A new survey of financial crime analysts found that 90 percent believe their organizations should invest more in accelerating time-to-insight during investigations; and such investment should likely be targeted at open source intelligence (OSINT) gathering capabilities.
One of the main findings of the survey, conducted by Authentic8 and Association of Certified Financial Crime Specialists (ACFCS), was a reported decline or stagnation in investigators’ caseload productivity. Less than half (43 percent) reported that they were able to handle more cases than in the previous year. But within this group, a trend emerged: A majority (86 percent) indicated they are either heavily invested in OSINT capabilities or plan to do so.
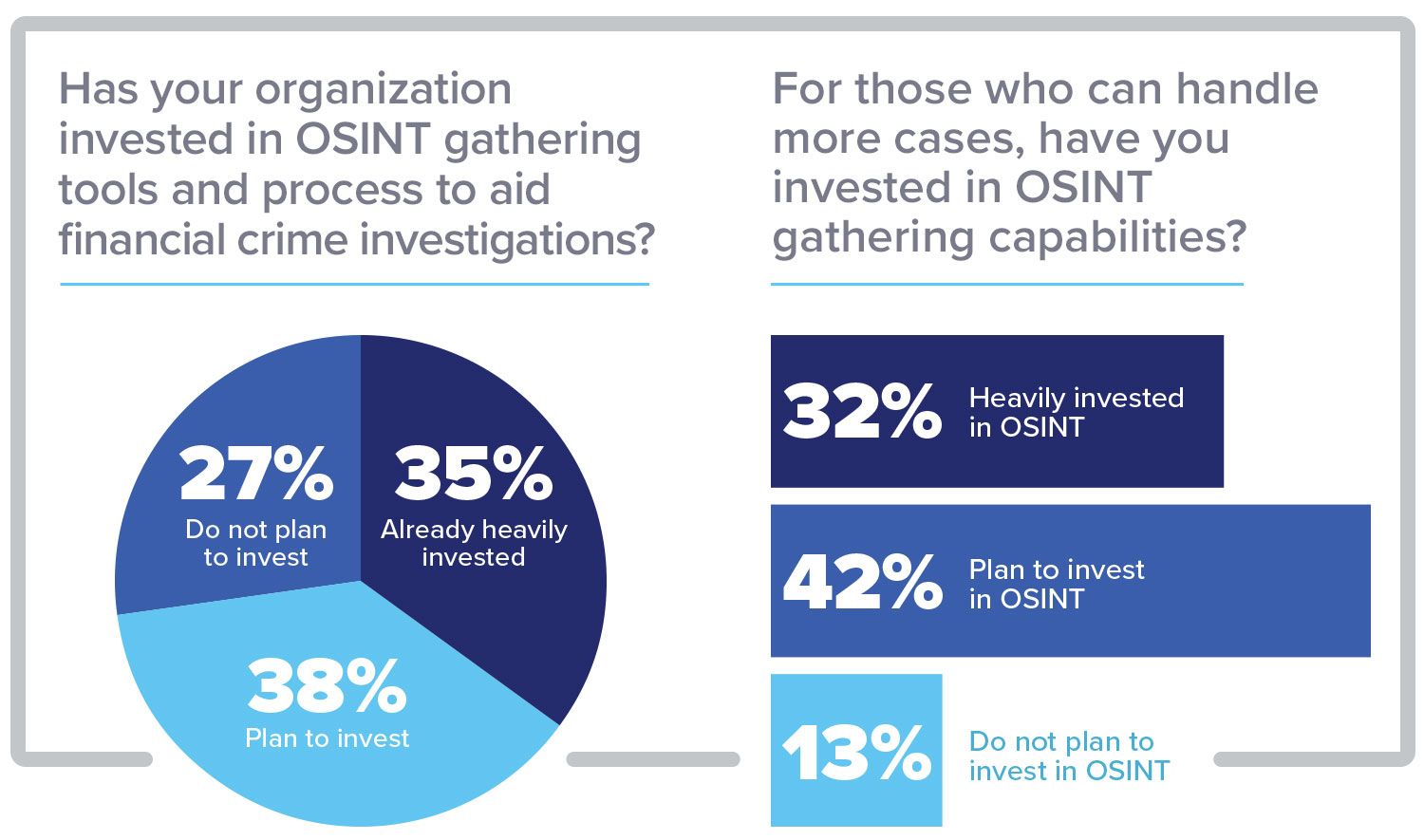
There is no single silver bullet, but investment in new OSINT gathering capabilities appears to be a strong enabler for investigator productivity.
And productivity should be a major concern for organizations attempting to tackle financial crime. Even if, like the majority of respondents in this survey, your firm is treading water in the number of cases it investigates year over year — let alone seeing that number decline — the gap between the incoming case count and the ability to handle it with current resources is widening. Organizations lacking efficiency in investigations put themselves at risk of monetary loss, compliance violations and prolonged exposure to threats.
So where can changes be made in investigative programs to improve OSINT gathering and caseload productivity? The first step is to understand the nature of typical investigations.
According to the survey, ad-hoc financial crime investigations can vary a lot, but in many cases they are quite complex. A good portion of respondents said their investigations are:
Understanding the scope of cases is critical to enabling the team’s productivity. Once scope is assessed, it’s important to analyze how analysts are able to conduct such investigations and where roadblocks lie.
Investigative work comes with unique requirements that are typically outside the boundaries of what an IT department is willing and able to support. Respondents highlighted a few areas that brought this home:
Enabling online anonymity, secure dark web access and access to specialized training are all factors in productivity that can be controlled by the organization. DIY isolation environments with “dirty” connections or machines can allow secure dark web access, though these can come with their own set of IT management and analyst workflow challenges (84 percent believe their organizations should invest more to reduce management overhead for IT related to investigations).
The issue of anonymity becomes even more critical in the dark web, and is still important during OSINT gathering in the open and deep web. Utilizing purpose-built solutions to manage investigators’ digital fingerprint (e.g., attribution) is one area of OSINT gathering investment that will reduce risk to the individual analyst as well as the organization. Maintaining anonymity/misattribution can also improve investigation efficiency so targets don’t realize they’re under investigation, potentially sending analysts back to square one.
Lastly, investing in specialized training for financial crime analysts, including the latest OSINT gathering techniques, can help improve the quality and quantity of work analysts are able to complete. Investigations require “humans in the loop” interactions — make sure your humans are the best equipped they can be.
Learn more. See how Silo for Research can help secure and improve productivity of financial crime investigations.