New Silo for Research feature provides Splunk integration for threat hunting and other online research, so enterprises maintain an investigation audit trail.
Any investigation that takes place today will at some point in time involve internet research and gathering open-source intelligence and information. Many analysts, investigators and researchers will start their investigation or research online, which can be a gold mine of information and critical to their mission. When trying to protect your enterprise, employees or customers — whether you are performing cyberthreat hunting or thwarting financial crime/fraud — open-source intelligence and publicly available information serve as key inputs.
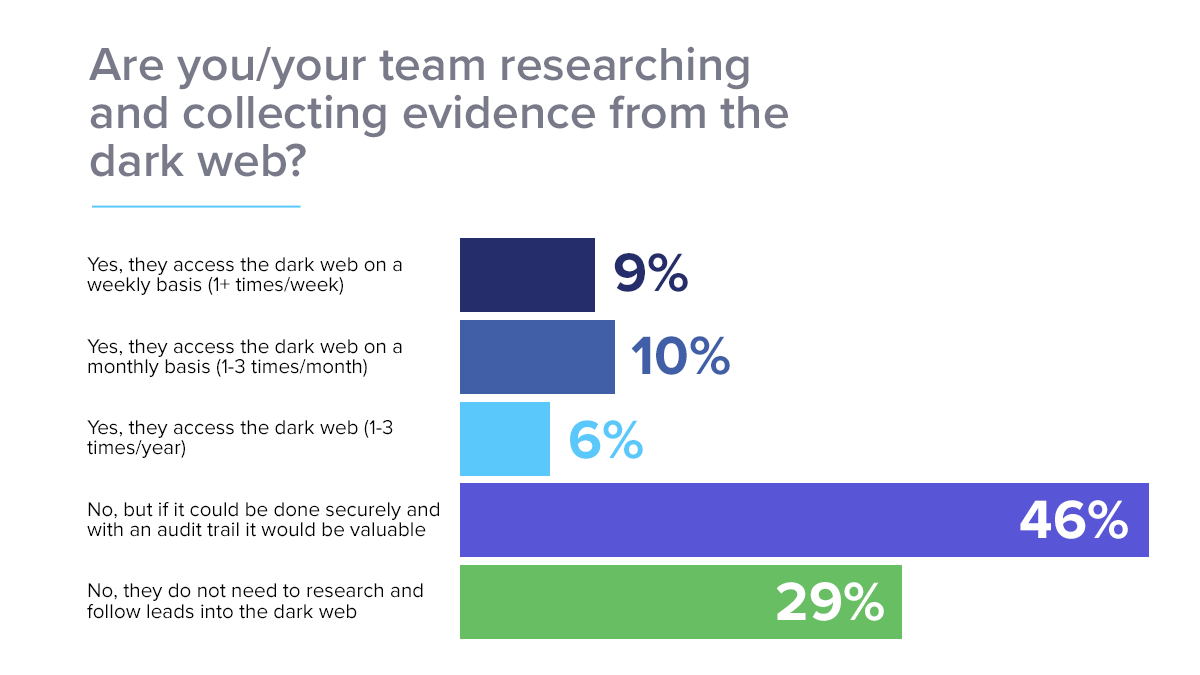
But conducting these investigations can be complex and risky for the researcher. Our recent survey report on financial crime investigations shows that more than 50 percent of such investigations need to visit websites hosted around the world in multiple countries. In additional findings, 25 percent of analysts access and perform research on the dark web — which is notoriously dangerous.
Making sure researchers and enterprise itself are safe and secure is of the utmost importance. This has led many enterprises to require investigators and analysts use personal or enterprise-supplied systems off the network — and without normal enterprise software — called “cold computers.” While this approach meets some security needs, it also causes problems for IT and risk management to track analyst activity, ensure it’s compliant with policy and maintain an audit trail.
The inability to maintain an audit trail for analysts can hinder research efforts, and many companies forbid their employees to research using technologies the organization doesn’t have visibility into or for which they’re unable to create an audit trail. Another finding of the above-mentioned report highlights this: 46 percent of analysts and enterprises would like to include dark web research in their investigations but are either not allowed to due to security concerns and/or the lack of an audit trail. Logging the required information is critical, but without easy access to the captured audit information, auditing itself isn’t very helpful.
Silo for Research solves these major challenges by protecting analysts from the dangers they might face on the surface or dark web, while allowing the enterprise to monitor the activities of analysts/investigators as they do their job, recording all web activity in a log.
Silo for Research provides the needed easy access to captured audit information. Once you have the data in hand, manipulation and monitoring of that data is the next step to make sure analysts aren’t doing things they shouldn’t — which could potentially compromise an investigation or make information inadmissible. The Splunk integration for threat hunting and other online investigations helps enterprises perform the needed monitoring and data manipulation of this information. It allows the SIEM team to set up granular log collection and indexing of Silo for Research’s user logs into the normal activity logs or into a separate, dedicated index for research activity (to make sure the information doesn’t cause noise for the SOC/IR team).
Get an overview and details of the “Authentic8 Silo Add-on for Splunk” on Splunkbase or by clicking on this link: https://splunkbase.splunk.com/app/5249/.