Website attacks increased by 59% in 2018, according to the 2019 Website Security Report recently published by Scottsdale, AZ-based SiteLock, a provider of business website security solutions. Most of the attacks were automated, the company reports, with 330 bots staging on average 62 attacks per day.
So far, so not surprising - just wait, there’s more. Let’s look next at a significant aspect of the SiteLock findings. It illustrates how much the attackers behind such malware campaigns can rely on the inherent vulnerability of traditional browsers.
When someone visits an infected site, the regular browser dutifully executes the malicious code from the web on the local machine. From there, ransomware, spyware or cryptojackers can spread through the user’s corporate or home network. Game over.
“Not so fast,” you may object. “Our IT security team has many ways to prevent such exploits. AV/EPP/ATP, CASB, VPN, SWG/URL Filters …” Which brings up that other finding in the report - the one that should give us more pause.

Sourc: SiteLock
“Only 15% of malware-infected websites were blacklisted in 2018, which is a 4% decrease from the start of the year to the end,” according to the security researchers. This result is based on a total sample size of 6,056,969 sites, of which about 0.78% were found infected.
In other words, 85% of infected websites were not blacklisted. Mind you, many organizations today rely on a Secure Web Gateway (SGW) or URL filtering for blacklisting or whitelisting of some sort.
So what does this result mean for them?
It essentially means they are paying for a false sense of security. Roughly 42,200 of the sampled websites were ready to drop their nasty surprise gifts anyway, on any visitor unlucky enough to use a locally installed browser.
SiteLock extrapolates from the sample and concludes that 17.6 million websites worldwide were infected with malware “at any given time” in 2018.
With 85% of infected sites not blacklisted, we’re looking at almost 15 million exploit-infested sites (14,960,000 to be exact) that are ready to blast right through your perimeter defenses.
What should be the takeaway from the SiteLock report?
In organizations that rely on URL filtering to regulate web use and compensate for the security weaknesses of regular browsers, we think it may help open a few eyes to the bigger picture:
Question: Does this mean if you take away the gateway for exploits - locally installed browsers - the threat of website infections, inbound or outbound, becomes a non-issue?
Answer: Yes.
You don’t have to take my word for it. Customers who use Silo Cloud Browser, developed by Authentic8 and based on that approach, confirm it. They also report significant savings (more on that below).
Web isolation with Silo moves the browser offsite, outside your IT perimeter. All web content is processed in an isolated cloud container and transmitted back to the user through an encrypted connection as visual information. No code from the web can touch the endpoint.
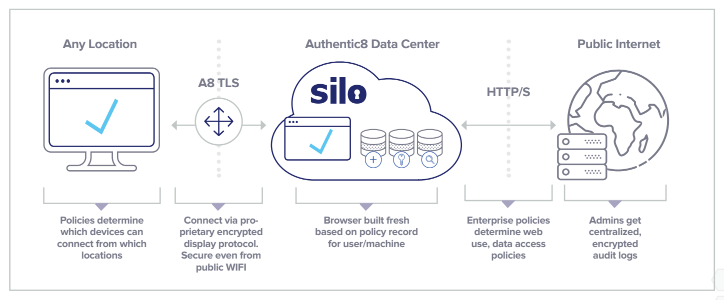
Web Isolation with Silo Cloud Browser
This makes it impossible for malware or spyware from infected websites to make its way onto your computer or corporate network. For each web session, a new browser instance is built from scratch in the cloud, which eliminates exploits and tracking based on persistent code. Websites can only see the IP address of Authentic8’s server. This ensures privacy, prevents de-anonymization, and eliminates the risk of targeted watering hole attacks through infected websites.
About those savings... - here’s a glimpse at what our customers say they save with Silo Cloud Browser over the tradional approach (read the complete overview here):
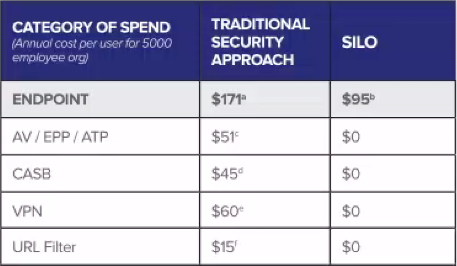
Web isolation with Silo enables our customers to stop spending on procurement and maintenance of pointless point solutions such as slow and vulnerable VPN services, ineffective AV tools - or useless URL filters that don’t catch 85% of infected sites.