While many cyberthreat intelligence teams rely on the traditional “Intelligence Cycle” or F3EAD models as they are defined, creating a customized, hybrid version of the two can be a better fit for the organization, their team and objectives.
There are many disciplines that collect, process and analyze information for different cyberthreat intelligence (CTI) purposes. In order to formalize and mature these disciplines, many practitioners and organizations use defined processes, frequently used in the U.S. Intelligence Community for purposes beyond cybersecurity. While these are common and defined processes, organizations may use variations to fit the particular needs of their tasks, workforce, etc.
Before creating a customized intelligence process, it’s best to learn the basic tenants of the established models — the Intelligence Cycle and F3EAD.
The U.S. government and military typically leverage one of two processes or a combination of both. The first is known as the ““Intelligence Cycle” made up of six steps:
The second process is known as “F3EAD,” shorthand for “Find, Fix, Finish, Exploit, Analyze and Disseminate.” Both of these processes have been around for a while, and for several years the former has been the basis of training for all intelligence analysts in the military.
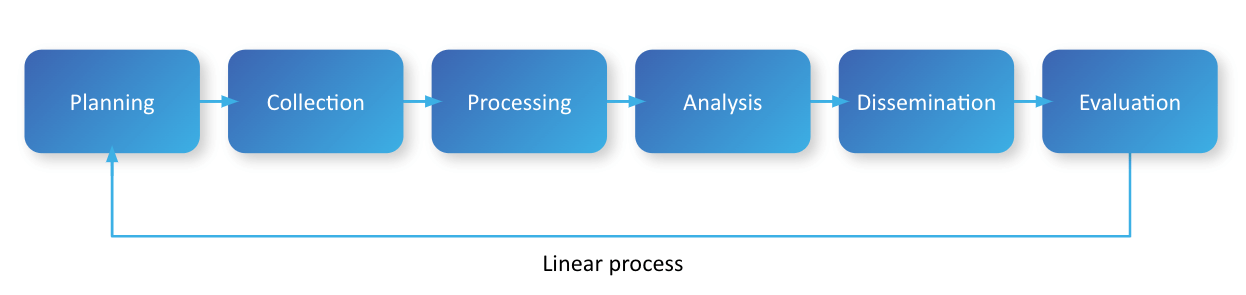
The formal Intelligence Cycle process
The Intelligence Cycle is a step-by-step process that is generally taught to be followed in order. This means that the members of the threat intelligence team begin by outlining the current threats to the environment; identifying intelligence gaps that need to be collected against; and create priority intelligence requirements (PIRs). These PIRs are used for the next phase in the cycle: Collection.
During Collection, the organization collects information based on the requirements identified during Planning and in accordance with the operations being conducted.
Once that information has been collected, the organization would move into Processing, where analysts look at all the information collected and evaluate that information based on the requirements set during Planning. All information that matches against those PIRs is kept, and any information that does not is disregarded by the organization. All kept information is collated based on the intelligence requirements to make it easier to analyze.
Next comes the Analysis step, where the raw information is turned into actionable intelligence that can be used. This could mean writing a formal report or the analyst creating an email with the pertinent information as well as an analyst comment based on the information collected and the analyst’s knowledge.
In Dissemination, the report or email is sent to the key stakeholders that need to be informed about the intelligence created to make a decision based on that intelligence.
Lastly, Evaluation takes another look at the intelligence and feedback from stakeholders. Evaluation is a chance for analysts to improve reports they have submitted.
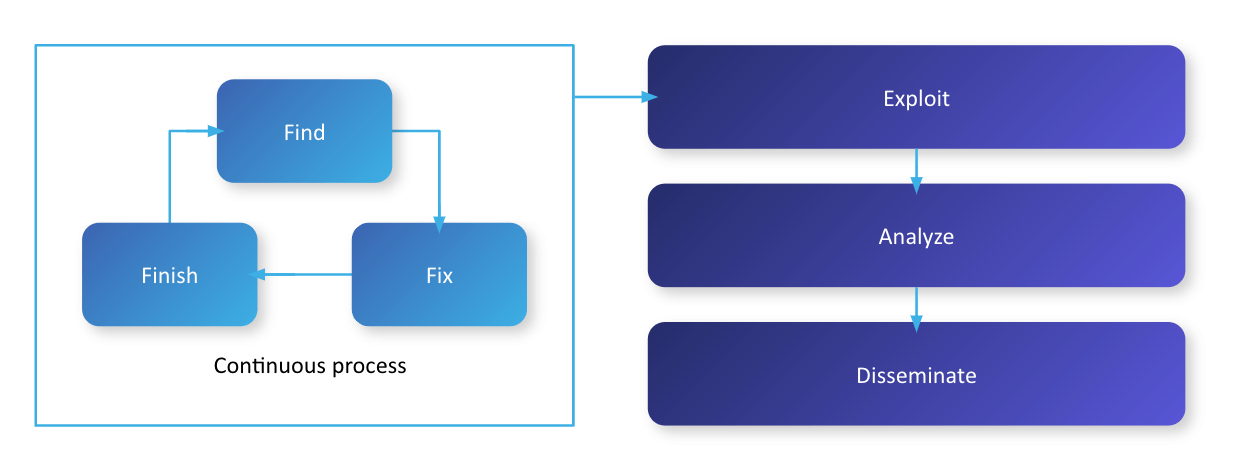
F3EAD contains the Find, Fix and Finish phases which form a continuous process
F3EAD was created by special operations forces’ intelligence teams and used in Iraq, Afghanistan and other areas where such forces are involved to provide the best information for the operations they conduct. F3EAD is used in the fast-paced world of special operations and is considered to be a deliberate way to target a defined threat.
This process differs from the Intelligence Cycle in that the entire process is an ongoing loop and is not conducted in a linear fashion.
F3EAD starts with the Find, Fix and Finish phase, where the organization finds a target, fixes its location and then captures or eradicates the target. If for some reason the organization failed to finish or locate the target, the process starts all over again at the Find/Fix phase of the cycle. The Find/Fix phase is a continuous operation, always looking for their current target set or a new target to Finish. If they are successful, the organization may find pertinent information, which they take with them to analyze, disseminate and start the process over. This means that the F3EAD cycle is a true, non-linear process that can start from any point and lead to the completion of an operation.
When the Intelligence Cycle and F3EAD were created, they were never intended to be used in cybersecurity. This is due to not only the different threats that organizations face in cybersecurity but the different priorities and requirements.
The Intelligence Cycle is nonetheless frequently used in cybersecurity, but with some challenges. It can cause threat intelligence programs to get stuck in creating a daily or weekly report that ultimately provides no significant impact to the decisions that need to be made by the organization.
To avoid this and other challenges, organizations should consider borrowing the best from each of the intelligence processes and creating a hybrid model of the two, specifically tailored for their cybersecurity operations.
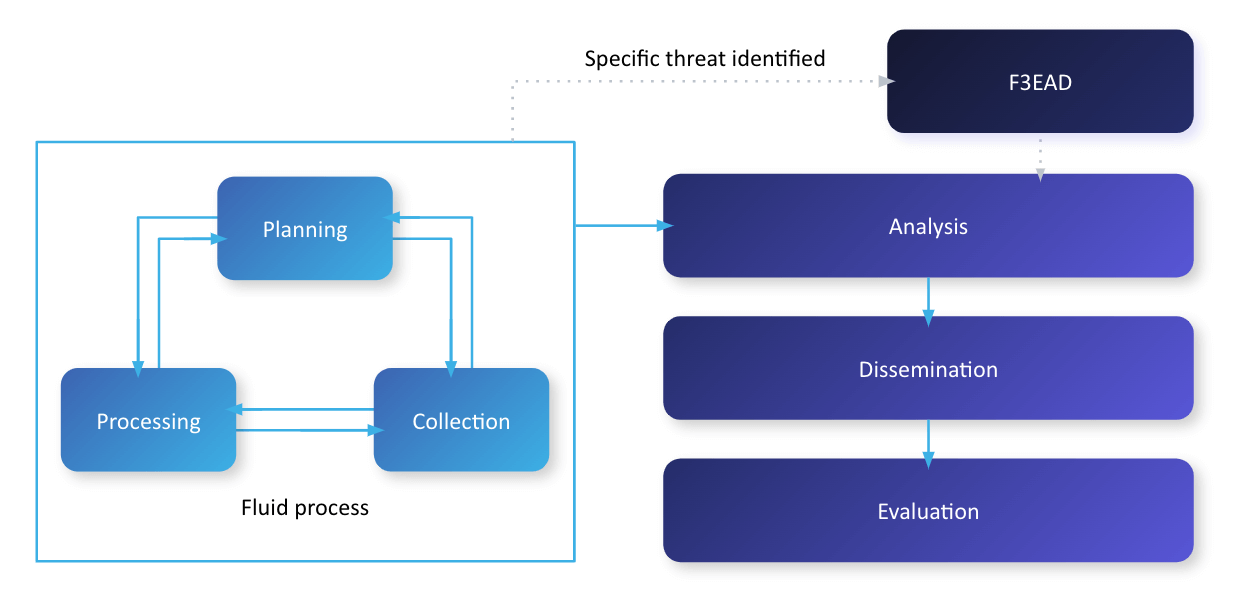
Example of a hybrid intelligence process combining the Intelligence Cycle and F3EAD models
Outlined below is a hybrid intelligence process that I’ve found useful in a particular organizational setting. It is not “the hybrid intelligence process” as organizations should build a formalized process that’s right for them, but it is an example of how such a customized process can be created.
As a general rule of thumb, the Intelligence Cycle is best applied against already created PIRs, while F3EAD is best applied to creating intelligence around specific threats.
This example of a hybrid model takes the tenants of the Intelligence Cycle but makes the first three steps (Planning, Collection, and Processing) a continuous cycle.
Under the hybrid model, the director of CTI or the manager of the CTI team should always be creating a plan and direction for the CTI directorate. This plan and direction would ensure that there are PIRs that would help drive the next step in the cycle: Collection. The PIRs are what would be used to implement a collection management plan to ensure information is collected to build actionable intelligence that can be consumed by the organization.
The Analysis step of the hybrid model also becomes an ongoing process, but not to the intensity as the previous steps, as it then falls to the CTI directorate to analyze the information and create relevant intelligence products (i.e., reports or other formalized communications). The number of products created and who they are disseminated to is something that is decided by the CTI director/manager and the chief information security officer (CISO).
To effectively make use of created intelligence products, the hybrid model should incorporate a quarterly meeting between the CTI director/manager, the CISO and the executive leadership team (ELT) of the organization and potentially the board of directors (if applicable) to provide:
The last step of the hybrid process is Evaluation, where feedback is requested. Feedback or reevaluation is extremely important from not only the main stakeholders but also from the ELT and board of directors, so that the best products can be put forward. Maintaining the Evaluation step is also important if there are more questions on the threat to the organization that can be asked and answered in a timely manner.
The F3EAD process comes into play when a specific threat has been identified in the organization’s network or was in the organization’s network and warrants a forensic investigation. In forensic investigations, F3EAD could be used to look into how the threat penetrated the network; indicators of compromise; identification of any missing information; and tactics, techniques, and procedures (TTPs) used by the attackers.
The F3EAD process could be added right after the Analysis step if there was a discovery of pertinent information that could allow the CTI director the ability to identify a threat actor or cybercriminal that could be attacking the organization.
For organizations that have a CTI team or are thinking about building a CTI team, a formal intelligence process should be designed and implemented. Using the processes mentioned in this post, organizations will need to identify which elements are the best fit for their organization.
Some things that need to be considered are:
Additionally, there are other considerations like where the CTI team will be in the organization (e.g, the risk department, cybersecurity department or its own entity under and answering only to the CISO, the ELT and the board of directors).
By giving due thought to the unique factors of your organization, teams and the threats they deal with, you can construct a customized intelligence process that takes the best of established models, shape them to your specific needs and ultimately, respond better to threats.
Listen to NeedleStack's Know thyself, disguise thyself podcast episode for more tools you can integrate into your intelligence process workflow.
Authentic8 and Silo for Research can help organizations in the Collection step by providing a software-as-a-service (SaaS) Managed Attribution platform. A tool like Silo for Research can help analysts by keeping their research-related browsing separate from other online activities. It does this by creating a secure, isolated environment that is managed by policy, providing protection and oversight at every step of an investigation. Since all web activity is logged and encrypted for compliance purposes and to protect the chain of custody for evidence.
Silo for Research also offers advanced features, such as a global egress network, allowing analysts to customize how their location is seen by the browser and the owners of the websites that they visit. To assist analysts in blending in with local traffic, Silo for Research has numerous attribution options like the ability to customize their IP address, keyboard and language settings, time zone configuration and much more. Lastly, Silo for Research isolates the browser from the end-point so that an analyst can be protected from malicious threats that are on the Internet.
Learn more on our website.