The COVID-19 pandemic seems like a double whammy for financial crime investigators. While online fraud has skyrocketed, teams are still adapting to a remote work environment. A recent survey among Association of Certified Financial Crime Specialists (ACFCS) members asked: Are they appropriately equipped for their mission?
Financial institutions are on high alert as attacks on the industry spiked by 38% in February and March. In March, the Financial Crimes Enforcement Network (FinCEN) alerted institutions to “malicious and fraudulent transactions similar to those that occur in the wake of natural disasters” and warned them of increased scam activity.
Between January and February, the Federal Trade Commission (FTC) reported more than 52,000 cases of fraud that were related to COVID-19 and resulted in $38.6M of fraud loss. All of this puts additional pressure on the industry’s fraud analysts and investigators, while they struggle with the consequences of working from home.
Together with Authentic8, the Association of Certified Financial Crime Specialists (ACFCS) asked members who attended a recent webinar on dark web research if they felt sufficiently equipped to conduct their online investigations.
More than 500 cybersecurity leaders, investigators, and analysts responded. The collective answer: “No.”
The results indicate that most surveyed specialists lack the proper equipment to conduct critical investigations on the web securely and efficiently. The culprit is the web browser.
I found it remarkable that the primary tool financial crime specialists rely on for their investigative work on the web is putting their mission and their organizations at risk. There were three main takeaways from the survey:

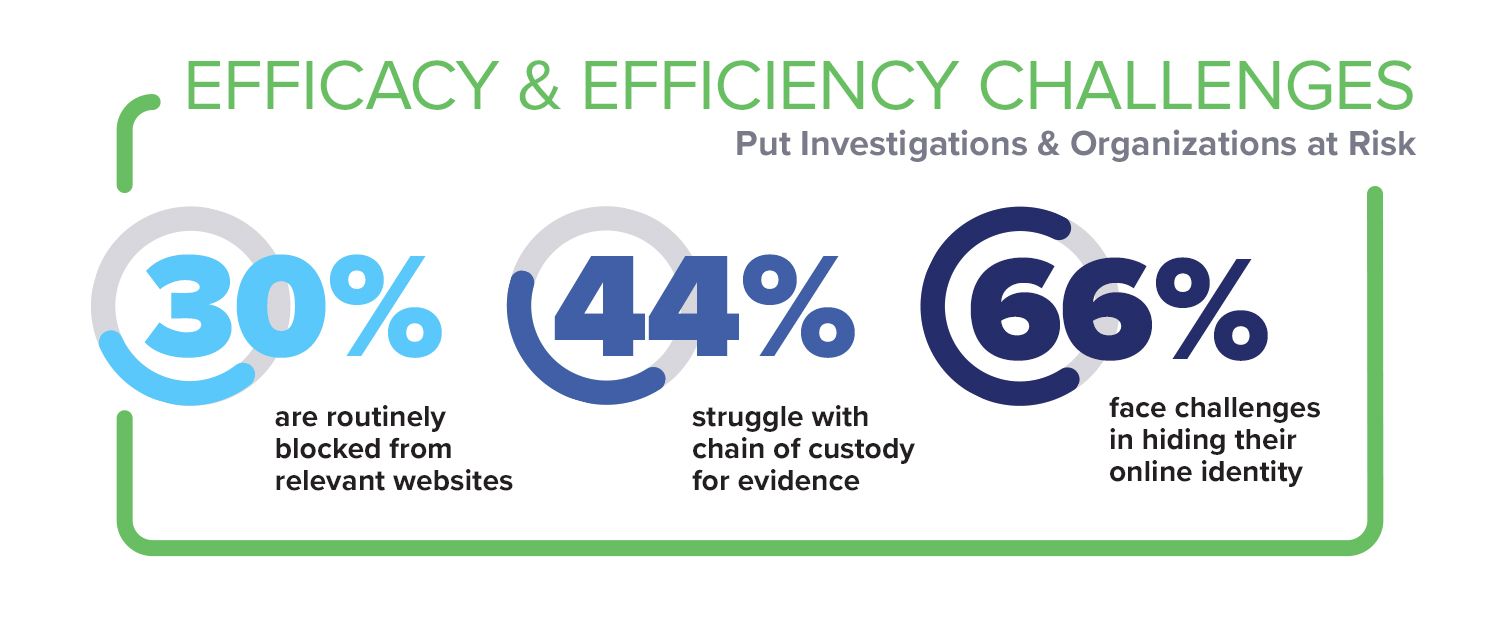

The most remarkable result of the survey was that not everyone claimed to face the above challenges. There was one cohort - those who used a cloud browser solution - who claimed to have much less “pain” than the rest.
The implication: There is a better way of doing things than using a local browser.
A cloud browser is a browser that runs on cloud-hosted servers. It executes all web code in a secure, isolated environment managed by policy, to provide protection and oversight. The end-user device receives a benign display stream, and end-users can interact via regular mouse and keyboard input. A concrete example of this is Silo for Research.
Silo for Research is a cloud browser-based product, built for the needs of investigators. Silo for Research combines web isolation with attribution management for secure, geographically distributed research and analysis.
Silo for Research can be configured to appear on the internet from one of dozens of global exit nodes and spoof different client environments. To the website under examination, the research framework presents itself as a regular browser launched on a local device on a local network.
Websites and social media platforms are presented only with the IP address of Authentic8’s server and cannot trace the network back to the end-user. This eliminates the risk of attribution or de-anonymization as the result of the web browser.
It is possible, but it is essential to recognize that different stakeholders have different outcomes they care about regarding an investigation. The good news is that a solution like Silo for Research can address the top priorities for multiple stakeholders.
With Silo for Research,
So yes, investigation outcomes can be measured - not only in lower IT costs and MTTR reduction but also in avoiding regulatory sanctions.
With Silo for Research, your firm will be able to conduct timely and thorough investigations (even when analysts work from home), file SARs quickly, maintain chain-of-custody and promptly produce documentation if compelled by regulators - without pushing IT to the brink.
Financial crime is on the rise. Pandemic-induced remote work is hampering investigations. Regulatory fines continue to grow in size. Does it make sense to roll the dice when it comes to equipping analysts and investigators with the tools they need?