Elizabeth Denham.
If your company is doing business in Europe, put that name on top of the list of people you’ll not want to hear from in their official capacity.
Just ask BA (British Airways) or Marriott International. Both encountered data breaches that put millions of their customers at risk. Now, they’ve both received notice from Ms. Denham that they’ll be fined the record amounts of $ 230 million and $ 125 million, respectively, under the European Union’s General Data Protection Regulation (GDPR).
Elizabeth Denham heads up the Information Commissioner's Office (ICO) of the United Kingdom. Yes, the recipients of her notice of intent may appeal the decision. And no, observers don’t expect the ICO to reduce these first GDPR penalties against major international corporations to the proverbial slap on the wrist.
To the contrary. GDPR applies to all companies, including in the US, that store or process data of EU citizens and residents. The EU’s privacy commissioners (not only in the UK) who are tasked with enforcing GDPR mean business. And they are getting up to speed.
Under the regulation, which went into effect in May 2018, the EU’s privacy watchdogs have the power to fine violators up to EUR 20 million or 4% of a company's worldwide annual turnover. Remarkably, BA didn’t get a discount from the ICO for good post-data breach behavior (read: transparent and timely), which had been praised by experts.
So far, the record has been mixed. One year after it went into effect, GDPR is credited with moving companies to significantly improve their notification process, which has roughly doubled the numbers of self-reports. For the UK alone, Stephen Eckersley, head of enforcement at the ICO, predicted 36,000 data breach reports in 2019, up from 18,000 to 20,000 in 2018.
These numbers, as well as the EU Data Protection Board’s official report from February, indicate that more companies comply with the GDPR requirement to report data breaches within 72 hours, instead of leaving the victims in the dark.
Does the regulation actually generate a measurable preventative effect? The same numbers don’t boost confidence that it does - until we remind ourselves that the EU countries continue synchronizing and honing their GDPR enforcement approach.
So what’s coming next for GDPR violators? Our team in Europe expects the UK, Germany or France to move with more record-breaking enforcement actions soon. Following the British ICO’s announcements, the question is not so much if #GDPRogues will be able to shave off a million or two from the penalty.
No, the question now becomes: Who will be next to receive a record-setting letter from Ms. Denham, or Frau Block, or Madame Falque-Pierrotin? Let’s make an educated guess.
Following the enforcement actions against Google, BA and Marriott, violators will be facing off with empowered and patient bureaucrats who just love this new revenue source. They can - and will - make lack of compliance with EU regulations an expensive endeavor. Just ask Google, which got slapped with a first $ 57 million GDPR fine by the French data protection authority back in January (and, like BA, has appealed the decision).
Google has big coffers. What about other transnationals? US companies with subsidiaries in the UK who run afoul GDPR, for example, cannot hope to get saved by the bell, e.g., Britain’s impending #Brexit.
With tax revenues already diminished by companies leaving for the continental EU, the UK has made clear its intent to hold on to GDPR, including its stiff penalties, which go straight to the UK’s Treasury.
In our podcast GDPR in the US: After the British Airways Hack, we predicted that travel and hospitality companies were ripe for the picking.
This wager was a safe bet in a way, because the travel industry presented the lowest-hanging fruit for the ICO, given the industry-endemic low data protection standards in handling sensitive information of international travelers, including EU citizens and residents.
In the BA incident, self-reported by the company in September 2018, attackers exploited a third-party vulnerability in the airline’s digital supply chain. They took a path we had examined on this blog only a month earlier.
This time around, I’ll go out on a limb and make another prognostication.
The next headline-worthy penalty most likely will hit a global corporation for not sufficiently protecting its EU employee data. That’s in addition to Facebook, which already faces the possibility of getting slapped with a billion-dollar fine within the coming months.
Why would the privacy watchdogs home in on employee-related GDPR violations next?
It’s the next logical step. In asserting their reach, the EU authorities can drive home the point that GDPR doesn’t just cover the payment and booking data of consumers, like in the BA and Marriott cases, or platform usage, like with Facebook and Google.
Expect non-compliant cross-border handling of employee data to become the next focal point of GDPR enforcement. Transnational organizations with a significant headcount in the EU become vulnerable every time their US, Asia or Mideast-based headquarters or a European subsidiary touches workforce-related personal data with apps that are not GDPR-compliant.
This GDPR investigation commissioned by the Dutch government into Microsoft Offices telemetry mechanism may well be a harbinger of bigger things to come.
Investigators reported that the company’s US mothership was engaging in “large scale and covert collection of personal data" in Europe through Office's built-in telemetry capabilities.
Functional and diagnostics data of apps used by Dutch employees were only a small part of data exfiltrated to the US. The Microsoft GDPR breach documented in the Netherlands also included email subject lines and content processed with Microsoft’s translation and spell-checking tools.
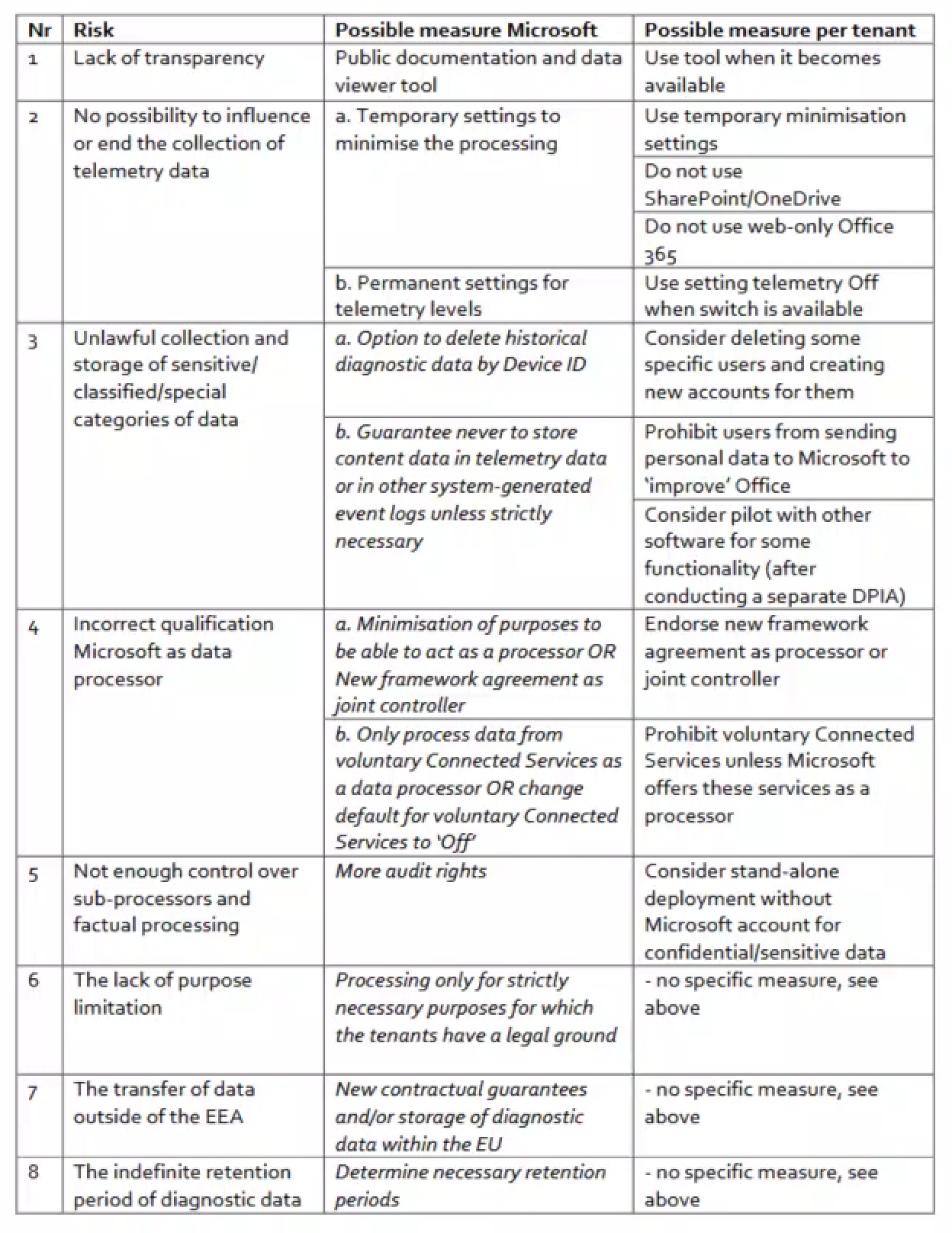
Source: SLM Microsoft Rijk
The German state of Hessia has since followed suit and banned Windows 10 and Office 365 from use in schools because of GDPR non-compliance. The Dutch and German findings underline that non-compliant software tools which touch employee or student data covered by GDPR will put the providers of such tools, as well as employers, in the crosshairs of EU data protection authorities.
This brings us to the primary tool used by employees and contractors to access resources online, including almost all relevant HR data: the locally installed browser. Close to 80% of data breaches are browser-related.
The “free” browsers still used in many globally active companies indiscriminately fetch and process executable code from the web on the local computer. This already makes them the primary attack vector for web-borne exploits, such as ransomware or spyware, which can compromise the corporate IT with disastrous consequences (as in BA’s case).
The Dutch government report can be read as a sign that browsers will soon come under the same intense scrutiny from EU privacy watchdogs as Microsoft’s Office package. The reason goes way beyond the traditional browser’s inherent security vulnerabilities, which have been known for years.
Critical from the GDPR perspective now proves that the old-style browser is also basically an anti-privacy tool.
By design, even with “Privacy” or “Incognito” mode enabled, such browsers constantly share privacy-relevant usage and user data with their makers and third parties - in other words, websites a person visits and advertisers on those sites.
Browser add-ons and extensions with backchannels to the developers compound the risk of security and privacy violations. The data leaks built into MS Office seem almost minor in comparison.
What does this mean for the browser under GDPR? Employers could be fined for browser-related privacy violations, for example as a result of HR accessing sensitive employee information through a regular browser.
The 2018 data breach at Australia-based HR services provider PageUp, which counted many US-based companies and universities among its clients, highlighted this risk. The HR field seems particularly vulnerable to attacks and data leaks - a point that is not lost on the EU’s privacy commissioners.
Not only does the use of locally installed “free” browsers as the primary means to access online resources at work expose employers to GDPR compliance risk. They also risk GDPR enforcement action whenever their EU employees use that same browser for personal web browsing, because employee privacy violations induced or facilitated by the work browser may not be covered by the personal web use contract common in many EU workplaces.*
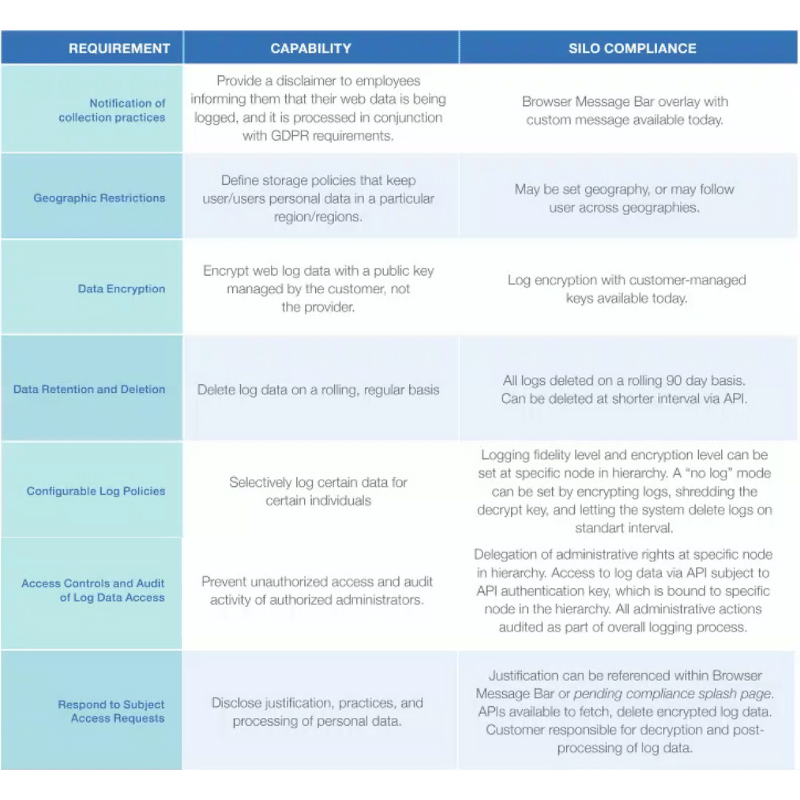
Source: Authentic8 GDPR Whitepaper
To be clear, so far, no company has been called out under GDPR for continued use of a traditional browser - yet. The MS Office investigation in the Netherlands may well have set the stage for that logical next step.
However, a clearer image will emerge over the coming months, with EU authorities working through their current backlog of GDPR investigations.
Authentic8 has monitored this process closely and will continue to do so because leveraging remote browser isolation with Silo Cloud Browser plays a role in how our customers prepare for GDPR.
Silo doesn't just provide maximum protection online. Web isolation with Silo also enables compliance managers to centrally access and manage all related data covered by GDPR. It
provides a compliant and secure framework for the related workflow in all instances where accessing or processing data covered by GDPR requires the use of a browser.
Authentic8 customers include many of America’s largest law firms with international offices, global financial services providers, and leading tech companies, among others.
Find out how Silo Cloud Browser will help your company brace for the next round of GDPR enforcement action in the EU. Ask for our GDPR Whitepaper and
* This assessment does not constitute and should not be read as legal advice. For legal advice regarding GDPR, US companies with customers, employees or contractors in Europe should contact a professional law firm with GDPR expertise.