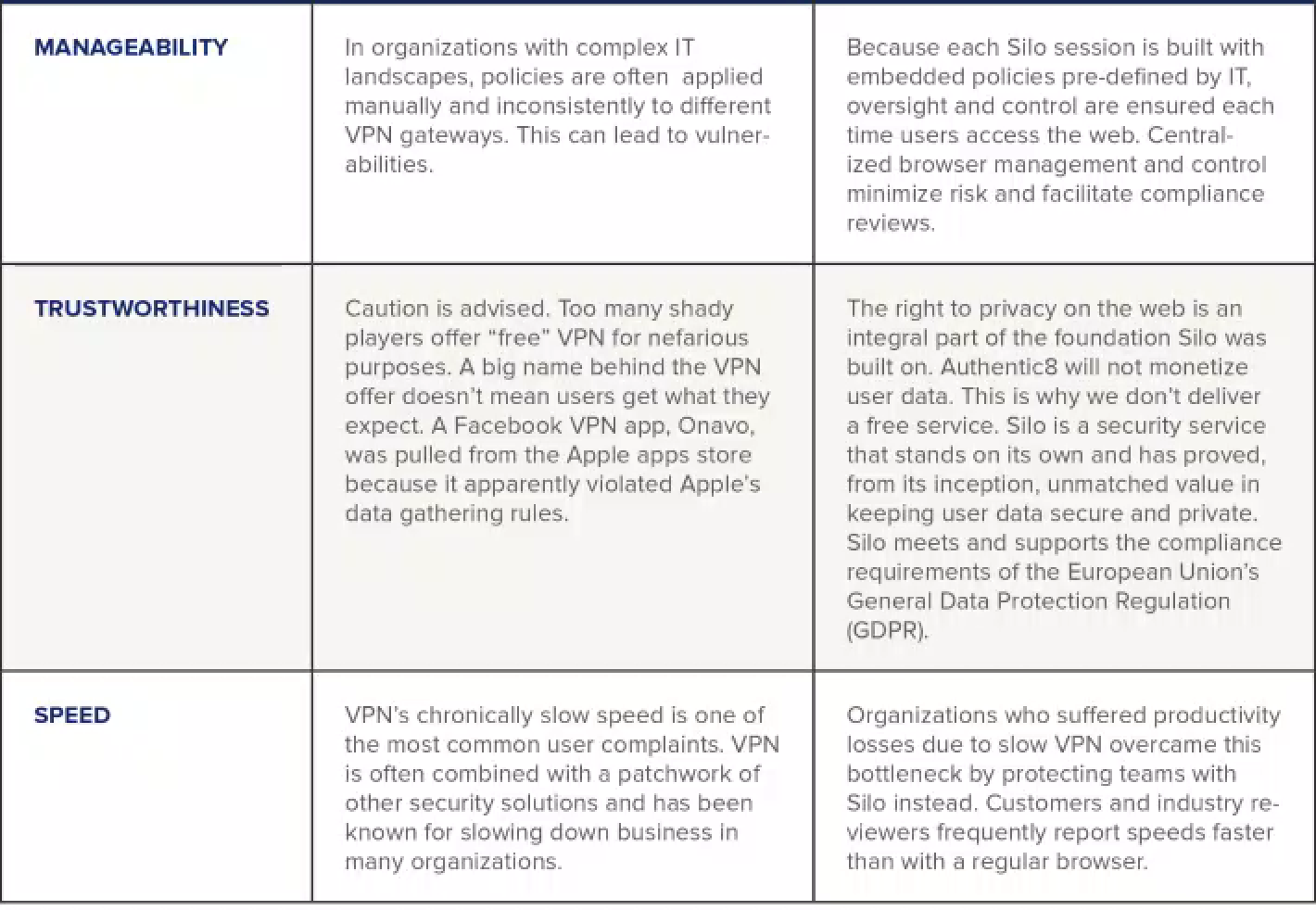
Source: Authentic8
This side-by-side comparison of VPN and the cloud browser approach to security and privacy online helps explain why major banks and investment houses, leading law firms, and more than 100 federal agencies now use Silo - and save money and labor on VPNs that are no longer needed.
Here’s how Silo works: Silo processes all web content remotely, isolated in a cloud container. Instead of web code, it transmits an encrypted display of the remote browser session back to the user.
The remote browser instance is built fresh at session start and destroyed at session end. It leaves no trace of the user’s web activities behind (such as cookies or residual code).
Using a secure cloud browser ensures that users remain safe, compliant, and anonymous online. Silo is centrally managed 24/7 by a team of dedicated IT security professionals.
Authentic8 does not monetize its solutions’ user data (many VPN services do). Because we value the privacy and trust of our customers, we store and process them only to the minimum required to provide the service.
VPN & Privacy: What Nobody Told You
VPN for Secure and Private Web Access? Think Again.
VPN: A Big Misunderstanding?