Business email compromise pushes phishing attacks past the gates of email security solutions, and threat actors are using OSINT to glean everything they can to craft messages that will trick employees.
Business email compromise (BEC) is a subtype of spear-phishing attack, itself a sophisticated form of phishing — the practice of using fraudulent communications via email, voice or in-person to trick individuals into revealing sensitive information or taking harmful actions such as installing malware on their computing devices. Phishing, in turn, is a subset of social engineering (SE) attacks, which rely on manipulating human psychology to exploit them to do harmful actions against secure computerized systems without their intention (see Figure 1).
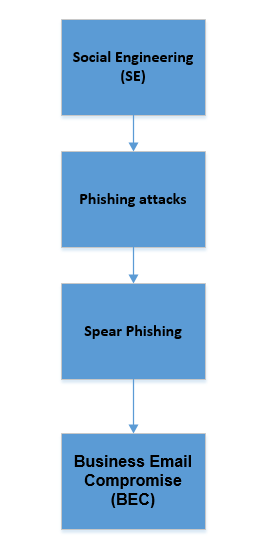
Figure 1 | BEC and its relation to SE attacks
BEC attacks are particularly harmful because they can circumvent traditional email security solutions, such as antimalware and antispam mechanisms. For instance, unlike other phishing attacks, BEC emails do not depend on malicious attachments or links to compromised websites as their attack vectors. Instead, they blend many social engineering tactics, impersonation and psychological manipulation to fool unsuspecting users into taking harmful actions. BEC attacks are mainly communicated via emails with text content only.
BEC attacks are increasing at a rapid pace and causing devastating commercial impacts to impacted companies worldwide. According to the FBI IC3 Internet Crime Report (2021, 2022 and 2023), BEC attacks racked up a staggering $2,946,830,270 in reported losses in 2023 alone, making them the second-costliest category of reported cyber crimes for the year.
BEC attacks generally involve impersonating executives or trusted business partners to trick unsuspecting employees (mainly in the financial department) into wiring funds to malicious actors. Last year, the BEC attack saw an alarming 38% surge, resulting in $4.57 billion in reported losses in the U.S. alone, securing the top spot in 2023's cybercrime rankings. To see the financial impact and prevalence of BEC attacks in all US states, you can check the interactive FBI IC3's State Report tool, which breaks down all types of reported crime data by state (see Figure 2).
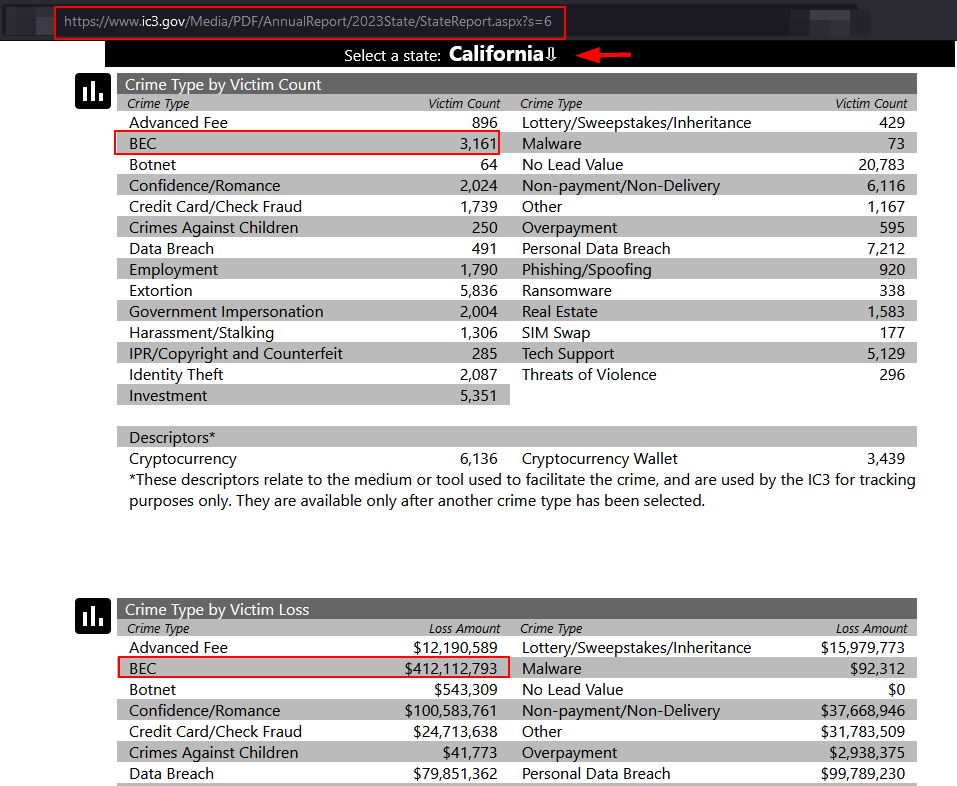
Figure 2 | the FBI IC3's State Report tool of reported crime types
How does advancing artificial intelligence (AI) technology increase BEC attacks?
The rapid advance of AI technologies, especially generative AI tools, will undoubtedly lead to intensifying SE attacks, specifically business email compromise. For instance, the accessibility of generative AI tools to the public will certainly allow abuse by threat actors through:
- Generating convincing phishing emails with the aid of text-generative AI tools such as ChatGP, Gemini and Notion AI — the last one is powered by the following three large language models: OpenAI, Cohere and Anthropic.
- Generating personal images to create fake profiles on social media websites. This continues further, as cybercriminals will create images and videos to fill up their fake profiles with content that makes it very hard to distinguish them from real ones.
- The most worrying aspect of leveraging AI tools in BEC attacks is using deepfake video and voice technologies. Deepfake AI tools can clone the voice of any human, in addition to cloning their face to a large extent, to create compelling counterfeit videos that can be used in live video conferences. Such attacks can be devastating and cause significant financial losses to companies. For example, in February 2024, the Hong Kong police reported a $25 million deep fake fraud. A fake CEO video call fooled a multinational company's finance employee. The unaware employee was invited to a conference video call with several other staff members. Ironically, all the staff members who appeared in the video call were generated using deepfake technology. The two most famous and free deepfake tools are DeepFaceLab and Swap Face.

Figure 3 | A fake photo of the North Korean leader generated using the DeepfakeLab tool; this tool is used for producing more than 95% of deepfake videos published across popular YouTube channels specializing in deepfake content
How BEC attacks work
Here is a breakdown of the main steps involved in a typical BEC attack:
Gather intelligence
The first step perpetrators take is to gather intelligence about their target personnel. To do this, they leverage open source intelligence (OSINT) tools and tactics to collect as much information about their targets, in addition to gathering intelligence on key personnel, organizational hierarchies and communication patterns within the targeted company to understand how to craft their fraudulent email without raising any doubts. For example, during the reconnaissance phase, threat actors leverage:
- Public sources: Include acquiring information about the target company's financial status, key business partners and organizational hierarchy. Examples of such repositories include:
- The Electronic Data Gathering, Analysis, and Retrieval System (EDGAR) (U.S.)
- Companies House (U.K.)
- European Union business register
- ZoomInfo (A database of 100 million company profiles, including their employee's email addresses and phone numbers)
- OpenCorporates (The largest website holding information about corporations in more than 140 jurisdictions)
- RocketReach (Find professional email addresses and associated mobile phone numbers.)
- Social media search: Social media websites provide a wealth of personal and business information about any individual. Each social media platform has a built-in search facility. Still, there are some online services and tools for simplifying finding information on these platforms more quickly, such as:
- Social Searcher: search for users, mentions, and trends across many social media platforms and on the web.
- Socialcatfish: a reverse phone lookup tool, you can also reverse search using the target user's email, username, name, and address.
- Peoplelooker: search for people using their name, email property, or phone number.
- Instant Username Search: a username search engine that helps you find all social media profiles of a particular username.
- Corporate websites: Companies' websites provide a rich source of information for phishers looking to craft targeted attacks. For instance, we can expect to find the following information when researching a target company profile:
- Employees' information, such as names, job titles and departments.
- Information about executives and leadership teams, including their personal images, LinkedIn profiles and sometimes their business email addresses and phone numbers.
- Links to company social media profiles can provide information about the company's culture, events, business partnerships and latest employee activities.
- Financial information — such as annual reports and financial statements — helps phishers craft customized emails relevant to a company's current financial activities, including its business partnerships with foreign suppliers. This information is crucial for crafting BEC attacks, as the most prevalent form of BEC attacks involves requesting wire transfers to foreign suppliers and business partners.
- Executing cyberattacks: Threat actors may try to execute cyberattacks, such as sending phishing emails containing malicious attachments or links to malicious websites to infect target user devices with malware (e.g., keylogger) to access their email accounts or other sensitive information.
Craft phishing email
After gathering reconnaissance on the target, attackers craft a customized message that could completely resemble the communication styles, formatting and email signatures of the impersonated individual, whether they be the CEO, CFO or a trusted vendor/supplier with whom the company has a business relationship. The BEC emails are generally directed to low-level employees working in finance or accounting departments to initiate wire transfers urgently or to reveal sensitive financial information that would be used later to begin the actual attack to steal the target company's money.
Attackers use different spoofing techniques to make the sender's email address look legitimate. These techniques include:
Name spoofing
The attackers use the impersonated entity name, such as the CFO name, in the sender field, although the actual email address differs.
Email spoofing
The attackers create an email address that resembles the impersonated individual's. For example, aubre0y@authentic8.com instead of aubrey@authenit8.com. As we noted, we added zero to the fake email address.
Domain spoofing
Attackers register domain names that closely resemble the entity they are impersonating. For example, send an email from finance@authentic88.com instead of finance@authentic8.com. Note how we used a spoofed domain name that is very close to the legitimate one to send the message from. This attack falls under typosquatting attacks.
Email header manipulation
Attackers may manipulate the email header message "Reply-To" field to conceal the sender's true origin. This allows attackers to make the email look like it originated from a legitimate sender.
Compromised accounts
In some cases, attackers may gain access to compromised email accounts in the target company. This allows them to send spoofing emails without worrying about employing any spoofing techniques.
Leverage social engineering tactics
The BEC email is carefully written to leverage many social engineering tactics and psychological manipulation to deceive the recipient into believing it. Here are some prevalent SE tactics used by hackers in BEC emails:
Urgent language
The BEC emails request taking immediate action, using phrases like "as soon as possible," "Please handle this urgently," "Failure to act could result in penalty fees" or warning of "limited opportunity deals" and heavy financial losses to create a sense of urgency. BEC emails will usually contain the reason why the requested action should be executed promptly, which also adds a sense of urgency to the request.
Confidentiality claims
BEC emails may state that the communication contains confidential information that should not be shared with other staff members. This prevents the victim from verifying the request and initiating fraudulent transactions.
Fear tactics
Threatening language like compliance fines, job termination or bounces can force the recipient to act promptly on the BEC email instructions.
Building trust over time
Successful BEC attacks often involve prolonged communications to gradually build trust with the target individual before convincing them to perform malicious actions.
As we have seen, BEC attacks are sophisticated phishing that relies on SE tactics to trick employees, commonly in finance departments, into transferring funds or revealing sensitive information. Attackers gather intelligence through OSINT, impersonate leadership teams or trusted partners and craft convincing emails using spoofing techniques. They leverage urgency, confidentiality claims and fear tactics to manipulate victims. BEC attacks bypass traditional email security solutions and have lost billions of dollars. With AI advancements, deepfakes and generated content can further enhance BEC attacks; this requires organizations to reinforce their cybersecurity defenses and, primarily, educate their employees about the BEC attack scheme.
We’ve seen how threat actors use OSINT to carry out BEC phishing attacks — learn how OSINT can help combat phishing websites >
Tags Cybersecurity Phishing/malware SOC

